Discover, prioritize, and remediate vulnerabilities, misconfigurations, identity,
and
data risks, across
multi-cloud environments.
-
Cloud-Native Vulnerability Mgmt. Get prioritized visibility into every cloud resource
from development to runtime. -
Enforce Least Privilege. Leverage the intuitive UI to attain the least privilege without disrupting productivity.
-
Automate Compliance. Eliminate audit fire drills. Verify and automatically
report on compliance frameworks.
Demo von Tenable Cloud Security anfordern
Außergewöhnliche, einheitliche Cloud-Sicherheit erwartet Sie!
We'll show you exactly how Tenable Cloud Security helps you deliver
multi-cloud asset discovery, prioritized risk assessments and
automated compliance/audit
reports.
Join 40,000+ organizations automating their cloud security with the leading independent provider


Cloud-Sicherheit – passend zu Ihrem individuellen Weg
Get full visibility across AWS, Azure, GCP, and Oracle Cloud Infrastructure (OCI) with 100% agentless scanning. Continuously discover your cloud environment across infrastructure, workloads, identities, and data, powerfully visualizing all your cloud assets. Obtain a unified view that simplifies your team’s understanding of even the most complex issues.
Try for free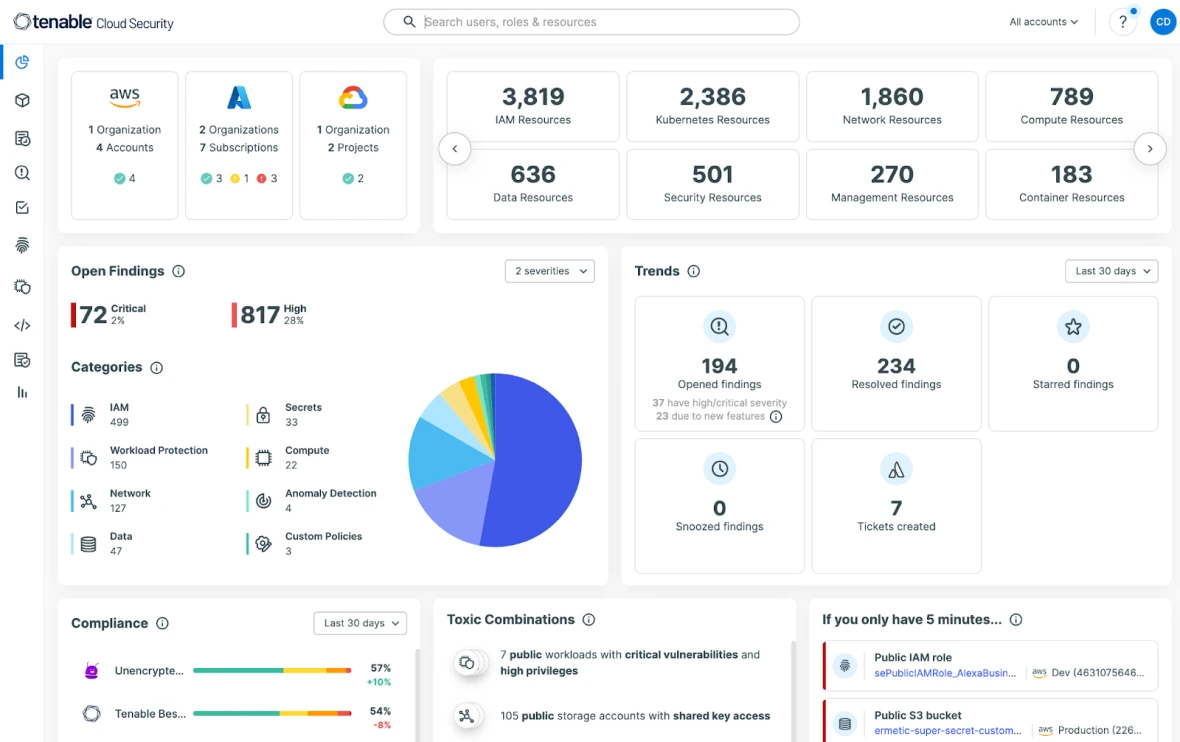
Überwachen Sie Risiken durch die kontinuierliche Überprüfung und Bewertung von Einstellungen und Konfigurationen in der Cloud-Umgebung. Durch den Abgleich aufgedeckter Risiken mit Sicherheitsstandards und -richtlinien können Sie Compliance erzielen und aufrechterhalten und Audits in Multi-Cloud-Umgebungen mühelos bewältigen. Profitieren Sie von vorgefertigten Berichten für über 20 Compliance-Frameworks, darunter SOC-2, GDPR, PCI DSS, HIPAA, NYDFS und andere.
Try for free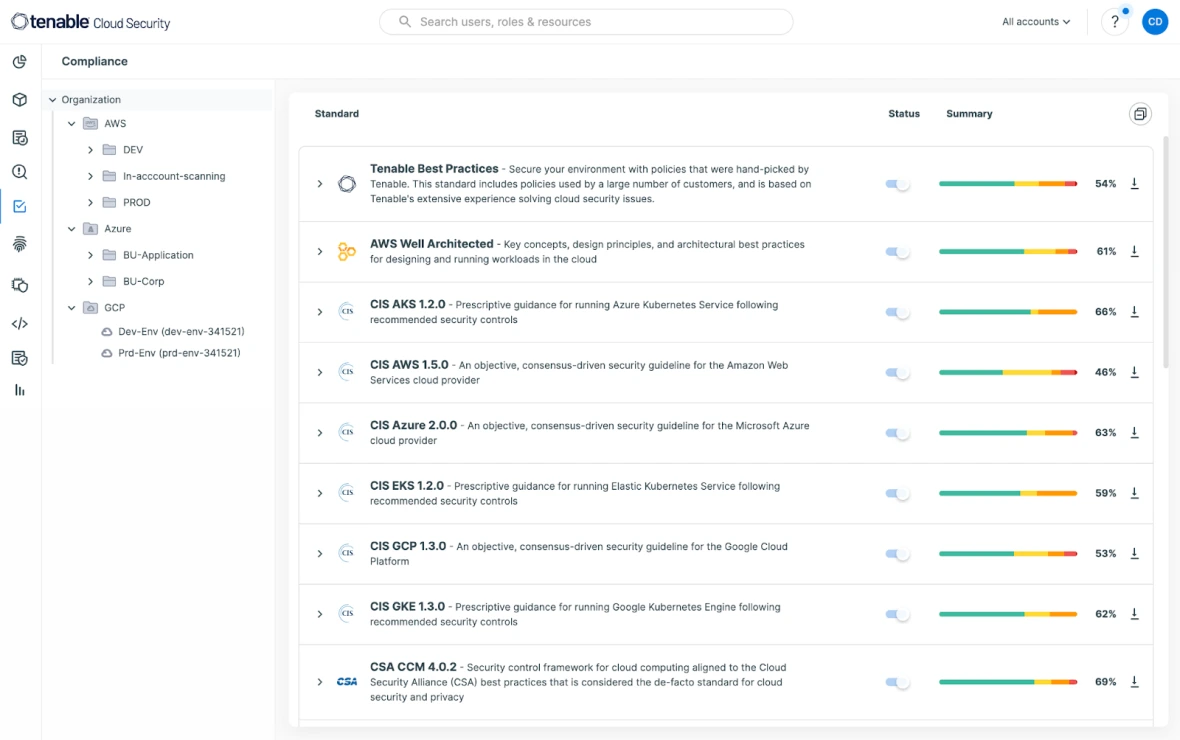
Tenable is a cloud security solution that allows you to focus on the risks that matter most. Tenable Cloud Security gives users deeply prioritized findings that empower Security and DevSecOps teams to automate threat detection and remediation efforts at scale. Mitigate and remediate risky privileges and faulty configurations using auto-generated and customizable policies by seamlessly integrating across ticketing, CI/CD pipelines, IaC, and other workflows.
Try for free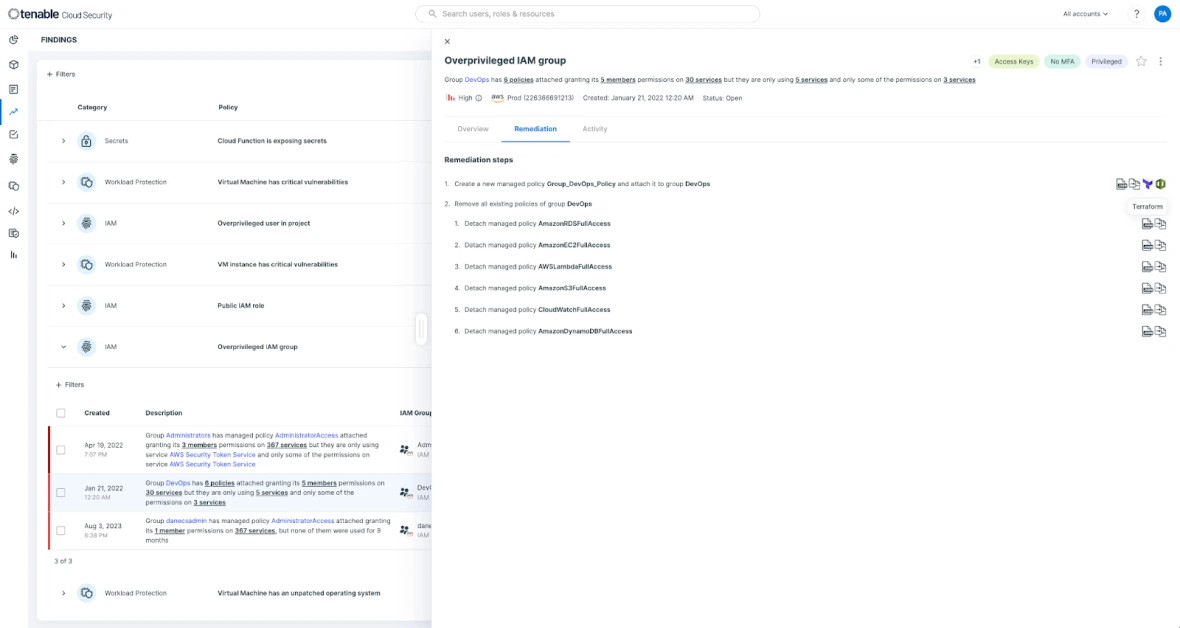
Erkennen Sie anormale und verdächtige Aktivitäten, indem Sie Risiken kontinuierlich anhand von Verhaltens-Baselines bewerten. Analyze cloud provider logs and link cloud threats with underlying architecture to show the context associated with each risk quickly.
Try for free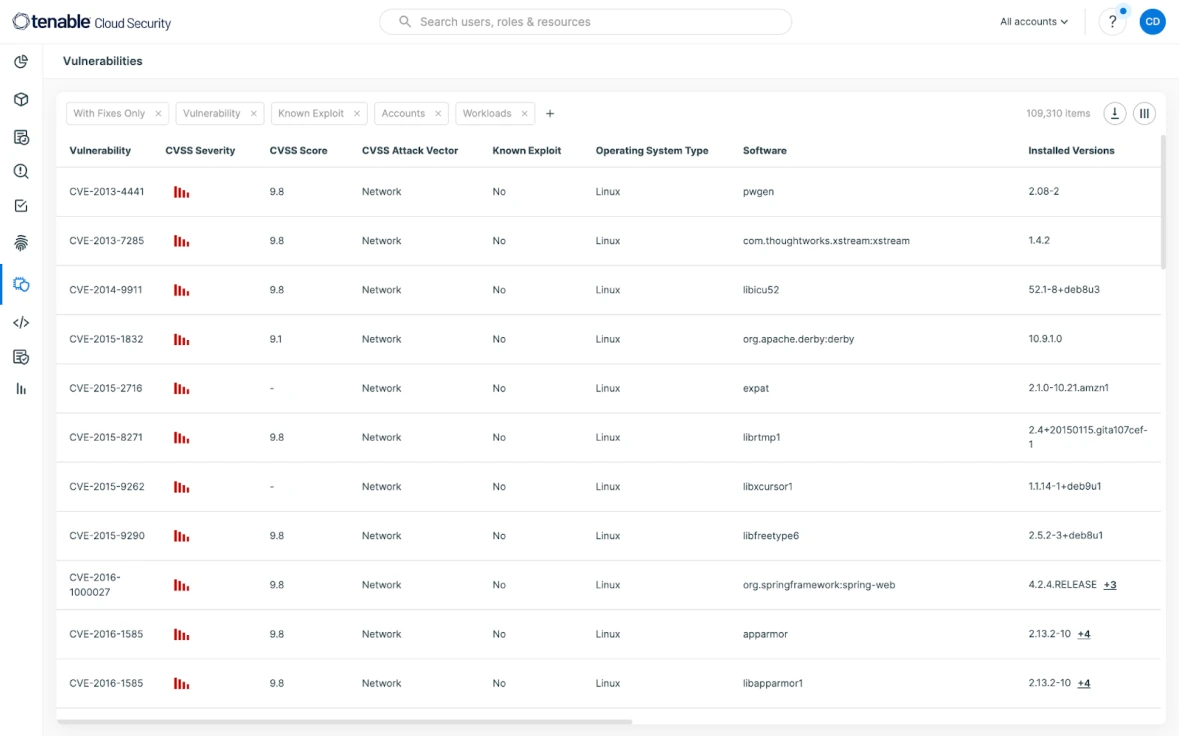
Build zero trust in your cloud security infrastructure. Minimieren Sie übermäßige Berechtigungen für Dienste und Personen, ohne irgendetwas zu beeinträchtigen. Der Weg zur Umsetzung von Least Privilege beginnt mit einer umfassenden und genauen Übersicht über alle Berechtigungen. Continuously discover all entities and policies (including IAM, resource, permissions boundaries, and ACLs) in the environment and analyze the relationships to reveal the gap between desired enterprise policy and actual entitlements.
Try for free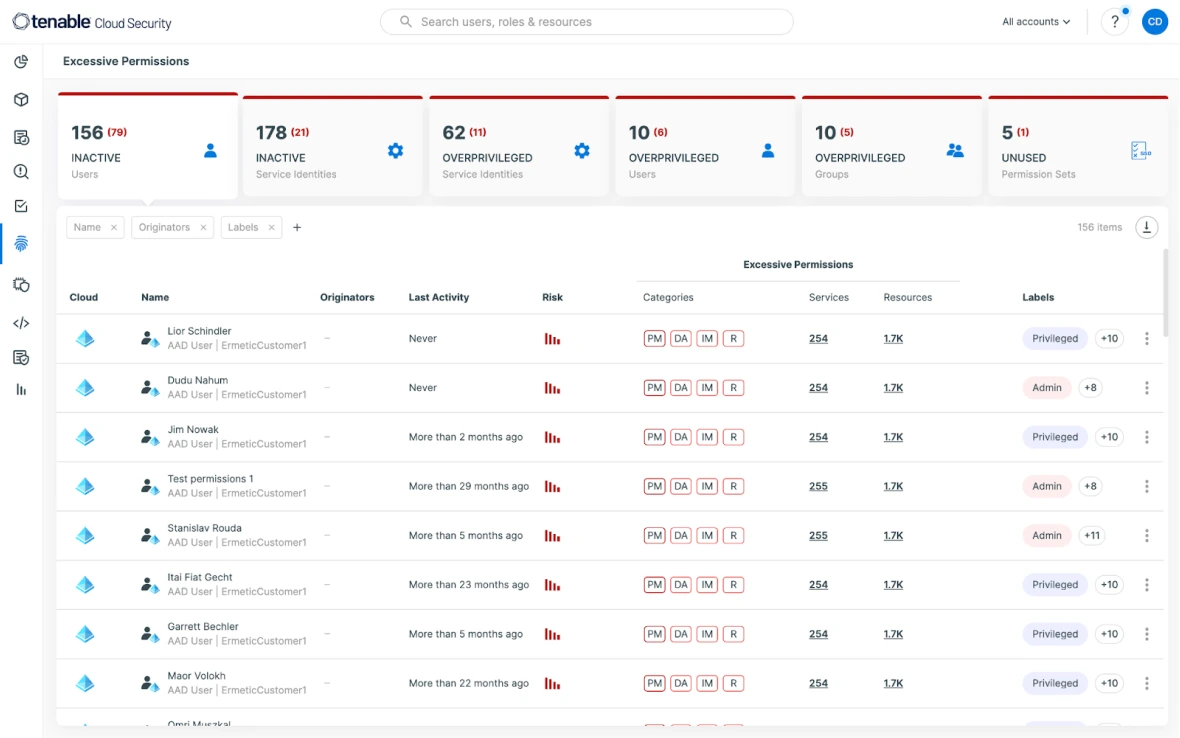









Informieren Sie sich in diesem E-Book über:
- How to protect workloads and manage vulnerabilities
- Securing identities and entitlements and enforcing least privilege
- Ways to accelerate cloud detection and response
- How to assess and prioritize risk across cloud environments




