A Role-Based Look at How Splunk Mission Control and Tenable Can Streamline Your Risk-Based Vulnerability Management Program

The new, exclusive integration between Tenable.io and Splunk Mission Control enables security teams to consolidate vulnerability insights and expedite their remediation efforts.
It's no surprise that the attack surface becomes increasingly complex when managing hybrid and cloud environments. The harsh reality is the more assets you have in your infrastructure, the more difficult it is to manage security events and alerts from your disparate security tools. Security teams often spend too much time consolidating and prioritizing alerts, when they could be using their limited time and resources to take actionable steps towards remediation. But there is still hope for security teams to help keep track of these various security events.
Recently, we launched our exciting new integration between Tenable.io and Splunk Mission Control that helps security teams streamline their risk-based vulnerability management program and expedite remediation efforts. The Tenable® Plugin for Splunk Mission Control features:
- Tenable as the only risk-based VM partner to integrate with Splunk’s new Unified Security Operations Platform
- A comprehensive dashboard that consolidates all critical vulnerabilities for a given Notable Event
- Tenable’s proprietary Vulnerability Priority Rating (VPR) which isolates the 3% of threats that pose the greatest actual risk to your business
In this blog, we’ll look at how the integration can help security teams at all levels of the organization, from analysts and security operations center (SOC) managers on the front lines to CISOs in the corner office. Taking this ground-up approach, we’ll aim to understand the daily challenges and goals for each position, while looking at how this new integration alleviates those key problems in different ways.
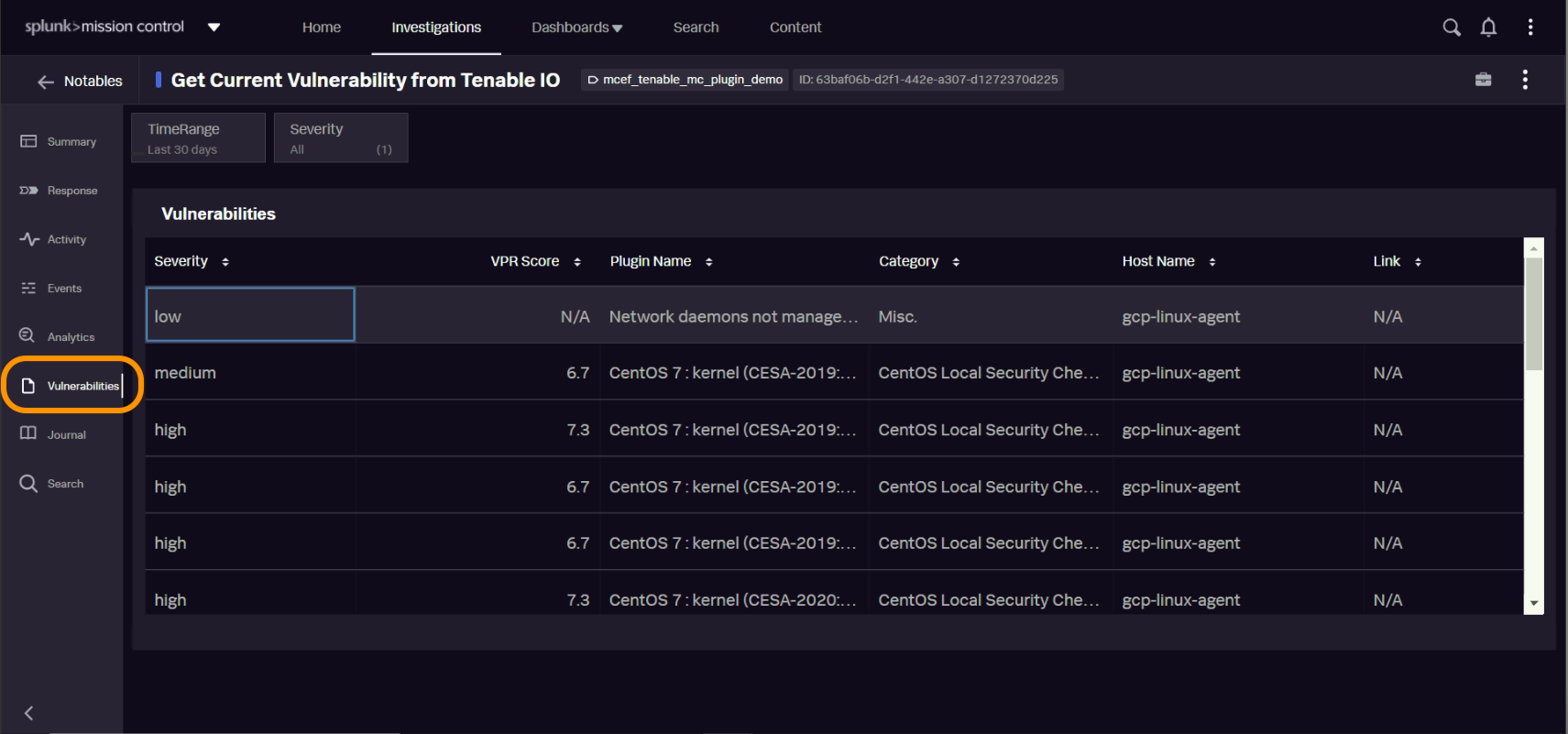 Security teams can view and organize vulnerabilities by severity or VPR score within their Splunk Mission Control dashboard.
Security teams can view and organize vulnerabilities by severity or VPR score within their Splunk Mission Control dashboard.
Security analysts: Consolidated events help prioritize remediation efforts
Security analysts have an “in the trenches” view of all the security tools, alerts and environments needed to protect modern organizations. To say that they are busy hopping from one security platform to the next is at best an understatement. On any given day, they might find themselves triaging security events, coordinating with team members across multiple workflows, and ultimately deciding which vulnerabilities are critical and require urgent remediation. Searching, correlating and coordinating security events take up most of analysts’ time, when in reality this work could be done in a more efficient manner. Consolidation is key to making life easier for security analysts, and having one place to view all alerts is half the battle.
The Tenable plug-in for Splunk Mission Control consolidates this work and provides security analysts with a central view to easily monitor vulnerability context for a given Notable Event — including VPR and severity rating — and use that context to make more informed decisions about which actions to prioritize. By providing analysts with a single, risk-based view of key vulnerability data, they can focus their efforts on remediation activities rather than the tedious effort of jumping back and forth between different applications and data sets.
SOC managers: Vulnerability insights align resources with critical threats
Analyst groups typically report into the SOC manager, who is responsible for managing the team’s daily operations and determining the optimal resource alignment. This not only means managing the workload, but ensuring that your team can move quickly even when dealing with disparate security tools that require complex workflows. The goal of the SOC manager is to streamline and orchestrate these workflows and make sure the team is focused on remediating the right security events.
To help alleviate these challenges, Splunk’s Mission Control framework enables security partners like Tenable to integrate with their key workflows. The SOC manager can optimize team resources by combining Tenable’s vulnerability insights into key parts of Splunk’s unified workflow, eliminating confusion about which vulnerabilities are most critical and enhancing team efficiency when executing steps to remediate.
CISOs: High-level metrics to report on security progress
While analysts and SOC managers contend with the daily flow of security alerts, the chief information security officer (CISO) is tasked with managing the overall security strategy for the organization. The CISO’s role is multi-faceted, and one of its broad mandates is to communicate the team’s effectiveness and efficiency to the board and other leaders within the organization.
With the integration between Tenable and Splunk Mission Control, CISOs now have an extensive dashboard that provides both Tenable’s vulnerability insights as well as a high-level synopsis of the organization’s security progress. CISOs and other security leaders can use this dashboard to monitor daily metrics such as total, active and fixed vulnerabilities. This dashboard also informs stakeholders about the 10 most critical vulnerabilities and their associated hosts at any point in time, which helps security teams determine which vulnerabilities they need to tackle first to reduce their overall cyber risk.
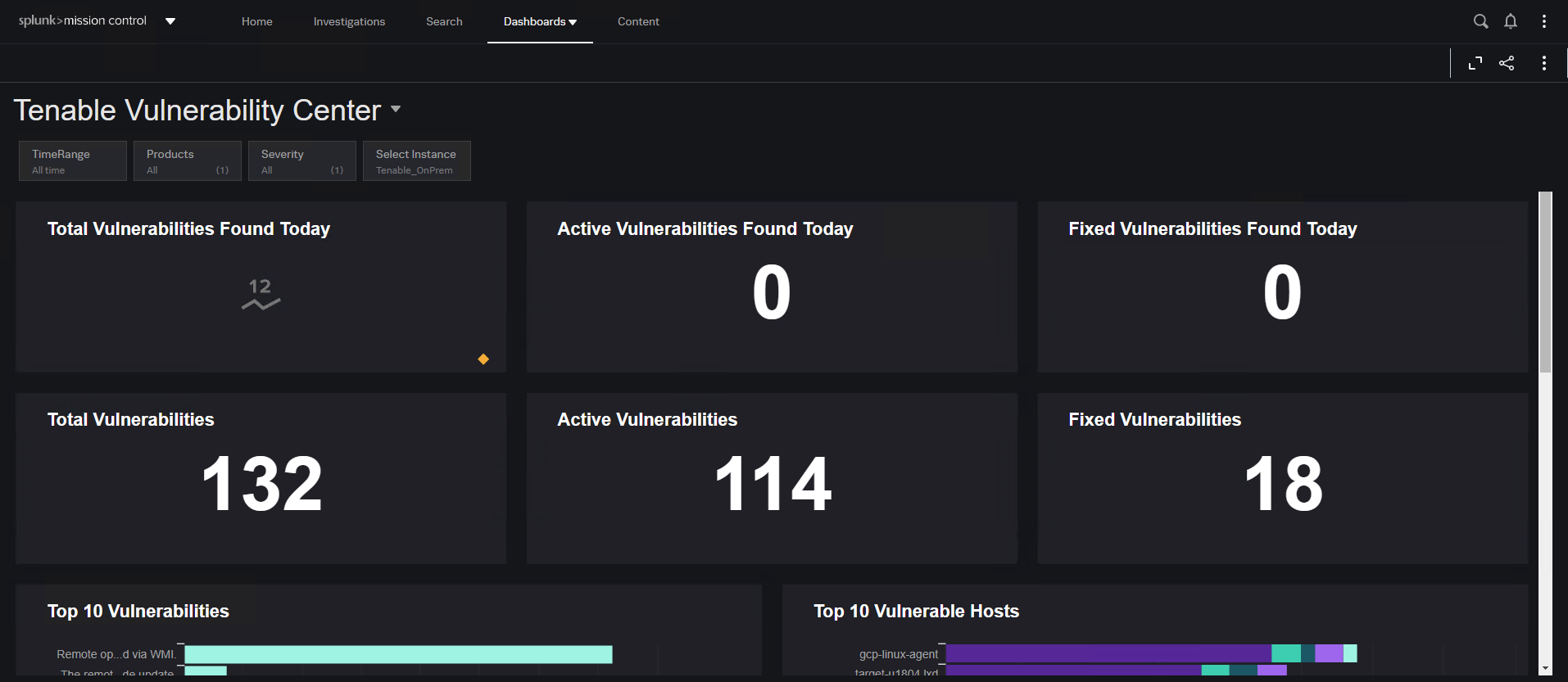
This Splunk Mission Control dashboard, powered by Tenable, is a simple, intuitive and powerful way for CISOs to monitor and communicate the overall efficiency and effectiveness of their security program.
Get started with a unified view of your attack surface
The integration between Tenable and Splunk Mission Control influences security personnel at every level of the organization, from the CISO down to the front-line security analysts. But at the end of the day, the common denominator between these roles is having an understanding and unified view of security events across the attack surface. For more information about the integration, please view the Tenable for Mission Control Solution Overview.
Splunk is a featured partner within Tenable’s Technology Ecosystem, which contains over 75 partners and 100+ unique integrations. The breadth and depth of Tenable’s ecosystem helps joint customers improve their security programs by combining Tenable’s market-leading risk-based vulnerability management solutions with other security applications in their environment. This “better together” approach helps serve and strengthen security programs of all sizes around the world.
Related Articles
- Integrations
- Risk-based Vulnerability Management
- Vulnerability Management






