by Cody Dumont
June 25, 2020
The Cybersecurity Maturity Model Certification (CMMC) was developed to create a framework to assess an organization's implementation of cybersecurity practices across the defense industrial base. Using NIST 800-53 and NIST 800-171 as the baseline, the primary objective of CMMC is to consolidate the two security catalogs into a single measurable framework. Over the next 5 years, starting in June 2020, organizations that create Government off-the-shelf (GOTS) products, handle Federal Contract Information (FCI), or Controlled Unclassified Information (CUI) will need to show compliance at 1 of the 5 levels. Only Certified 3rd Party Assessment Organizations (C3PAO) will be able to certify an organization as compliant or not. Tenable.sc provides on-prem solutions for assessing Cyber Exposure practices and maps these practices to known assessment regulations such as NIST, CSF, and others. This dashboard showcases practices from:
- Identification & Authentication (IA)
- Access Control (AC)
- System & Communications Protection (SC)
- System & Information Integrity (SI)
The federal government relies heavily on external service providers and contractors to assist in carrying out a wide range of federal missions. Sensitive but unclassified federal information is routinely processed by, stored on, or transmitted through nonfederal information systems. Failing to properly protect this Controlled Unclassified Information (CUI) could impact the ability of the federal government’s to successfully carry out required missions and functions. CMMC provides requirements for protecting the confidentiality of CUI. Defense contractors should use these requirements when establishing contracts and agreements with non-federal entities that process, store, or transmit CUI.
Organizations rely on robust authentication, access control, and enforcement of least privilege to protect critical systems and sensitive data. Without proper user authentication and account management, an organization may not know who has access to their network, whether or not old accounts of former employees are still active, and whether or not user passwords meet policy requirements. Default credentials that have not been changed and are well known to attackers could allow systems to be exploited and data to be lost. Without enforcement of least privilege, users on the organization's network may inadvertently access systems or information they should not access, change files, or install malware on the network. Without proper access control, intruders may gain access to the organization's network and sensitive data through compromised mobile devices or removable media, or through remote or wireless means.
Tenable.sc identifies informational data such as user accounts, group memberships, and protocols used to access systems throughout the network. Through active scanning, Nessus provides the ability to track configuration settings related to users and password management, along with other account and privilege settings. When combining the configuration audit information along with user account related informational vulnerabilities, the security operations team is able to identify common overlooked settings, for example users that have never logged in or changed passwords.
Tracking system communications is another vital aspect covered in CMMC. When implementing passive scanning with Nessus Network Monitor (NNM), Tenable.sc can not only identify and track systems communicating with external hosts, but also identity the use of remote access solutions such as remote console access (SSH, RDP, VNC, & etc), VPN technologies, and wireless usage. This information assists the organization in managing and properly restricting access to information systems that process, store, or transmit CUI.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requires audit files utilizing NIST 800-53 and NIST 800-171 checks. The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.9.0
- Compliance Data
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provides the ability to continuously Assess an organization’s adherence to best practice configuration baselines. Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective cybersecurity practices prescribed by CMMC standard.
Components
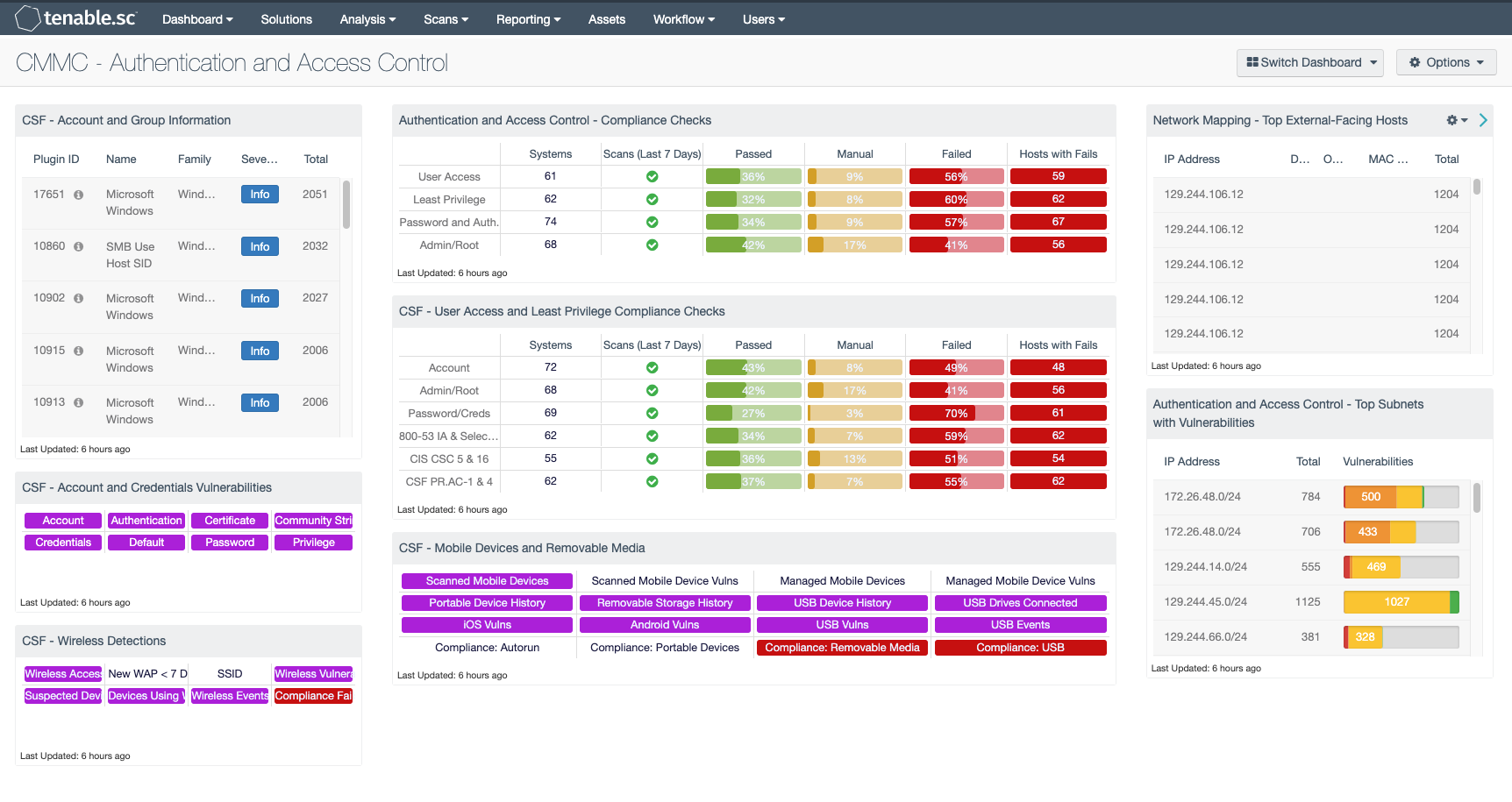
CSF - Account and Group Information: This table displays detections of account and group information, such as accounts that have never been logged into, disabled accounts, and group user lists. This information is obtained through Nessus credentialed scans. Most of these detections will contain lists of accounts in their output. The Obtains the Password Policy detection will contain the retrieved password policy in its output. Clicking on the Browse Component Data icon on the component will bring up the vulnerability analysis screen to display the detections and allow further investigation. In the analysis screen, setting the tool to Vulnerability Detail List will display the full details for each detection, including its description and output.
CSF - Account and Credentials Vulnerabilities: This component displays warning indicators for vulnerabilities actively and passively detected on the network related to accounts and credentials. A purple indicator means that one or more vulnerabilities contain the specified keyword. Clicking on a highlighted indicator will bring up the vulnerability analysis screen to display details on the vulnerabilities and allow further investigation. In the vulnerability analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities are present. Setting the tool to Vulnerability Detail List will display the full details on each vulnerability, including a description, the solution to fix the vulnerability, and in some cases, links to more information.
CSF - Wireless Detections: This component presents a breakdown of detected wireless access points, wireless vulnerabilities, and wireless event activity on the network. Indicators will turn purple when an event or vulnerability is detected. Analysts can drill down to obtain additional information, including IP addresses and MAC addresses. This information can assist an organization in maintaining an accurate inventory and detecting any unauthorized wireless devices.
Authentication and Access Control - Compliance Checks: This component displays compliance information in the areas of user access, least privilege, password and authentication requirements, and administrative/root account control. The displayed compliance information is either based on keywords, or is related to relevant areas in security standards such as NIST SP 800-53, the CIS Critical Security Controls, the Cybersecurity Framework, and ISO/IEC 27001. For each row, the columns provide the number of hosts audited, whether an audit scan was run in the last seven days, the ratios of passed audit checks (in green), checks that require manual verification (in orange), and failed audit checks (in red), and the count of hosts with failed checks. Clicking on a highlighted indicator in the Hosts with Fails column will bring up the vulnerability analysis screen to display the systems with failed audit checks and allow further investigation. Note that in order for data to appear in this component, appropriate audit/compliance scans must first be run on the network.
CSF - User Access and Least Privilege Compliance Checks: This component displays user access and least privilege compliance information in areas such as password requirements, lockout policy after failed logins, and controlled use of administrative privileges. The first rows display compliance information by keyword. The last rows display user access and least privilege compliance information related to several standards: NIST 800-53 (IA family and selected AC controls), CIS Critical Security Controls (v6.0, CSC 5 and 16), and the Cybersecurity Framework (PR.AC-1 and PR.AC-4). For each row, the columns provide the number of hosts audited, whether an audit scan was run in the last seven days, the ratios of passed audit checks (in green), checks that require manual verification (in orange), and failed audit checks (in red), and the count of hosts with failed checks.
CSF - Mobile Devices and Removable Media: This component assists an organization in monitoring mobile devices and removable media. Indicators are highlighted purple for mobile devices detected through active and passive scans, and for mobile devices managed through an MDM server. Indicators are also presented for device connection histories, vulnerabilities, and USB events. Additional indicators are highlighted red for compliance failures related to portable devices and removable media.
Network Mapping - Top External-Facing Hosts: This component uses both PVS plugin ID 14 (Accepts external connections) and PVS plugin ID 16 (Outbound external connections) to identify internal hosts participating in connections to systems outside of the internal network. An outbound external connection means that a system with an IP address in the internal network range (set in the PVS configuration) is talking to a system with an IP address outside of the internal network range. Hosts that accept external connections may be accessible from the internet and should be closely monitored. This table presents host information on the top internal hosts with external connections, including the host IP address, DNS name, operating system CPE, and MAC address. Analysts can drill down to obtain additional information on the external connections, including the ports and protocols observed.
Authentication and Access Control - Top Subnets with Vulnerabilities: This component displays the top Class C subnets with actively and passively detected vulnerabilities related to authentication and access control. These vulnerabilities may include password vulnerabilities, default account and credential vulnerabilities, and other authentication-related vulnerabilities. Presenting these interactions by subnet allows easy understanding of which areas of the network are more vulnerable. Clicking on the Browse Component Data icon will bring up the vulnerability analysis screen to allow further investigation. If desired, the analysis tool can be changed to present the authentication and access control vulnerabilities by vulnerability, IP address, or asset list.