CVE-2023-46805, CVE-2024-21887, CVE-2024-21888 and CVE-2024-21893: Frequently Asked Questions for Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways

Frequently asked questions for five CVEs affecting Ivanti Connect Secure and Policy Secure Gateways, with three of the vulnerabilities having been exploited in the wild as zero-days.
Update February 29: The blog has been updated to include a link to a Cybersecurity Advisory from the Cybersecurity and Infrastructure Security Agency (CISA) and multiple partners about threat actor exploitation of these Ivanti vulnerabilities .
Background
The Tenable Security Response Team has put together this blog to answer Frequently Asked Questions (FAQ) regarding five vulnerabilities affecting Ivanti Connect Secure and Policy Secure Gateways. Three of these five vulnerabilities have been exploited in the wild as zero-days.
FAQ
What are the Ivanti CVEs and when were they disclosed?
As of February 8, there have been five CVEs disclosed by Ivanti throughout January and February 2024:
| CVE | Description | CVSSv3 | Advisory |
|---|---|---|---|
| CVE-2023-46805 | Ivanti Connect Secure and Ivanti Policy Secure Authentication Bypass Vulnerability | 8.2 | Released January 10 |
| CVE-2024-21887 | Ivanti Connect Secure and Ivanti Policy Secure Command Injection Vulnerability | 9.1 | Released January 10 |
| CVE-2024-21888 | Ivanti Connect Secure and Ivanti Policy Secure Privilege Escalation Vulnerability | 8.8 | Released January 31 |
| CVE-2024-21893 | Ivanti Connect Secure, Ivanti Policy Secure and Ivanti Neurons for ZTA Server-Side Request Forgery (SSRF) Vulnerability | 8.2 | Released January 31 |
| CVE-2024-22024 | Ivanti Connect Secure, Ivanti Policy Secure and ZTA Gateways XML External Entity (XXE) Vulnerability | 8.3 | Released February 8 |
CVE-2023-46805 and CVE-2024-21887 were originally disclosed on January 10 and we published a blog post that same day. CVE-2024-21888 and CVE-2024-21893 were disclosed in a security advisory on January 31, the same day this blog post was published.
Which Ivanti products are affected?
Ivanti Connect Secure and Ivanti Policy Secure are impacted by all five of these vulnerabilities. ZTA is also listed in each of the advisories, however Ivanti’s KB article provides further clarification. According to the article, Ivanti Neurons for ZTA gateways cannot be exploited when deployed in a production environment. However when a gateway “is generated and left unconnected to a ZTA controller, then there is a risk of exploitation on the generated gateway.” Ivanti explains further that while Ivanti Neurons for Secure Access is not vulnerable to these CVEs the gateways being managed are.
What is the significance of the two new CVEs disclosed on January 31?
The January 31st advisory from Ivanti includes two new CVE’s that were not known when we released our previous blog post. This advisory indicates that as part of its investigation into CVE-2023-46805 and CVE-2024-21887, Ivanti became aware of two new vulnerabilities, CVE-2024-21888 and CVE-2024-21893. While Ivanti’s advisory says that the SSRF issue (CVE-2024-21893) has only been exploited in limited, targeted attacks, they do note that they “expect a sharp increase in exploitation once this information is public – similar to what we observed on 11 January following the 10 January disclosure.”
What is the significance of the new CVE disclosed on February 8?
The February 8th advisory from Ivanti disclosed CVE-2024-22024, an XXE vulnerability affecting the SAML component of Ivanti Connect Secure, Ivanti Policy Secure and ZTA gateways. This vulnerability could allow an attacker to access restricted resources without any authentication. The vulnerability was internally discovered by Ivanti and has not been exploited in the wild. According to Ivanti, this vulnerability only affects the following versions and products:
- Ivanti Connect Secure: Versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2 and 22.5R1.1
- Ivanti Policy Secure: Version 22.5R1.1
- ZTA version 22.6R1.3
On February 9, researchers at watchTowr Labs released a blog post detailing their discovery and reporting of CVE-2024-22024. According to the blog, watchTowr reported CVE-2024-22024 to Ivanti on February 2nd and pointed out in their blog that they were unclear why Ivanti's advisory mentioned the XXE was discovered internally by Ivanti. The watchTowr blog post describes the issue and how they tested it, but does stop short of providing an exploit script. Later on February 9, an update was made to the Ivanti advisory for CVE-2024-22024 which stated that CVE-2024-22024 was also responsibly disclosed by watchTowr.
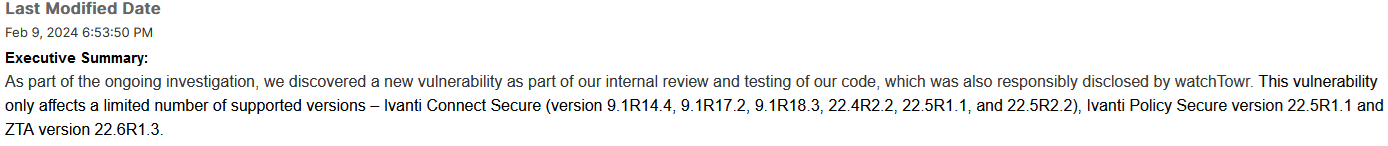
Image Source: Ivanti Advisory for CVE-2024-22024
Which of these five CVE’s have been exploited?
As of February 8, Ivanti is aware of exploitation for three of the five CVEs, which were exploited in the wild as zero-days:
- CVE-2023-46805
- CVE-2024-21887
- CVE-2024-21893
At the time this blog was published, no known exploitation for CVE-2024-21888, the privilege escalation vulnerability affecting the web component of Ivanti Connect Secure and Policy Secure, has been observed. However, It’s important to note that CVE-2023-46805 and CVE-2024-21887 are being exploited in chained attacks, allowing the threat actor to compromise devices without authentication. CVE-2024-21893 can also be exploited without authentication, allowing for limited access to resources. As of February 8, no known exploitation has been observed for CVE-2024-22024, the latest CVE announced by Ivanti who discovered the XXE flaw during their ongoing investigation of these vulnerabilities.
On February 9, a post on X (formerly Twitter) by security researcher Kevin Beaumont stated that Ivanti's claims that CVE-2024-22024 has not been exploited are "false." In addition, Beaumont linked to a blog post from watchTowr who reported the issue to Ivanti, but were not credited in the security advisory that claims the vulnerability was found internally. An update to the advisory was made on February 9th, crediting watchTowr. At the time of this blogs update on February 9, we do not have any further information on exploit activity beyond the post by Beaumont, nor a confirmation from Ivanti in their advisory that exploitation has been observed. Despite the uncertainty, we strongly recommend referring to Ivanti's recommendations for patching or mitigation steps if a patch is not available for your release branch.
When was zero-day exploitation first observed for these vulnerabilities?
According to Ivanti and a blog by Volexity, CVE-2023-46805 and CVE-2024-21887 were first exploited in the wild in a chained attack for unauthenticated remote code execution (RCE) as early as December 3, 2023.
While Ivanti has observed limited, targeted attacks using CVE-2024-21893, the newly disclosed SSRF issue, at this time, it’s unclear when this exploitation was first identified.
Are these vulnerabilities being actively exploited?
Yes, as noted above, three of the five vulnerabilities have seen active exploitation. According to an alert from the US Cybersecurity Agency (CISA), multiple threat actors are actively targeting and exploiting affected devices to plant webshells and/or steal credentials. The CISA warning also states that threat actors have identified workarounds to the original mitigations supplied by Ivanti in their first advisory.
A Volexity blog post and Mandiant blog post have been released highlighting exploitation by multiple threat actors and APT groups who have planted webshells and malware on affected devices in widespread, global attacks.
On January 31, Mandiant published a follow up blog post detailing the webshells and malware they have identified in their incident response engagements from impacted customers. Mandiant's blog post provides an overview of post exploitation activity and additional tactics, techniques, and procedures (TTPs) that have been observed.
On February 4, Shadowserver posted on X (formerly Twitter) that a major increase in exploitation activity for CVE-2024-21893 has been observed, prior to the public release of proof-of-concept (PoC) code. At the time of the post, over 170 distinct IP addresses has been observed in attempts to exploit the vulnerability.
On February 29, CISA along with multiple partners released a Cybersecurity Advisory (CSA) AA24-060B detailing the exploitation of these vulnerabilities by threat actors. This CSA includes indicators of compromise and observed activity from incident response investigations.
Are patches or mitigations available?
Yes, as of January 31, the first set of patches have been released to address all four of the vulnerabilities that were known at the time affecting Ivanti Connect Secure versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2 and 22.5R1.1 as well as ZTA version 22.6R1.3. Additional patches are expected to be released in phases.
Ivanti’s original advisory stated that the first patches would be released the week of January 22, however on January 26, their advisory was updated to reflect that “The targeted release of patches for supported versions is delayed, this delay impacts all subsequent planned patch releases.”
On February 8, Ivanti announced a new set of patches to address CVE-2024-22024 along with the four previously disclosed CVEs.
| Product | Fixed Release |
| Ivanti Connect Secure | 9.1R14.5, 9.1R17.3, 9.1R18.4, 22.4R2.3, 22.5R1.2, 22.5R2.3 and 22.6R2.2 |
| Ivanti Policy Secure | 9.1R17.3, 9.1R18.4 and 22.5R1.2 |
| ZTA Gateways | 22.5R1.6, 22.6R1.5 and 22.6R1.7 |
For those versions which are still impacted and do not yet have a patch available, a KB article from Ivanti provides mitigation guidance, which has been updated several times since its original release. It is important to note that the current guidance recommends a factory reset of the affected appliance before applying the patch in order to prevent threat actors from maintaining persistence on a compromised device. Ivanti’s KB article was updated on February 8 to include that CVE-2024-22024 is also mitigated by the supplied mitigation script released on January 31. We recommend reviewing the KB article and advisories for the latest information on patching and mitigation steps.
If I’ve applied the mitigation, do I need to apply the patch?
Applying the relevant patch, once available, is the best way to ensure that your device is secured for these vulnerabilities. Ivanti notes that if you have applied the mitigation, it can be removed after the patch has been applied.
An important note listed on the KB article states that no configuration changes should be pushed to the appliance that has the XML mitigation script in place. It’s possible that configuration changes could stop key services from running, thereby impacting the mitigation and limiting its efficacy.
What actions are required for Federal Civilian Executive Branch (FCEB) agencies?
On January 19, CISA published their first emergency directive (ED) 24-01 for 2024 concerning mitigating vulnerabilities impacting Ivanti Connect Secure and Ivanti Policy Secure Vulnerabilities. According to the ED, FCEB agencies were required to apply the mitigation supplied by Ivanti no later than 11:59 pm EST on Monday January 22, 2024, along with performing additional actions outlined in the directive. With the release of the additional two CVEs, CISA released a supplemental ED on January 31 with updated guidance in the wake of continued exploitation of affected devices. According to the supplemental ED, agencies running affected products are to "disconnect all instances of Ivanti Connect Secure and Ivanti Policy Secure solution products from agency networks" no later than 11:59PM on Friday February 2, 2024. Additional actions are listed in the directive and we recommend that you review the steps CISA has outlined and take appropriate action.
Can I use the internal integrity checker (ICT) to identify malicious activity?
According to Ivanti, the internal ICT does not scan for malware and cannot be used to identify threat activity. Ivanti and CISA both note that threat actors have been observed manipulating the ICT in order to hide traces of their activity, so it cannot be trusted. They do recommend running the external ICT, which is receiving regular updates for new functionality.
Has Tenable released any product coverage for these CVEs?
Yes, product coverage is available and can be found on the individual CVE pages for each of these CVEs:
These links will display all available plugins for these vulnerabilities, including upcoming plugins in our Plugins Pipeline. Note that CVE coverage for CVE-2024-22024 is expected to be released soon.
Change Log
Update February 29: The blog has been updated to include a link to a Cybersecurity Advisory from the Cybersecurity and Infrastructure Security Agency (CISA) and multiple partners about threat actor exploitation of these Ivanti vulnerabilities .
Update February 9: The blog has been updated to include additional information about possible exploitation of CVE-2024-22024.
Update February 8: The blog has been updated to include information on CVE-2024-22024, a new CVE found by Ivanti during their investigation into the vulnerabilities discussed in this blog.
Update February 5: The blog has been updated to include information about increased exploitation activity and the release of exploit code for CVE-2024-21893.
Update February 2: The blog has been updated to include information from the US Cybersecurity and Infrastructure Security Agency (CISA) Emergency Directive ED 24-01 and a supplemental update to the directive.
Update January 31: The blog has been updated to include a link to a blog by Mandiant with additional information about the tactics used by an APT group actively exploiting these vulnerabilities.
Get more information
- Tenable Blog Post: CVE-2023-46805, CVE-2024-21887: Zero-Day Vulnerabilities Exploited in Ivanti Connect Secure and Policy Secure Gateways
- Ivanti Security Advisory: CVE-2023-46805 and CVE-2024-21887
- Ivanti Security Advisory: CVE-2024-21888 and CVE-2024-21893
- Ivanti Security Advisory: CVE-2024-22024
- Ivanti KB article
- Mandiant Blog: Cutting Edge, Part 2: Investigating Ivanti Connect Secure VPN Zero-Day Exploitation
- CISA Cybersecurity Advisory: Threat Actors Exploit Multiple Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management



