CVE-2020-6287: Critical Vulnerability in SAP NetWeaver Application Server JAVA Disclosed (RECON)

Researchers disclosed a critical flaw in SAP NetWeaver Application Server that could allow an attacker to gain access to any SAP application. Organizations are strongly encouraged to apply patches as soon as possible.
Update July 16, 2020: A proof of concept script has become publicly available for CVE-2020-6286. The proof of concept section of our blog has been updated accordingly.
Background
Around 5 p.m. PST on July 13, SAP disclosed two vulnerabilities in SAP NetWeaver Application Server JAVA (AS JAVA), including a critical flaw reported by the security firm Onapsis. SAP NetWeaver is considered the “central foundation for the entire SAP software stack” and allows access to SAP data over Hypertext Transfer Protocol (HTTP). The flaws reside in the LM Configuration Wizard, a component of AS JAVA.
Analysis
CVE-2020-6287 is caused by a complete lack of authentication in the SAP NetWeaver AS Java’s LM Configuration Wizard. Due to the lack of authentication, a remote unauthenticated attacker could execute “critical actions,” including creating an administrator user and providing them with the “keys to the kingdom” over the SAP NetWeaver AS JAVA system. An attacker could gain access to
CVE-2020-6286 is a path traversal vulnerability due to the lack of input validation for a path in a “certain parameter” of the web service. An unauthenticated, remote attacker could exploit this vulnerability and “download zip files to a specific directory.” The vendor assigned this vulnerability a CVSSv3 score of 5.3.
Vulnerability potentially affects multiple SAP solutions
According to an alert from the Cybersecurity Infrastructure Security Agency (CISA), CVE-2020-6287 is present by default in SAP applications running on top of SAP NetWeaver AS Java v7.3 and newer, including SAP NetWeaver v7.5. Additionally, this could potentially affect a variety of other SAP Java-based business solutions, including the following:
- SAP Enterprise Resource Planning
- SAP Product Lifecycle Management
- SAP Customer Relationship Management
- SAP Supply Chain Management
- SAP Supplier Relationship Management
- SAP NetWeaver Business Warehouse
- SAP Business Intelligence
- SAP NetWeaver Mobile Infrastructure
- SAP Enterprise Portal
- SAP Process Orchestration/Process Integration
- SAP Solution Manager
- SAP NetWeaver Development Infrastructure
- SAP Central Process Scheduling
- SAP NetWeaver Composition Environment
- SAP Landscape Manager
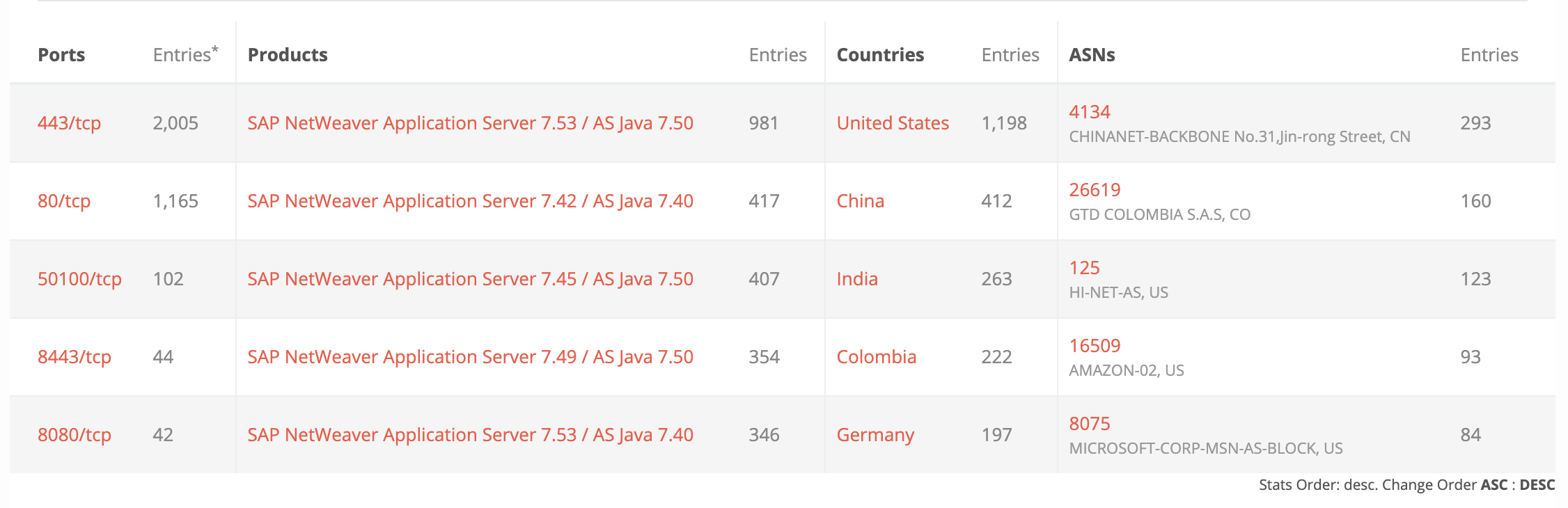
Publicly accessible NetWeaver AS JAVA systems
According to Onapsis, which identified and reported CVE-2020-6287 to SAP, more than 40,000 SAP customers may be affected. Based on a BinaryEdge search, there are at least 4,000 publicly accessible SAP NetWeaver AS JAVA systems. However, it is very likely that there are additional publicly accessible and vulnerable systems.
Proof of concept
A proof-of-concept (PoC) for CVE-2020-6286 has been published by security researcher Dmitry Chastuhin to his GitHub repository. The script allows the download of any zip file from a vulnerable SAP server.
At the time this blog post was published, there was no PoC code publicly available for CVE-2020-6287. However, considering the simplistic nature of potential exploitation for this vulnerability and publicly available patches that can be reverse engineered, we anticipate that a PoC will be published very quickly.
Solution
To address these CVEs, SAP released security updates in SAP Security Note #2934135 as part of their Security Patch Day for July 2020. According to the SAP Security Note #2934135, if the patch cannot be applied, the proposed workaround is to disable the LM Configuration Service (tc~lm~ctc~cul~startup_app application). While the workaround is defined as “defense in depth,” SAP notes that this is “not a solution.” SAP provides additional information on disabling the LM Configuration Service in SAP Security Note #2939665. Based on the severity of this vulnerability, we strongly recommend applying patches as soon as possible, focusing on internet-facing systems which are more at risk than internal systems.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released.
Get more information
- SAP Note #2934135 - [CVE-2020-6287] Multiple Vulnerabilities in SAP NetWeaver AS JAVA (LM Configuration Wizard)
- SAP Security Patch Day for July 2020
- AA20-195A: CISA Alert for SAP NetWeaver AS Java
- Onapsis Vulnerability Threat Report
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


