CVE-2020-8193, CVE-2020-8195, and CVE-2020-8196: Active Exploitation of Citrix Vulnerabilities

Following active exploitation against F5 BIG-IP devices, exploit attempts targeting newly disclosed vulnerabilities in Citrix products have begun, which include potential extraction of VPN sessions on vulnerable targets.
Background
On July 7, Citrix disclosed 11 new vulnerabilities in the Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliance devices. Following the disclosure of these vulnerabilities, Citrix published a blog post noting that there were some barriers to exploitation, but encouraged customers to apply the security fixes as soon as possible. Shortly after the disclosure, Dr. Ullrich of SANS Internet Storm Center (ISC) detected unidentified exploit attempts leveraging some of these vulnerabilities, which appeared to be probing for vulnerable devices.
Analysis
The following is the list of vulnerabilities that Citrix patched as part of their recent CTX276688 advisory:
| CVE ID | Vulnerability Type | Actively Exploited |
|---|---|---|
| CVE-2019-18177 | Information disclosure | No |
| CVE-2020-8187 | Denial of service | No |
| CVE-2020-8190 | Local elevation of privileges | No |
| CVE-2020-8191 | Reflected Cross Site Scripting (XSS) | No |
| CVE-2020-8193 | Authorization bypass | Yes |
| CVE-2020-8194 | Code Injection | No |
| CVE-2020-8195 | Information disclosure | Yes |
| CVE-2020-8196 | Information disclosure | Yes |
| CVE-2020-8197 | Elevation of privileges | No |
| CVE-2020-8198 | Stored Cross Site Scripting (XSS) | No |
| CVE-2020-8199 | Local elevation of privileges | No |
Of the 11 vulnerabilities patched by Citrix, attackers are attempting to exploit the following CVEs in the wild:
CVE-2020-8193 is an authorization bypass vulnerability in the management interface on the device’s NSIP address. The NSIP address is a specific device IP address dedicated to the management interface for Citrix devices. An attacker could send a specially crafted request to the NSIP address that bypasses the administrator login and gain direct access to the device.
CVE-2020-8195 and CVE-2020-8196 are information disclosure vulnerabilities found in the management interface with either user access or after exploiting the auth bypass on the device. By sending a specially crafted HTTP request, an attacker could retrieve important device information like configuration files. At this time, it’s unknown which of these two vectors are specifically being used to target victims due to the similarities between the vulnerabilities.
These three CVEs were discussed in a technical writeup by Donny Massland, one of the researchers credited with reporting five of the 11 vulnerabilities, where Massland discusses the potential impact of exploitation of these vulnerabilities.
Well, since people wanted to know, here is my write-up for the Citrix vulnerabilities I found last January (including local file disclosure!):https://t.co/XkubhdVpv9
— Donny Maasland (@donnymaasland) July 8, 2020
Exploitation in the wild
On July 10, the NCC Group’s Research and Intelligence Fusion Team (RIFT) detected active exploitation of a subset of the vulnerabilities Massland disclosed.
On the Citrix ADC Vulnerabilities per @donnymaasland 's blog we've confirmed impact / replicated VPN session theft.https://t.co/2YgBBcv3DI pic.twitter.com/cZSnOhuyLO
— NCC Group Research & Technology (@NCCGroupInfosec) July 10, 2020
NCC Group subsequently published their own blog post about the flaws, detailing the detected exploitation alongside the information gathered by SANS and created a timeline showcasing disclosure to exploitation.
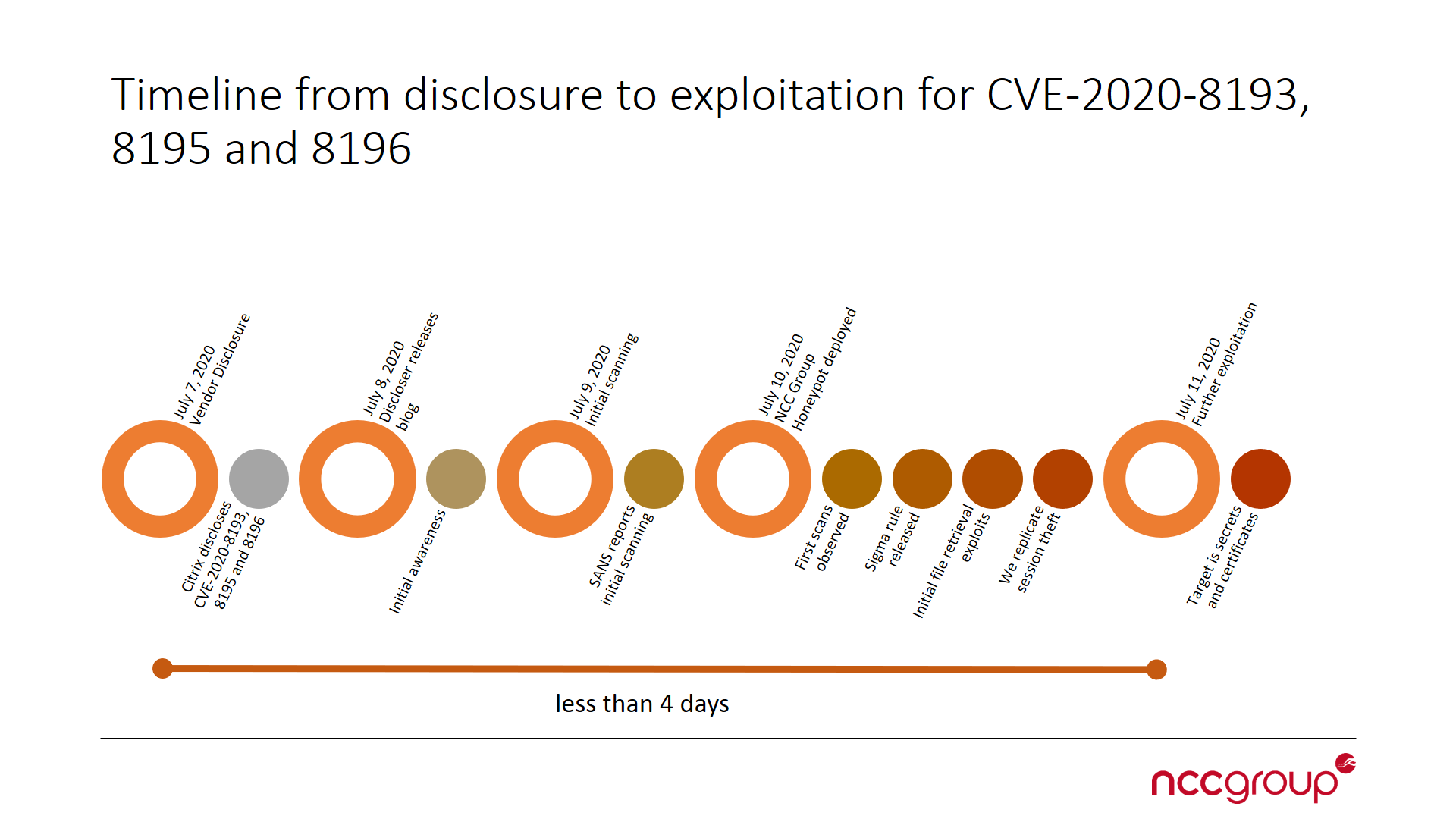
Image Source: NCC RIFT
The quick turnaround time from disclosure to exploitation from the detected threat group matches up with attacks by the same threat actor that NCC Group observed utilizing the F5 BIG-IP vulnerability that was disclosed on June 30. Within less than a week from disclosure, vulnerable assets were being successfully exploited.
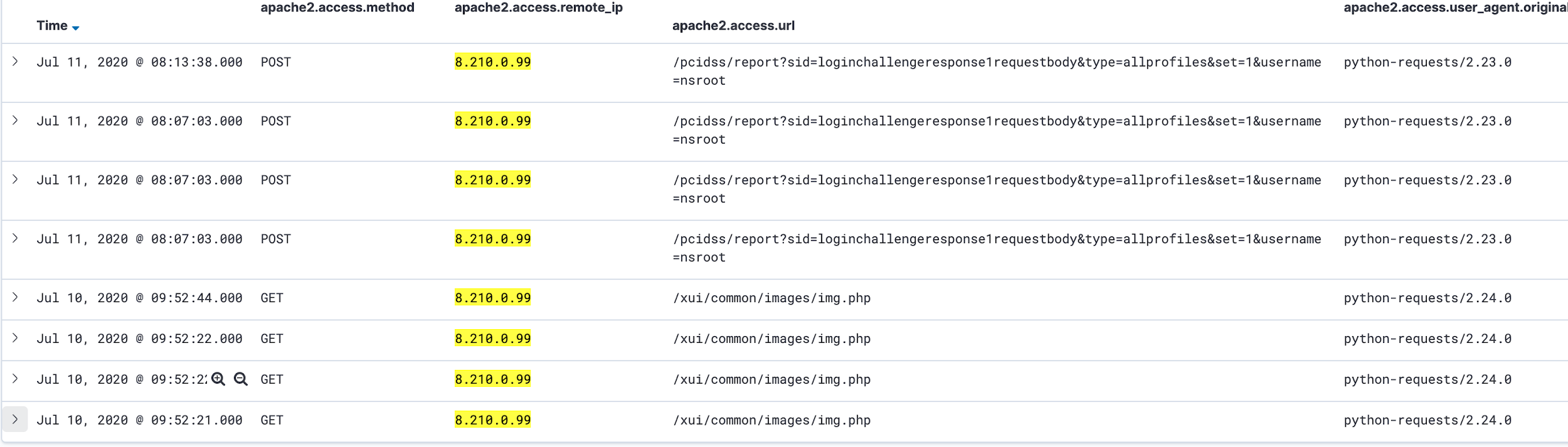
Image Source: NCC RIFT
Proof of concept
Massland's Blog provides examples of exploitation for obtaining device configurations and active VPN sessions and several researchers have released PoC scripts to the general public on GitHub.
Solution
Citrix has released patches for these vulnerabilities, and lists the following versions as fixed:
| Affected Products | Fixed Versions |
|---|---|
| Citrix ADC and Citrix Gateway | 13.0-58.30 and later releases |
| Citrix ADC and NetScaler Gateway | 12.1-57.18 and later 12.1 releases 12.0-63.21 and later 12.0 releases 11.1-64.14 and later 11.1 releases |
| NetScaler ADC and NetScaler Gateway | 10.5-70.18 and later 10.5 releases |
| Citrix SD-WAN WANOP | 11.1.1a and later releases 11.0.3d and later 11.0 releases 10.2.7 and later 10.2 releases |
| Citrix Gateway Plug-in for Linux | 1.0.0.137 and later versions |
Tenable strongly recommends applying these patches as soon as possible, especially now that active exploitation has been observed in the wild.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities can be found here.
Get more information
- CVE-2020-5902 : Tenable Blog covering a critical vulnerability in F5 BIG-IP
- Citrix Advisory CTX276688
- Citrix Blog providing additional context on CTX276688
- SANS ISC Exploitation Detection
- NCC Group RIFT Analysis Blog
- Donny Massland's Vulnerability Disclosure
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


