Cybersecurity Snapshot: 6 Things That Matter Right Now

Topics that are top of mind for the week ending Oct. 7 | CISA puts spotlight on asset inventory and vulnerability management | Think tank does deep dive on IoT security | What’s the current state of cybersecurity? Not great | New malware cracks monthly top 10 list | And much more!
1 – CISA: Asset inventory and VM are fundamental practices
As Cybersecurity Awareness Month kicks off, here’s a fresh reminder from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) that visibility into all of your IT and operational technology (OT) assets and their vulnerabilities is critical for reducing cyber risk.
In a “binding operational directive” issued this week, CISA stresses the importance of having an updated, comprehensive inventory of IT and OT assets and of continuously detecting their vulnerabilities.
The document’s requirements include that by April 3, 2023 civilian executive-branch agencies of the federal government be able to:
- Perform automated discovery of IP-addressable networked assets that are on-prem, remote and in the cloud every seven days.
- This includes OT and metadata around scan maturity, scan frequency and scan depth.
- Trigger vulnerability detection across all discovered assets every 14 days.
- Ingest detected vulnerabilities into CISA’s Continuous Diagnostics and Mitigation (CDM) dashboard within 72 hours of discovery.
- Search for inventoried assets and detected vulnerabilities within 72 hours of receiving a CISA request and deliver the results within seven days.
Further analysis and commentary about the CISA directive from FCW, Forrester, The Record and Federal News Network.
More resources about Cybersecurity Awareness Month from CISA, the National Cybersecurity Alliance, the Center for Internet Security and the National Institute of Standards and Technology.
For more information about asset inventory and vulnerability management, check out these Tenable resources:
- VM Fundamentals: How to Perform Asset Discovery and Classification
- Full IT Visibility Requires Business Risk Context
- These Are the Building Blocks of Effective Vulnerability Management
- Busting 5 Common Myths About Vulnerability Assessment
- Cloud Security: Why You Shouldn’t Ignore Ephemeral Assets
2 – A framework for securing the IoT ecosystem
The Internet of Things (IoT) ecosystem – devices, services, networks – keeps growing, along with complex cybersecurity issues that accompany it.
In a new report, the Atlantic Council think tank outlines key technology and policy issues that complicate IoT security, using the U.S., the U.K., Australia and Singapore as case studies, and zooming in on three industries: smart homes; networking and telecommunications; and consumer healthcare.
The report also recommends specific steps that governments can take to help make IoT products more secure, including:
- Mandate that IoT manufacturers operating in their markets meet a baseline of minimally acceptable security requirements for their products.
- Pressure domestic suppliers and retailers to demand from manufacturers that they make their IoT products more secure.
- Create advanced security requirements for IoT products, and encourage manufacturers to adopt them.
Overview of Actors and Actions to Improve IoT Security
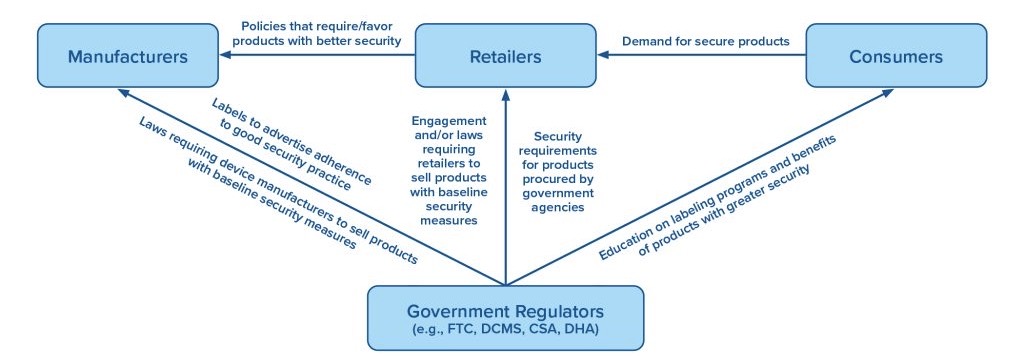
(Source: Atlantic Council’s “Security in the billions: Toward a multinational strategy to better secure the IoT ecosystem,” Sept. 2022)
For more information about IoT security:
- “What is IoT security?” (TechTarget)
- “IoT Security Assurance Framework” (IoT Security Foundation)
- “Securing the Internet of Things” (U.S. Department of Homeland Security)
- “Securing the IoT Supply Chain” (IoT Security Foundation)
- “Three strategies for navigating the fragmented IoT security ecosystem” (IoXT Alliance)
3 – U.S. government details hack of defense organization
CISA, the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA) released an eye-opening joint advisory this week, outlining a months-long advanced persistent threat (APT) attack against an unnamed “defense industrial base organization.”
According to the advisory, it’s likely that multiple APT groups were involved and that they used an open-source toolkit called Impacket to breach the victim’s enterprise network and an exfiltration tool called CovalentStealer to swipe sensitive data. The attackers also exploited a Microsoft Exchange vulnerability to access company email accounts.
The agencies want defense industrial organizations and critical infrastructure providers to read the advisory to understand how the hack was carried out and how they could defend themselves against similar attacks.
Here’s a quick glance at some mitigation recommendations:
- Segment networks based on role and functionality
- Manage vulnerabilities and misconfigurations
- Search for anomalous behavior
- Restrict and secure use of remote admin tools
- Implement a mandatory access control model
- Audit account usage
More coverage and analysis about this advisory from The Hacker News, MeriTalk, The Record and Infosecurity Magazine.
4 – A temperature check on tool sprawl
There’s a trend among CISOs wanting to consolidate their cybersecurity product stacks and shrink their roster of vendors, in an attempt to rein in tool sprawl. It’s a pain point for cyber teams, as they move away from siloed point tools and seek integrated products that interoperate and share data, and that ultimately make it easier to get actionable insights for reducing cyber risk. At a recent Tenable webinar, we took the opportunity to poll participants about the size of their tool stacks. Here’s what we found.
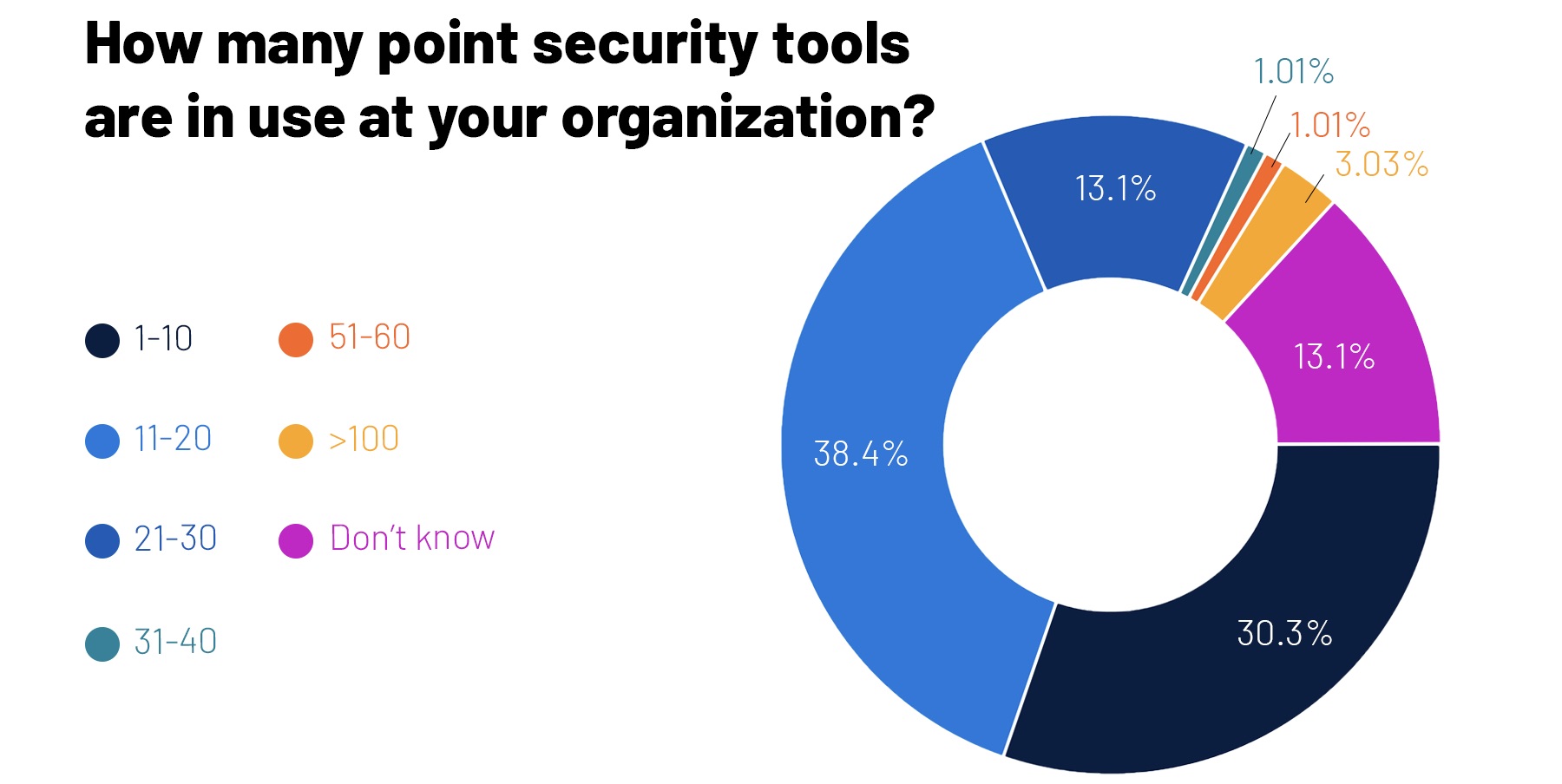
(99 respondents polled by Tenable in Sept. 2022)
For more information about this topic:
- “The shift to integrated cybersecurity platforms: a growing trend among CISOs” (Tenable)
- “Most enterprises looking to consolidate security vendors” (CSO Magazine)
- “Note to Security Vendors: Companies Are Picking Favorites” (Dark Reading)
- “Thanks to the economy, cybersecurity consolidation is coming” (Protocol)
- "Cybersecurity: Best-of-Breed Approach or Single-Vendor Platform?" (BizTech Magazine)
5 – The state of cybersecurity? Not good enough
Here’s a bumper crop of insights into how security teams are tackling – with varying degrees of success – the challenges of a growing and complex attack surface: The wide-ranging “2022 State of Cybersecurity” report from the non-profit Computing Technology Industry Association (CompTIA.)
“Digital transformation driven by cloud and mobile adoption is forcing a new strategic approach to cybersecurity, but fully adopting this new approach poses significant challenges, both tactically and financially,” reads the report.
As a result, the report, which polled more than 1,200 business and IT pros involved in cybersecurity in the U.S., Canada, Europe, Oceania and Southeast Asia, concludes that cybersecurity remains “a problematic area” which is making “relatively slow progress.”
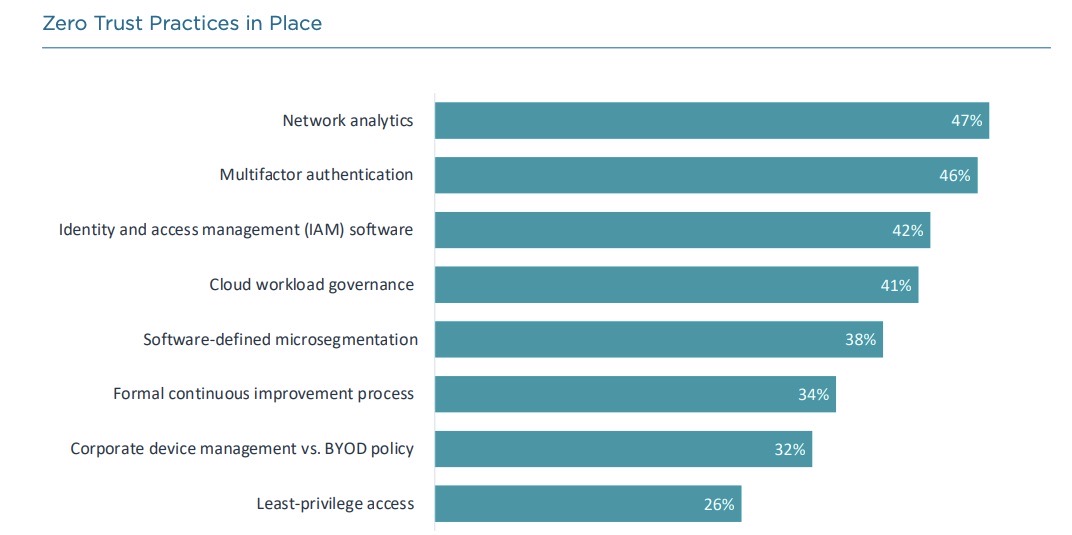
Meanwhile, four key trends are impacting cybersecurity teams, including:
- The further merging of cybersecurity and business operations
- An emphasis on zero trust to trigger improvements
- A focus on staff specialization
- A boost in tools’ automated capabilities
When asked to list their organization's main changes in cybersecurity approach this year, the 500 U.S. respondents listed these top five:
- Higher priority on incident response (cited by 43%)
- More diverse set of technology tools (39%)
- Greater focus on process improvement (38%)
- Shift to proactive measures (37%)
- Greater focus on employee education (36%)
As they deal with the most common types of incidents – malware-infected devices and infrastructure, lost or stolen devices, unauthorized backend access and ransomware attacks – U.S. respondents react in various ways, as illustrated by the charts below.
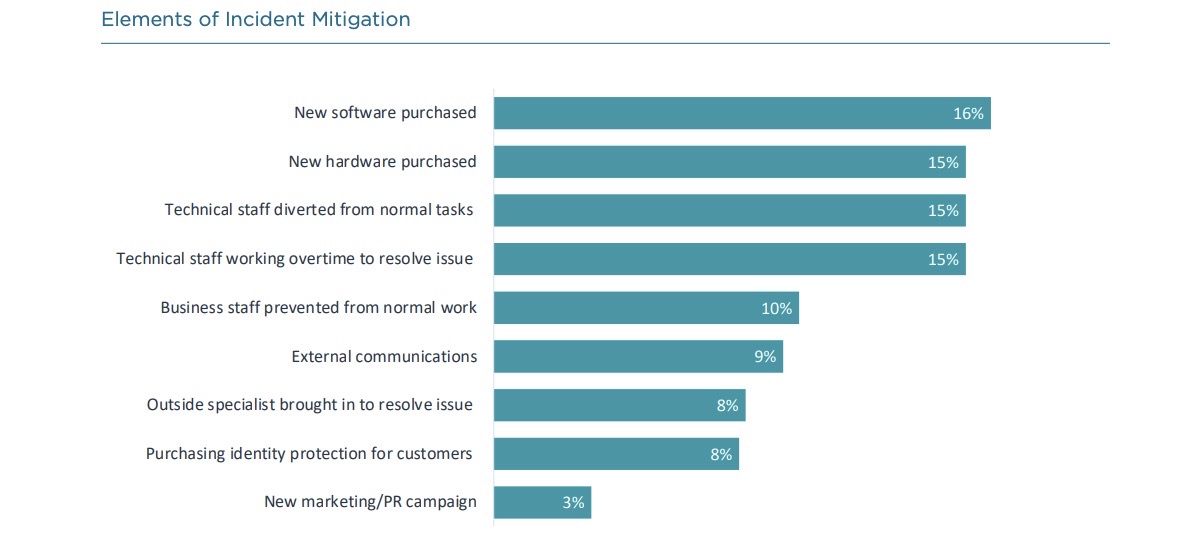
(Source: CompTIA's “2022 State of Cybersecurity” report, Sept. 2022)
For more information:
- Check out highlights from the report
- Read the full report on the web or as a PDF
6 – CIS: New strains show up in August’s top malware list
The Center for Internet Security recently released its list of the top malware for August, noting that the lineup features notable changes compared with the previous month.
Namely, LingyunNET, RecordBreaker and TeamSpy made their debut on the monthly list, and SocGholish and Tinba returned to it.
Here’s the full list:
- SocGholish, a remote access trojan (RAT) and a banking trojan that uses fake Flash updates
- ZeuS, a modular banking trojan that uses keystroke logging
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI) and EternalBlue
- TeamSpy, spyware that uses remote access tool TeamViewer and malware to steal information
- NanoCore, a RAT that spreads via malspam as a malicious Excel spreadsheet
- LingyunNet, riskware that uses victims’ system resources
- Agent Tesla, a RAT that captures credentials, keystrokes and screenshots
- Gh0st, a RAT for creating backdoors to control endpoints
- RecordBreaker, an information stealer that’s the successor to Racoon Stealer
- Tinba, a banking trojan also known as Tiny Banker because of its small file size
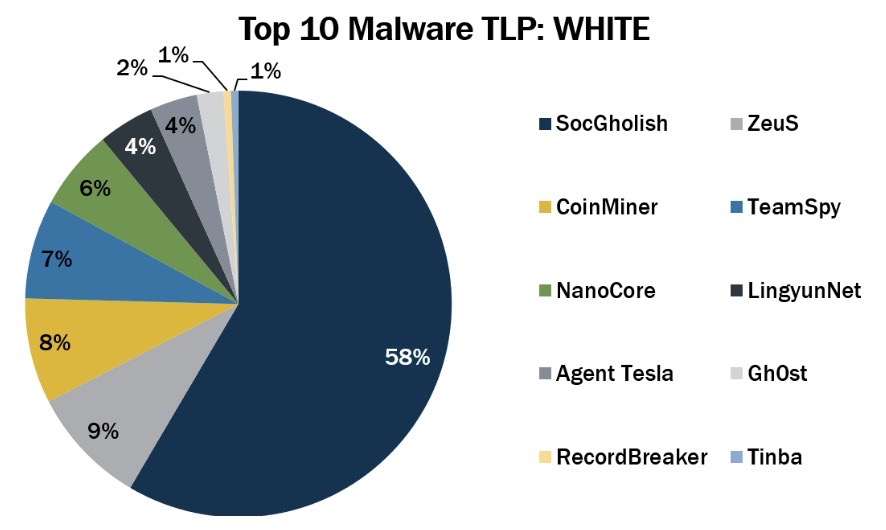
(Source: Center for Internet Security, Sept. 2022)
To get all the details, context and indicators of compromise for each malware, read the CIS report.
Tenable has launched the Tenable One Exposure Management Platform, which unifies a variety of data sources into a single exposure view to help organizations gain visibility, prioritize efforts and communicate cyber risks. Check out these resources to learn more about it!
- Introducing the Tenable One Exposure Management Platform (blog)
- Exposure Management: Reducing Risk in the Modern Attack Surface (blog)
- 3 Real-World Challenges Facing Cybersecurity Organizations: How an Exposure Management Platform Can Help (white paper)
- From Risk-Based Vulnerability Management to Exposure Management (infographic)
- Exposure Management and the Future of Cybersecurity (LinkedIn Live)
- Asset Management
- Cloud
- Cybersecurity Snapshot
- Government
- Vulnerability Management

