Cybersecurity Snapshot: New Guide Details How To Use AI Securely, as CERT Honcho Tells CISOs To Sharpen AI Security Skills Pronto

Cyber agencies from multiple countries published a joint guide on using artificial intelligence safely. Meanwhile, CERT’s director says AI is the top skill for CISOs to have in 2024. Plus, the UK’s NCSC forecasts how AI will supercharge cyberattacks. And a global survey shows cyber pros weighing pros and cons of AI. And much more!
Dive into six things that are top of mind for the week ending January 26.
1 - Using AI securely: Global cyber agencies publish new guide
Is your organization – like many others – aggressively adopting artificial intelligence to boost operational efficiency? If so, you might want to check out a new guide published this week about how businesses can use AI securely.
Created by the Australian Cyber Security Centre (ACSC) in collaboration with cyber agencies from 10 other countries, the “Engaging with Artificial Intelligence” guide highlights AI system threats, offers real-world examples and explains ways to mitigate these risks.
AI threats discussed in the document include:
- AI model data poisoning
- Input manipulation, including prompt injection
- Generative AI hallucination outputs
- Privacy and intellectual property violations
- Theft of AI models

And here are some of the guide’s recommendations:
- Implement mitigations from cybersecurity frameworks relevant to your organization, such as the NIST AI Risk Management Framework and MITRE’s ATLAS
- Assess how your organization’s privacy and data protection obligations will be impacted by your AI systems’ ways of collecting, processing and storing data
- Protect access to your AI systems with phishing-resistant multifactor authentication
- Keep backups of your AI models and training data
- Assess if an AI system vendor followed secure-by-design principles while developing it
To get more details, check out:
- the “Engaging with Artificial Intelligence” guide
- the ACSC announcement “New guidance for engaging with artificial intelligence”
- the U.S. Cybersecurity and Information Security Agency’s announcement “CISA Joins ACSC-led Guidance on How to Use AI Systems Securely”
For more information about using AI securely:
- “Adversarial Machine Learning and Cybersecurity: Risks, Challenges, and Legal Implications” (Stanford University and Georgetown University)
- “Considerations for Implementing a Generative Artificial Intelligence Policy” (ISACA)
- “Top 10 Critical Vulnerabilities for Large Language Model Applications” (OWASP)
- “A CISOs Guide: Generative AI and ChatGPT Enterprise Risks” (Team8)
- “Envisioning Cyber Futures with AI” (Aspen Institute)
2 - CERT Director to CISOs: Grok AI now
Mastering AI. That’s the number one skill CISOs must acquire in 2024, according to Greg Touhill, Director of the CERT Division of Carnegie Mellon University’s Software Engineering Institute (SEI).
In his article “The Top 10 Skills CISOs need in 2024,” published on the SEI’s blog this week, Touhill unequivocally ranks AI at the top of his list, advising CISOs to “master AI before it masters you.”
“CISOs need to understand the power and potential of AI-enabled technologies well beyond the mechanics of how AI is constructed and operated,” Touhill writes.

CERT Director Greg Touhill (Credit: Carnegie Mellon University)
Specifically, CISOs must:
- Understand the various types of AI platforms
- Know how these platforms can be used by their organizations and against their organizations
- Help their organizations craft proper governance and oversight processes for AI use
- Know who to contact for help on AI matters
“The present and near-future for CISOs will be marked by breathtaking technical advances, particularly those associated with the inclusion of artificial intelligence technologies being integrated into business functions,” he writes.
Rounding out the top five skills CISOs need to develop in 2024 are:
- Improve communication with the board of directors and the C-suite
- Deepen their understanding of their organization’s business
- Use advanced metrics to manage their organization’s cyber risk posture
- Better their understanding and management of supply chain risks
“Some forecasts have already characterized 2024 as a pressure cooker environment for CISOs. In such an environment, skills are critical,” writes Touhill, who was the U.S. federal government’s first CISO, appointed by former President Barack Obama.
For more information about CISO priorities and challenges in 2024:
- “A tougher balancing act in 2024, the year of the CISO” (CSO Online)
- “CISO Planning for 2024 May Struggle When It Comes to AI” (Dark Reading)
- “The state of the CISO? A mix of anxiety and empowerment” (Tenable)
- “CISOs’ crucial role in aligning security goals with enterprise expectations” (Help Net Security)
- “What’s important to CISOs in 2024” (PwC)
VIDEOS
CISO Predictions for 2024 (CISO Tradecraft)
Achievements and Aspirations: Reflecting on 2023 and Predicting 2024 (CISO Global)
3 - U.K. cyber agency: AI will boost quantity and intensity of cyberattacks
The volume and impact of cyberattacks, including ransomware, will grow over the next two years, as malicious actors of all stripes incorporate AI into their toolboxes. Still, how the bad guys use AI and what benefits they get from it will depend on their level of skill and knowledge.
So says the U.K. National Cyber Security Centre (NCSC) in its new report “The near-term impact of AI on the cyber threat,” published this week.
Here’s a table with a nifty breakdown of how the NCSC projects that AI will supercharge the cyberattack capabilities of cybercriminals with different levels of sophistication.
Extent of Capability Uplift Caused by AI over the Next Two Years
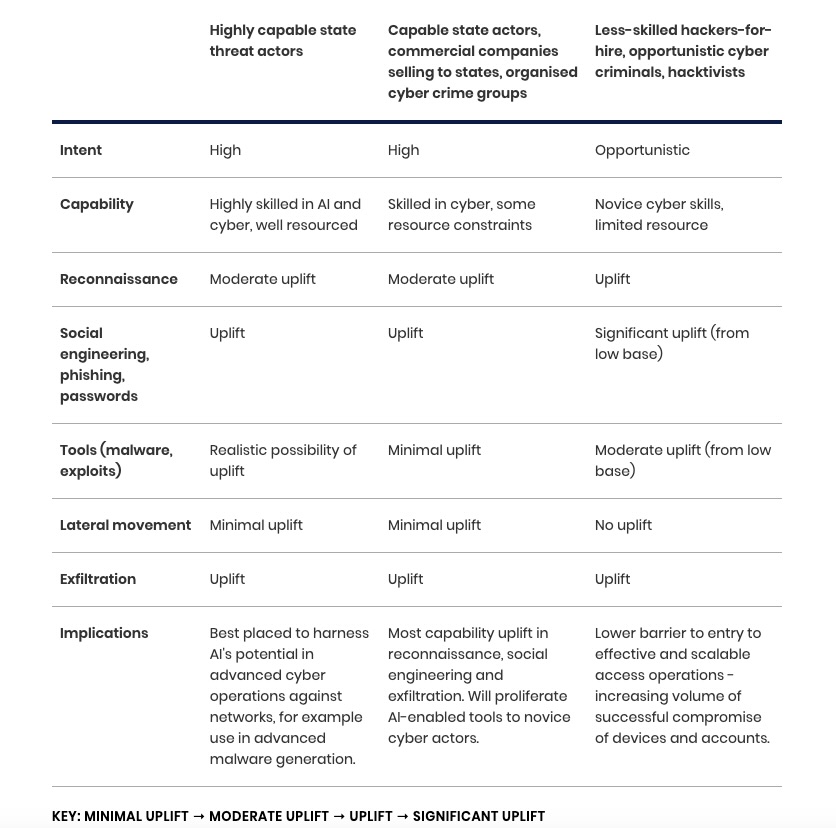
(Source: NCSC’s “The near-term impact of AI on the cyber threat” report, January 2024)
In a companion statement, the NCSC highlighted how AI will likely heighten the already critical threat from ransomware by making it easier in particular for unskilled hackers to launch more effective cyberattacks.
“This enhanced access, combined with the improved targeting of victims afforded by AI, will contribute to the global ransomware threat in the next two years,” the NCSC statement reads.
For more information about how to address AI-powered cyberattacks:
- “Skilling up the security team for the AI-dominated era” (CSO Online)
- “How Zero Trust Can Protect Systems Against Generative AI Agents” (Dark Reading)
- “How to combat AI-produced phishing attacks” (SC Magazine)
PODCAST
Defending Against AI Threats (FBI)
4 - Report: Cyber pros weigh AI security benefits and downsides
A global survey of cybersecurity pros once again shows how they view AI technologies as a blessing and a curse, offering powerful capabilities for cyber defenses and for cyberattacks.
Specifically, the 1,000-plus cyber pros surveyed for the “EC-Council Threat Report 2024” identified these top risks in AI-fueled cyberattacks:
- Automated creation of sophisticated attacks
- Development of autonomous and self-learning malware
- Automated exploitation of vulnerabilities
- Automated phishing and social engineering
- Difficulty detecting and mitigating AI-powered attacks

Meanwhile, here are the main areas where respondents see AI helping cyber defenders:
- Threat detection and forensics
- Anomaly detection
- User behavior analysis
- Malware detection
- Phishing and social engineering detection
“AI has emerged as a double-edged sword in cybersecurity, offering unprecedented defense capabilities and new avenues for attackers,” EC-Council President and CEO Jay Bavisi said in a statement.
Other key findings from the 47-page report include:
- 83% have noticed a shift in attack methods caused by the use of AI
- 66% say they’re not prepared for a potential barrage of AI-driven cyberthreats
- 82% view regular training for incident response as critical for boosting cybersecurity
5 - Insurer: Cyber incidents top business risk rankings
What’s business executives’ main concern going into 2024? That’d be the consequences of suffering a cyber event, according to a report from insurer company Allianz Commercial.
For the third straight year, the “Allianz Risk Barometer” ranks cybersecurity incidents first among business risks. They’re specifically worried the most about data breaches and about cyberattacks against critical infrastructure and physical assets.
Which cyber exposures concern your company most over the next year?
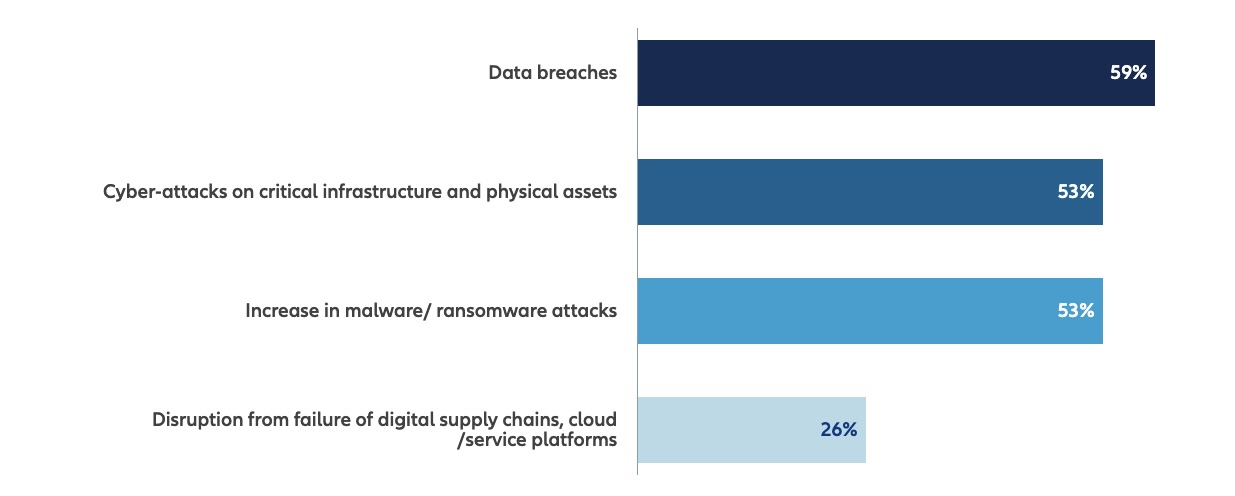
(Source: “Allianz Risk Barometer” report, January 2024)
Factors expected to increase cybersecurity risk for businesses this year include the weaponizing of AI by cyberattackers; weak cyber defenses; lax mobile device security; and the skills shortage among cyber pros, according to the report, based on a global survey of 3,000-plus risk management experts.
Rounding out the top 5 business risk rankings were business interruption; natural catastrophes; changes in legislation and regulation; and macroeconomic developments.
The Top 10 Global Business Risks for 2024
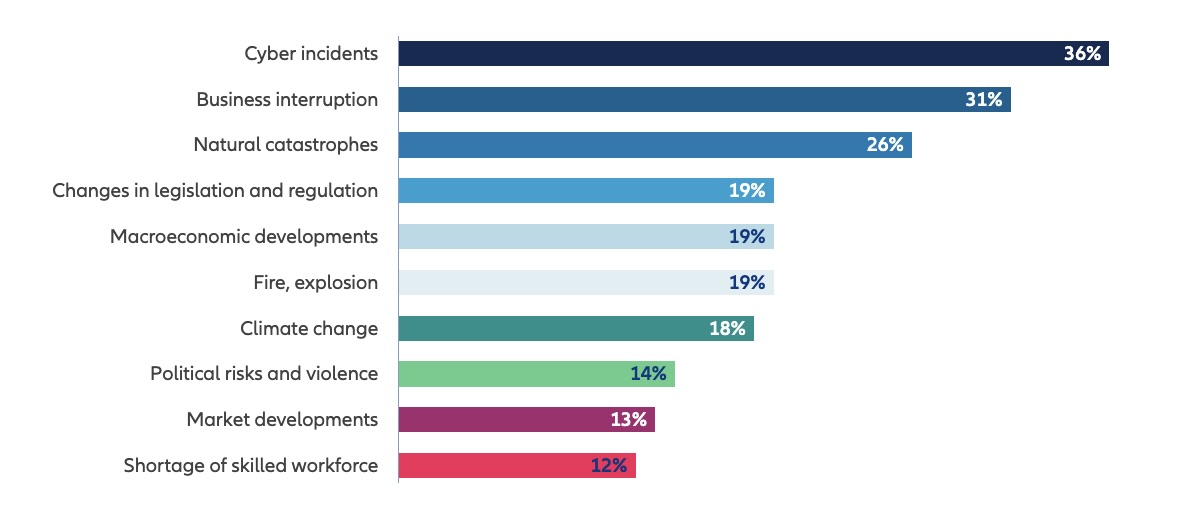
(Source: “Allianz Risk Barometer” report, January 2024)
To get more details, check out:
- The report’s announcement “Allianz Risk Barometer: A cyber event is the top global business risk for 2024”
- The full “Allianz Risk Barometer 2024” report
- The report’s section on cybersecurity risk
- A detailed breakdown of survey results by regions, industries and company size
- The video “The world’s top business risks for 2024”
6 - CISA issues urgent alert on Ivanti bugs
An emergency directive from CISA is requiring all federal agencies in the civilian executive branch to address active vulnerabilities in the Ivanti Connect Secure and Ivanti Policy Secure products.

Specifically, the instructions in the “Emergency Directive (ED) 24-01 Mitigate Ivanti Connect Secure and Ivanti Policy Secure Vulnerabilities” include:
- Implement the directive’s mitigations
- Report indications of compromise to CISA
- Remove compromised products from agency networks
- Follow the directive’s detailed steps for returning the products to service
“Even as federal agencies take urgent action in response to this Directive, we know that these risks extend to every organization and sector using these products. We strongly urge all organizations to adopt the actions outlined in this Directive,” CISA Director Jen Easterly said in the statement “CISA Issues Emergency Directive Requiring Federal Agencies to Mitigate Ivanti Connect Secure and Policy Secure Vulnerabilities.”
To get all the details about these Ivanti vulnerabilities, read the Tenable blog “CVE-2023-46805, CVE-2024-21887: Zero-Day Vulnerabilities Exploited in Ivanti Connect Secure and Policy Secure Gateways.”
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- Malware
- Vulnerability Management


