Ghosts of InfoSec

As National Cybersecurity Awareness Month draws to a close on Halloween, it is a fitting time to reflect on some of the ghosts of infosec.
Friendly and unfriendly ghosts
The ghosts of infosec include both friendly and unfriendly spirits. The friendly ones remind us of the lessons learned and the knowledge we've gained through the decades of our young industry; they also inspire us to look forward and to build on their work. Sadly, we do have quite a few unfriendly ghosts to contend with, from those which are merely troubling to some which are truly terrifying.
Willis Ware understood the significance of computers long before most, saying in 1966:
“The computer will touch men everywhere and in every way, almost on a minute-to-minute basis. Every man will communicate through a computer whatever he does. It will change and reshape his life, modify his career and force him to accept a life of continuous change.”
Decades before it became a popular concern, Ware predicted that increased reliance on computers would present serious privacy issues. He led several committees aimed at safeguarding computer user privacy rights, including the Privacy Protection Commission created by President Ford, which led to the creation of the Federal Privacy Act of 1974.
I won’t dwell on the most terrifying ghosts; the media does a good job of scaring us all with the latest cybersecurity nightmares, from insecure medical devices to default credentials on IoT systems. Those of us in the industry have a wide array of our own hauntings depending on our experiences, from pervasive web application vulnerabilities such as SQL injection to unvalidated inputs to unpatched software and flawed crypto.
Oldies but goodies
There are two reports from the sixties and seventies which I still find valuable, and they also provide good resources for exploring both ends of our ghost spectrum.
The first is the Ware Report (officially titled Security Controls for Computer Systems), a foundational text on computer security which established an understanding of security issues which is still relevant today despite its age and the rapid evolution of computer technology. The Ware report gave us insights including:
…certainly security control will be cheapest if it is considered in the system architecture prior to hardware and software design.
and
User convenience is an important aspect of achieving security control because it determines whether or not users tend to find ways to get around, ignore, or subvert controls.
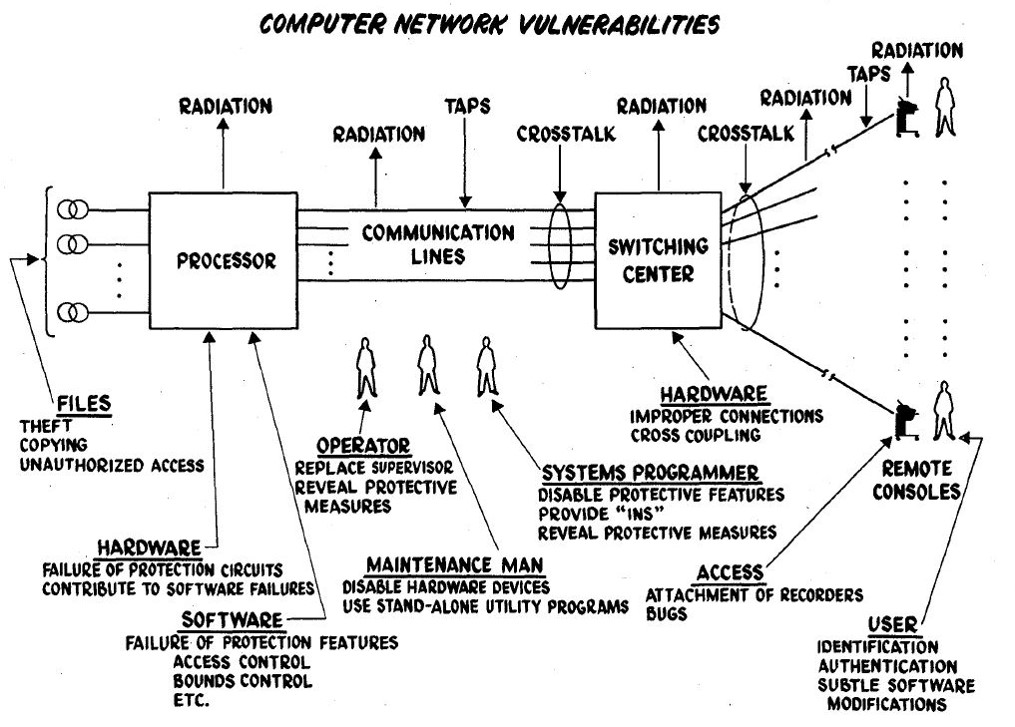
The Ware report also gave us this graphic, which identifies key vulnerabilities:
Figure 3, from Security Controls for Computer Systems
As dated as this is, with a few changed labels, this graphic is almost as accurate today as it was nearly 50 years ago when first published; the critical leakage points are still valid.
Bob Abbott’s many contributions to computing and security include authoring the first set of Privacy and Data Confidentiality policies for the Health Care area (1974) and the development of the first multi-user, multi-tasking operating system for Cray class supercomputers to go into 24X7 operational deployment. He also led a project that produced the first physiological monitoring system for patients recovering from open-heart surgery. Abbott may be best remembered by some as an advisor to the movie Sneakers. The James Earl Jones character in the movie was named Bernard Abbott in a nod to him, and many characters were modeled after members of Bob’s team.
The Ware Report is inspirational; it reminds us of the people who have come before us, and the work they have done; it truly provides a group of “friendly infosec ghosts” who paved the way into the cybersecurity industry. Unfortunately, rereading the report also reminds us of how long we have struggled with some of the fundamental issues of securing information and how much work we still need to do before they will stop haunting us.
Rereading the report also reminds us of how long we have struggled with some of the fundamental issues of securing information
Another early report I find informative is Security Analysis and Enhancements of Computer Operating Systems (authored by Bob Abbott and others), part of the RISOS (Research in Secured Operating Systems) project. Although this report has not aged as well as the Ware Report, it is still informative. This report outlined seven key operating system security flaws covering issues including parameter validation, logic flaws, identification/authentication/authorization failures, and more that any modern student of software security would recognize. As before, this shows us both good work that we can continue to build upon and ghosts we have yet to exorcise. In spite of being another reminder of flaws we have yet to resolve, it is good to consider that as an industry we have made great strides in driving some of these ghosts out of our operating systems – unfortunately many have moved to the application layer and continue to haunt us there.
Moving forward
Admiral Grace Hopper was a computer pioneer whose career spanned decades, from the early days of programming with patch cables and later with DIP switches to her invention of the first programming language compiler. One of Adm. Hopper’s most notable contributions to the field is the term “debugging,” which comes from her solving a computing “bug” by removing a moth from an electromechanical relay in a computer system. Her importance to computing in the US Navy was so great that the first two times she retired, the Navy brought her back – she finally retired as a Rear Admiral in 1986.
As we close the door on another National Cybersecurity Awareness Month, we must remember how far we have come, and how far we have yet to go. As bad as some of the poltergeists are, let’s try to focus on the friendly ghosts that remind us of how far we have come – from pioneers such as Admiral Grace Hopper, Willis Ware, Bob Abbott, and many more; and the foundational work they did.
We must remember how far we have come, and how far we have yet to go
Isaac Newton is often credited with the saying “If I have seen further it is by standing on the shoulders of giants.” All of us working to improve the state of cybersecurity stand on the shoulders of many giants; remember those ghosts and maybe we can all get a good night’s sleep on this All Cybers’ Eve.
- Personal security