How to Remediate Risk to Critical OT/IoT Systems without Disrupting Operations

Find out how adopting a proactive approach to secure your operational environments can help you reduce risk and eliminate downtime.
For a long time, operational technology (OT) environments were considered isolated and "air-gapped," supposedly immune to the cyber threats plaguing the IT world. In reality, that hasn't been the case for many years. IT and OT systems are inextricably linked.
Sophisticated cyber attacks on critical infrastructure, manufacturing, power grids, data centers and other sectors demonstrate that securing OT isn't just a best practice — it's a national and economic imperative. Most attacks originate on the IT side, and often go undetected by traditional, siloed OT security tools.
OT security is the CISO’s frontier
It can be daunting for CISOs and SecOps teams to find themselves responsible for OT security. You’re inheriting responsibility for systems you don’t fully understand — programmable logic controllers (PLCs), supervisory control and data acquisition (SCADA) systems, industrial control networks. All with their unique terminology, devices, protocols and operational practices. Additionally, you’re working with operations teams who are focused on maintaining operational continuity and “keeping-the-machines-running” 24x7. They can’t afford any downtime.
Perhaps you're new to the world of OT, or you've recently joined a team where OT security is now a core part of your responsibilities. You might be asking yourself, "What even is a PLC?" or "How can I improve my OT security knowledge?" You're not alone. Many security professionals are navigating the unique challenges of securing operational environments for the first time.
We understand that organizations need fewer, more integrated tools, and not a proliferation of them. To bridge this gap and address the evolving threat landscape, Tenable is helping organizations fundamentally shift their OT security approach.
We continuously invest in “deep core” OT security capabilities for asset discovery, risk-based vulnerability management, continuous monitoring, and more. All of our solutions, including Tenable OT Security, are backed by Tenable Research and industry-leading vulnerability intelligence, many years of experience and thousands of networks secured.
But we're always looking ahead to the future, paving the way forward with Tenable One. Looking to empower security teams with a unified platform to assess, prioritize and remediate risk across the entire attack surface — from cyber-physical systems (OT, IT, IoT), identities, web apps and cloud to AI tools, and everything in between.

The importance of mitigating OT risk earlier and faster
Let’s start with a scenario that is all too familiar for security teams concerned with OT risk:
A security analyst identifies a critical vulnerability or a misconfiguration already on a PLC that controls a key part of the production line. In line with typical procedures, they go to the operations team to request the device be taken down soon for patching.
The response? “No way! We’re not doing that.”
The operations team simply cannot afford unplanned downtime. This creates a dangerous stalemate: the security team faces a known risk on a critical asset that can’t be immediately remediated, and the operations team is forced to accept the risk to keep business-critical systems online. As a result, risk remains, and the production line, supply chain and overall operational continuity are all at risk.
As shown in the graphic below, attackers look to move laterally through your environment anywhere they can gain a foothold in your IT and OT systems, including by exploiting unpatched IT-side vulnerabilities (e.g., CVEs, misconfigurations) or taking advantage of identity exposures to gain access downstream to critical assets, data and processes.
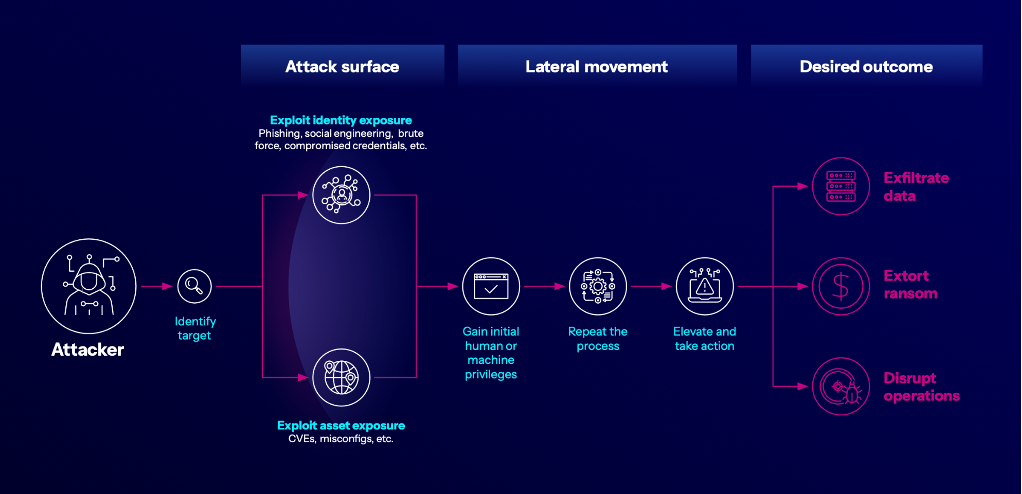
It’s not just about being proactive; it’s about finding an efficient way to reduce risk quickly without disrupting operational continuity. To do this, security teams need the right tools and processes in place to identify and fix the root cause of OT risk earlier in the attack chain — often on the IT side of the house.
The goal is to answer the most pressing question: "How can you reduce my risk exposure today without disrupting critical operations and physical processes?"
Unified exposure management for OT security
Traditional, siloed security tools simply aren't equipped for proactive security. They provide fragmented views that make it difficult to connect the dots between IT and OT risk, and everything in between.
That’s where exposure management comes in. It transcends silos, giving you a unified view of your entire attack surface — so you can focus on addressing the cyber risks that are most likely to be exploited in your environment. With exposure management, you can proactively address the preventable, exploitable and most impactful risks much earlier.
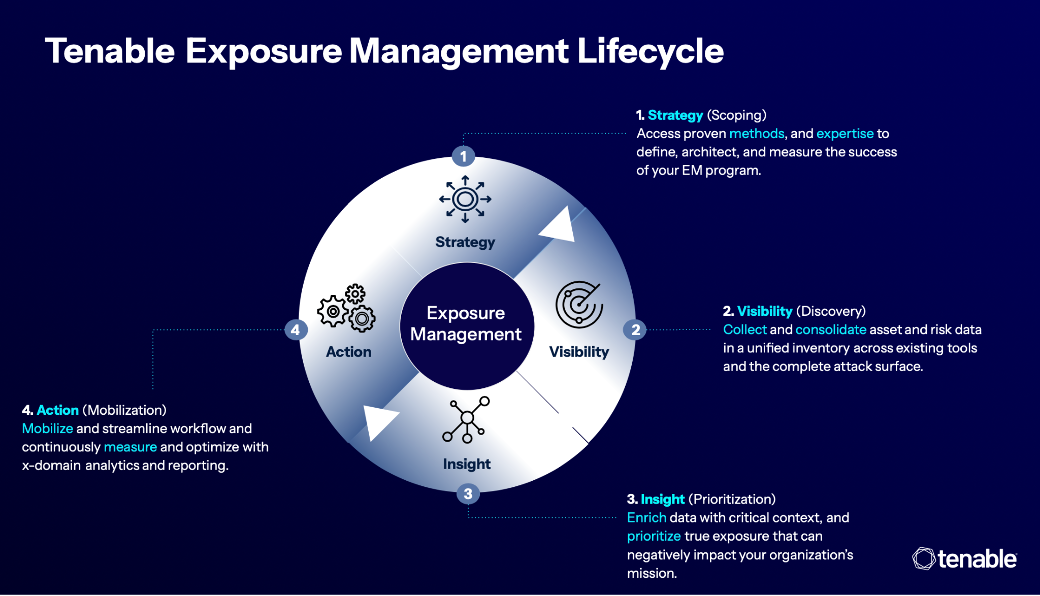
A proactive exposure management approach, aligned with the Tenable Exposure Management Lifecycle shown below, enables you to identify and mitigate critical cyber exposures before they’re exploited, unlike reactive approaches that only alert you after a threat manifests.
Unlock a stronger security posture with the Tenable Exposure Management Lifecycle, which combines Strategy, Visibility, Insight and Action to continuously identify, prioritize and remediate your organization's most critical exposures.
Remember that risk alert we were talking about on a PLC? With traditional siloed security tools your only option would be to wait for the next scheduled maintenance interval (probably in several months) to address the issue. With Tenable, you can trace potential attack paths from that vulnerable PLC to other systems in your environment and take immediate action to cut off their exposure, reducing risk well before that scheduled maintenance window.
Built-in capabilities such as Attack Path Analysis, MITRE ATT&CK Mapping and Network Maps allow you to instantly visualize the entire attack chain:
- The PLC is connected to an engineering workstation.
- That workstation has a known, exploitable vulnerability and is misconfigured.
- The workstation can be accessed by a “remote access user group.”
- One of the users on that group is a domain administrator account whose credentials were recently compromised.
Suddenly, you can see the full blast radius. The problem isn't just a vulnerability on a PLC; it's a clear, exploitable path from an IT identity compromise to the potential shutdown of your core operations. You've found the IT-side choke point that you can fix now.
Now, instead of burdening your OT team with unplanned downtime, you've mitigated the risk while giving them cover to keep systems up and running until the next scheduled maintenance window. Even better: next time, the operations team won't cringe when you contact them about a vulnerability — they’ll appreciate the essential coverage the security team provides.
Additionally, AI-powered security recommendations help surface timely insights and automate time-consuming investigations by delivering immediate, intelligent answers and one-click guidance. This simplifies a complex investigation down to a clear, actionable remediation plan.
For example, looking at the attack path, a SecOps analyst can ask simple, direct questions:
- "What is this PLC device and what does it do?”
- “Who was trying to attack it? And how?"
- “Has the Cybersecurity and Infrastructure Security Agency (CISA) flagged this device model vulnerability or advisory?"
- “What actions can I take right now to break this attack path and reduce risk today?"


See Tenable AI Aware in action →
Breaking down OT/IT silos and building new levels of trust
Adopting a unified approach to managing exposure does a lot more than reduce risk; it fundamentally changes the dynamic between security and operational teams. The two groups often feel like they don’t speak the same language. Exposure management provides a powerful bridge, creating a shared language of immediate and timely risk reduction.
The conversation changes from:
Security: "You have to take down this critical asset right now."
Operations: "No."
To a collaborative partnership:
Security: "We found a critical risk to a PLC. We have already mitigated the immediate threat by fixing a problem on our side. The asset is protected for now, but let's work together to schedule a patch during the next maintenance window."
Operations: "Excellent news, we’ll buy the pizza this time!”
With exposure management, security teams are empowered with a faster triage and clear and faster remediation paths, while operational teams benefit because they can maintain operational continuity.
Tenable’s commitment to unified security across the attack surface
Without deep visibility into your OT environment, your security strategy is incomplete. You're essentially flying blind in a significant portion of your operational landscape. True cyber resilience comes from a holistic understanding of your attack surface. That’s why our vision for exposure management includes OT security as a key pillar of our product portfolio.
Tenable has an unmatched framework for reducing tool sprawl and delivering a complete, unified view of risk. This is vital if you want to assess and mitigate risk across your entire organization. By unifying data from IT, OT, IoT, cloud and identities, we’re able to deliver a seamless workflow, complete asset inventory and context-aware prioritization that legacy OT security tools and point solutions can’t match. And with more than 300 third-party integrations, we’ve built the industry’s most open platform for exposure management to date.
Explore all Tenable integrations →
By focusing on exposure and providing a unified platform to see, predict and act on threats, we’re helping our customers move beyond the limitations of the past and safeguard their most critical assets from the threats of tomorrow.
Learn more
- Dive deeper into the challenges and solutions for securing OT with our eBook “Blackbox to blueprint: a security leader’s guide to managing OT and IT risk”.
- Learn more about Tenable OT Security and how it fits into your cybersecurity roadmap.
- Explore our complete Tenable One Exposure Management Platform, offering scalable security solutions for the entire attack surface.
- Exposure Management
- OT Security



