Threat Modeling: What You Need to Know About Prioritizing Attacks and Vulnerabilities

Threat modeling gives vulnerability management teams a good understanding of how attacks work, enabling them to focus prioritization efforts around the bugs most likely to affect their environment.
The importance of threat modeling in assessing security postures is a given nowadays. The vulnerability view, while it does play a central role, is only one part of an assessment. It’s not enough to pinpoint which vulnerabilities or attack vectors are the most relevant at a given time. Taking into account the characteristics of individual attacks and the strategies of attackers enables defenders to prioritize. Instead of defending against all vulnerabilities (which can number in the hundreds and thousands), defenders can prioritize their efforts to focus on a select number that the attacker needs to breach the system.
In this blog post, I will share a few notes on how attacks are carried out, links to vulnerabilities, and how the right threat model can save the day.
Threat modeling: vulnerabilities vs. attacks
Threat modeling is the formal process of identifying and ranking the threats most likely to affect your environment. Typically, there are two views to threat modeling:
- the vulnerability view, in which system vulnerabilities, either taken individually or combined, define the technical exposure to attacks; and
- the attacker and threat landscape view, in which the modeling takes into account the threat landscape, in the form of attack instances, and attacker strategies.
These models are typically represented through attack graphs, game theory or decision analysis. Regardless of the modeling approach, our interest here is to define the threat-modeling steps most likely to make a difference when it comes to protecting your system.
Targeting all known vulnerabilities that an attacker may exploit is usually pointless. Out of tens of thousands of vulnerabilities, only a fraction is actively exploited in the wild. In addition, it has been shown that vulnerability exploitation can be described by a heavy tail distribution, which basically means a very small fraction of vulnerabilities is responsible for orders of magnitude more attacks than the remaining majority.
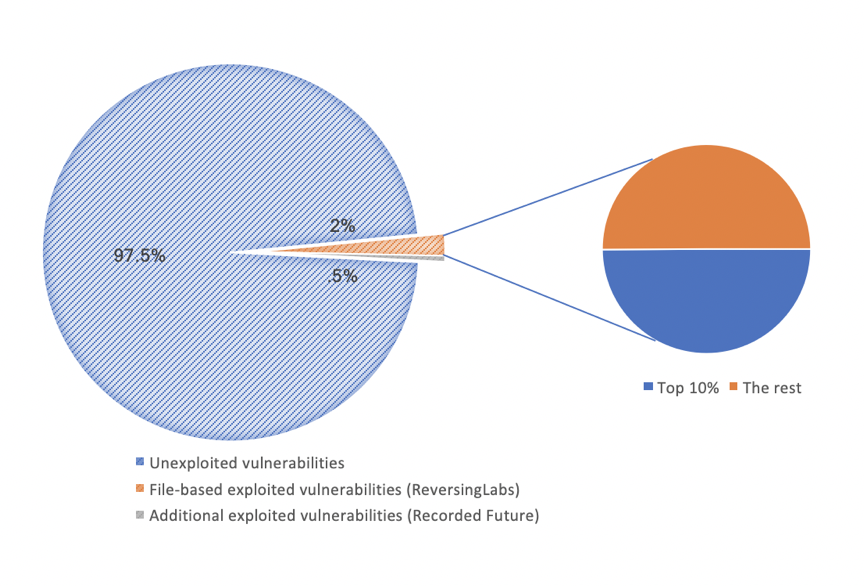
A good example here would be exploit kits, which drive millions of attacks, yet use only a dozen vulnerabilities each at a maximum. Data from Tenable and ReversingLabs, from January 1 through May 5, shows only 2 percent of all known and detected vulnerabilities were seen in ReversingLabs's threat detection feed (file-based malware). Additionally, the top 10 percent of CVEs (out of 638) from that feed is responsible for 50 percent of exploit detections.
Additional data from Recorded Future, including a broader range of cyber attacks — such as fileless or Web attacks — shows a further 172 CVEs being exploited in the same period, which brings the total to 2.5 percent of all known and detected vulnerabilities in Tenable data. This shows that it’s unrealistic to assume attackers can choose any available vulnerability or path to compromise.
There is no 'one-size-fits-all' attack strategy, nor defender strategy for that matter. Outside of the 'Attacks-as-a-Service' model, using pre-existing mechanisms — such as the above-mentioned exploit kits — or an existing infrastructure controlled by cybercriminals to launch distributed denial of service (DDoS) attacks, for instance, the attack generation process is usually dynamic and made-to-measure. In fact, attackers might need to re-engineer their attack strategy if nothing in their toolbox works on a target environment, which might translate to a lot more effort in terms of reconnaissance, enumeration or even exploit modification and engineering.
It’s equally unrealistic to assume attackers are all-knowing about their targets and can choose whichever attack strategy they believe is best.
A typical attack scenario might, for instance, involve a watering hole attack, a phishing attack or password spraying to establish the initial foothold. Once inside, additional effort is required to identify the network and system configuration visible from there and understand which attacks are needed to move to the next target.
Even though no two attacks are exactly alike, there are similar tactics, techniques and procedures (TTPs) that attackers use. These should be well understood on the defender side. The MITRE ATT&CK framework offers a good high-level reference.
Leveraging real-world and timely threat intelligence and attacks knowledge is essential to define (and narrow down) the search space to highly likely and high impact threats for a given environment.
Steps for Threat Modeling
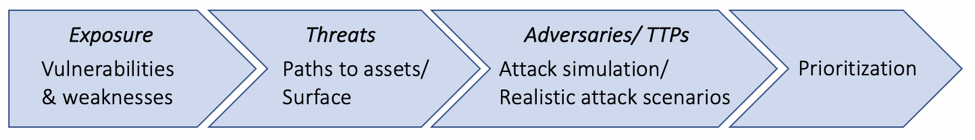
The main question, from the defender perspective, remains “how to decide which vulnerabilities to fix first?” Starting with a given technical exposure, i.e. exploitable vulnerabilities and weaknesses on a system, the basic process would be to identify attack scenarios and characteristics, based on known attack strategies and threat intelligence reports. This would narrow down the initial set to a much smaller number of vulnerabilities that are more likely to lead to realistic attacks on that environment.
Threat modeling would then require the following basic steps:
- Identify system vulnerabilities and weaknesses.
- Identify attack paths against your assets, based on these vulnerabilities and weaknesses, taking into account existing countermeasures and safeguards.
- Identify realistic attacks that can leverage existing vulnerabilities and weaknesses on those paths, using both generic and timely knowledge about threats and threat actors.
- Prioritize risks based on impact and asset/ application criticality.
Under this modeling, the defender is able to reason about the attackers’ ability, not only to find an initial entry point, but also to do further reconnaissance, enable persistence, escalate privileges, move laterally and so on, which could be aligned with the MITRE ATT&CK framework.
Ideally, a threat model is enhanced by emulating TTPs used by adversaries and carried out by red teams. This can also be done by mapping those TTPs along the attack surface without necessarily carrying out real-world campaigns. The main advantage to real-world campaigns, however, is taking into account the human factor (employees’ skill gaps) and how the company and blue teams react (mainly reflected by metrics such as Time to Detect and Time to Mitigate).
The appearance of a new vulnerability might not carry any weight on the overall model, in terms of scenarios and risks. If it does, however, the available description and severity, combined with threat intelligence activity, will estimate attack likelihood and impact factors to update the model. It is then imperative for security teams, responsible for assessing security postures, to have a good understanding of how attacks work, keep an open eye on the latest reports and make sure they understand how adversaries are operating and changing their attacks.
Most vulnerability management practitioners understand the importance of risk-centric vulnerability prioritization and remediation. The main focus currently is on imminent (and most of the time, commoditized) attacks, which, in fact, should be the first priority. A more efficient threat model, based on the steps above, will take defenders further by including relevant advanced attacks and continuously assessing the threat landscape for more effective overall risk reduction.
Learn more:
- Read the SecureITSource article Beware of This New “As-a-Service"
- Get up to speed on the MITRE ATT&CK framework
- Visit Tenable’s Predictive Prioritization webpage at https://www.tenable.com/predictive-prioritization
- Security Frameworks
- Threat hunting
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning


