WEF Report: Cyberattacks Rank Just Below Climate Change as an Existential Threat

The vast majority of respondents to the World Economic Forum’s Global Risks Perception Survey expect cyberattacks against infrastructure and cybertheft of money/data to increase in 2020. Here’s why you should care.
It’s no small irony that the publication of the Global Risks Report 2020 from the World Economic Forum (WEF) on January 15 happened to follow closely on the heels of one of the most alarming Microsoft Patch Tuesday announcements we’ve ever seen.
The Microsoft disclosure of CVE-2020-0601 on January 14 hits at the very trust we have in today's digital computing environments — trust to authenticate binaries and trust that our ciphered communications are properly protected. The flaw would enable an attacker to exploit how Windows verifies cryptographic trust, enabling them to deliver executable code and making it look like it came from a trusted source. You can imagine its use in ransomware and phishing attacks on unpatched systems.
Given the proliferation of ransomware and phishing attacks in 2019, it comes as no surprise to see the WEF report rank data fraud/theft at No. 6 and cyberattacks at No. 7 in its list of top 10 long-term risks in terms of likelihood over the next 10 years. These risks outrank water crises, global government failures and asset bubbles as causes of concern for WEF survey respondents. In terms of potential impact, the top 10 list ranks information infrastructure breakdown at No. 6 and cyberattacks at No. 8, with the latter cited as the second most concerning risk for doing business globally over the next 10 years.
The report is based on the WEF’s Global Risks Perception Survey, which reflects responses from 800 members of the Forum’s diverse communities. The report identifies two specific types of cyberattacks in its list of top 10 short-term global risks: attacks against infrastructure and theft of money/data. More than three quarters of respondents (76.1 percent) expect cyberattacks against infrastructure to increase this year, while 75.0 percent expect cybertheft of money/data to increase.
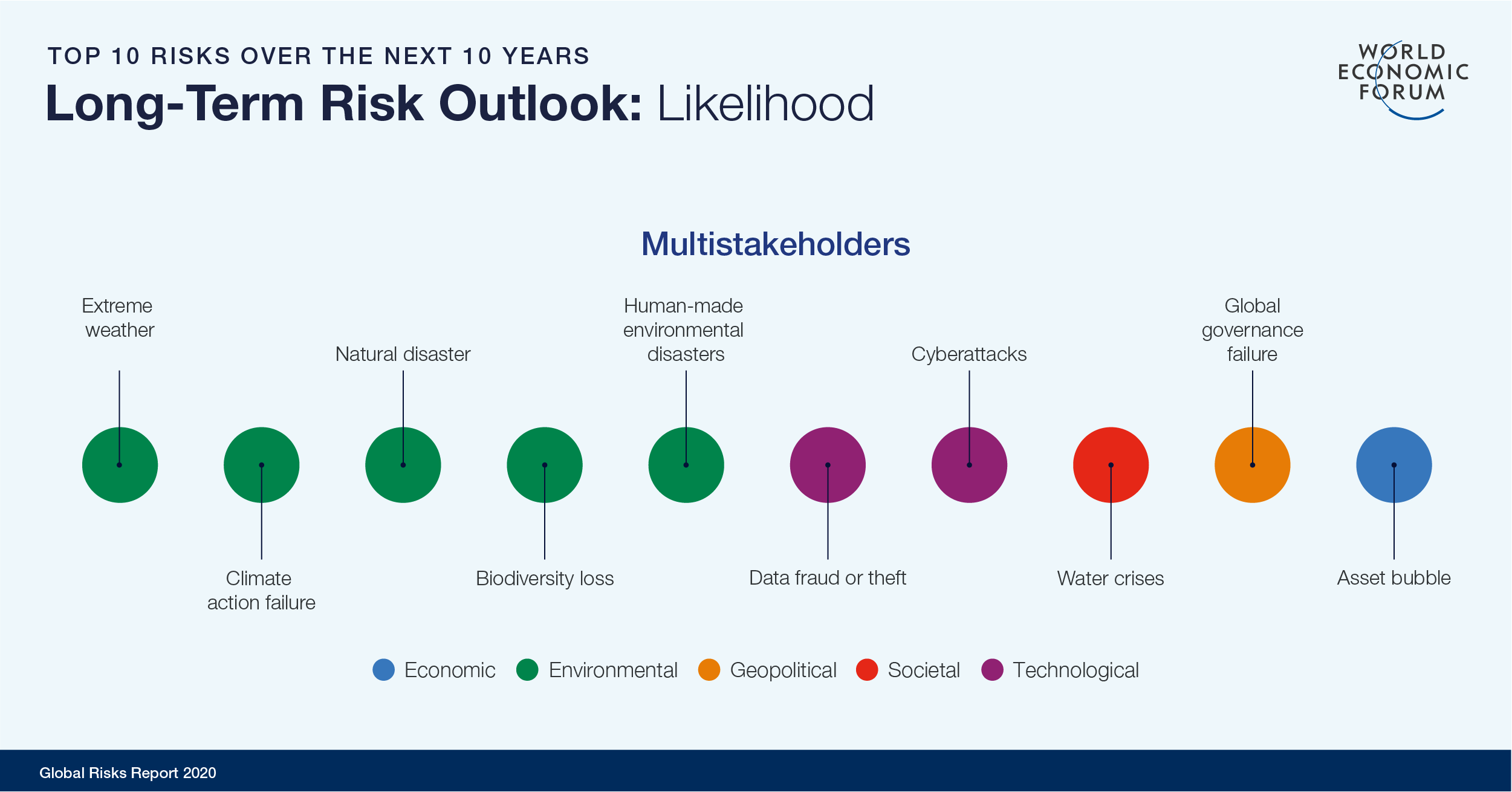
Image: The World Economic Forum Global Risks Report 2020
Attacks on critical infrastructure are particularly concerning when we consider how the convergence of IT and operational technology is expanding the attack surface. Norsk Hydro reported that it lost more than $50 million in its first quarter of 2019 following the LockerGoga attack. In recent years, losses from Shamoon, WannaCry and NotPetya were in the billions. If the financial losses aren’t enough, attacks on critical infrastructure also bring the potential for enormous human costs. The loss of power or water services have obvious consequences for human life, but we also need to consider how malicious tampering of operational controls across public and private sectors can change ingredients in medications, foods, beverages or manipulate critical components like automobile airbags or transportation logistics.
The WEF Global Risk Report, which was first issued in 2007, can be seen as a reflection of the evolving importance business leaders place on cyber risk. Between 2012 — when cyberattacks first appeared in the list of top five risks in terms of likelihood — and 2017, cyberattacks and data theft dropped in and out of the top five lists in terms of likelihood. This is the first year since 2017 that neither concern made the top five list of likely risks. We interpret this year’s top five as a reflection of the seriousness of climate issues, rather than an indication of any improvements in global cybersecurity since last year’s report.
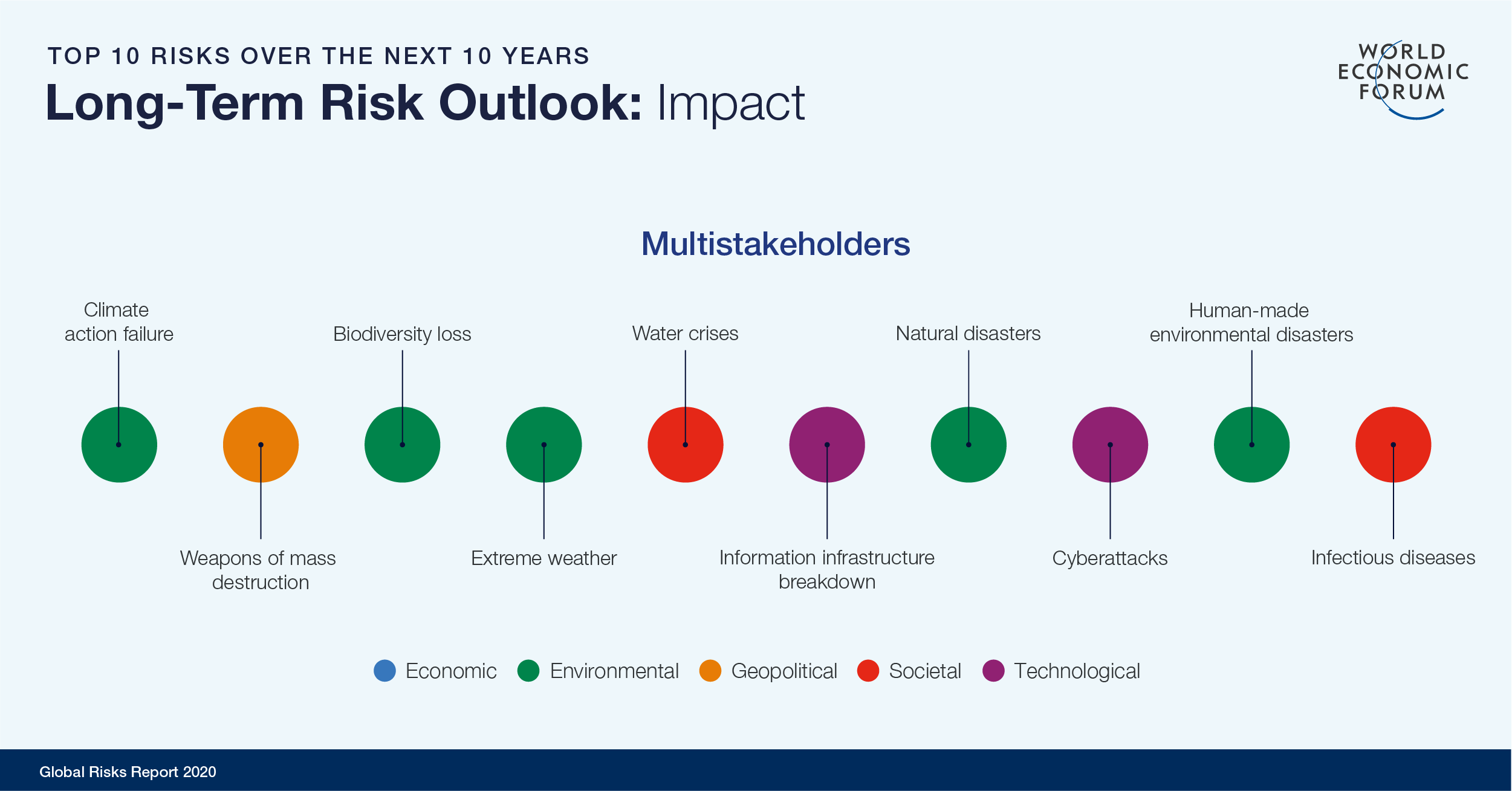
Image: The World Economic Forum Global Risks Report 2020
CVE-2020-0601, the critical Microsoft CryptoAPI flaw, serves as a timely case in point. This is a serious vulnerability and, with POCs shared within hours of the announcement, we fully expect to see it exploited in the wild in the coming weeks and months. While we applaud the disclosure process followed by the U.S. National Security Agency and the rapid response to the vulnerability from Microsoft, we nonetheless expect to see continued attacks over the course of the year among organizations that do not patch their systems quickly.
We hear time and again from our infosec customers about the difficulties they have in getting their business leaders to prioritize cybersecurity and take the necessary steps to treat cyberattacks as an existential threat, ranking just below total environmental collapse. We hope this blog post gives you the ammunition you need to make a case for implementing a risk-based approach to cyber exposure management.
If the WEF report findings aren’t enough, here are some other data points to consider:
- For the first time, cyber incidents are ranked as the most important business risk globally among the 2,700 experts surveyed in 100 countries for the 9th annual Allianz Risk Barometer, supplanting business interruption as the No. 1 concern. Seven years ago, cyber risk ranked 15th, with only 6 percent of survey respondents citing it as an important business risk.
- Nearly two thirds (62 percent) of global executives rank cyberattacks and threats as one of their organization’s highest risk-management priorities in 2020, according to the 2019 Marsh & McLennan Global Cyber Risk Perception survey of 1,500 business executives.
- Cybersecurity ranks second only to the cloud when it comes to digital transformation investment priorities, according to Altimeter’s State of Digital Transformation 2018-2019 report, which is based on a survey of 554 business and IT professionals in North America, Europe and China.
Yet, even as cyber risk has become more of a priority for organizations in recent years, the Marsh & McLennan report finds that confidence in an organization’s ability to manage the risk has declined. In addition, fully half of respondents said cyber risk is almost never a barrier to the adoption of new technology, even though 23 percent said that, for most new technologies, the risk outweighs potential business benefits.
The WEF 2020 Global Risks Report demonstrates how crucial it is for organizations to approach cyber risk with the same degree of analysis and consideration they apply to other existential threats. To that end, it’s incumbent upon all of us to learn what it means to take a cyber-first approach to all major business decisions.
Efforts like the Microsoft Cybersecurity Tech Accord are an important step toward fostering a cyber-savvy future for organizations around the world. None of these issues can be solved in a vacuum. As with climate change, addressing the existential threat of cyberattacks requires a concerted and sustained effort across the public and private sectors. I’m honored to have had the opportunity to discuss these challenges and more on a Cybersecurity Tech Accord panel session today during the World Economic Forum in Davos, Switzerland. It served as an open forum to discuss industry responsibility and how we must collectively work together to solve 21st century cybersecurity challenges.
Learn more:
- Download the WEF Global Risks Report 2020
- See what the Cybersecurity Tech Accord is all about
- Read the blog CVE-2020-0601: NSA Reported Spoofing Vulnerability in Windows CryptoAPI
