by Sharon Everson
July 13, 2017
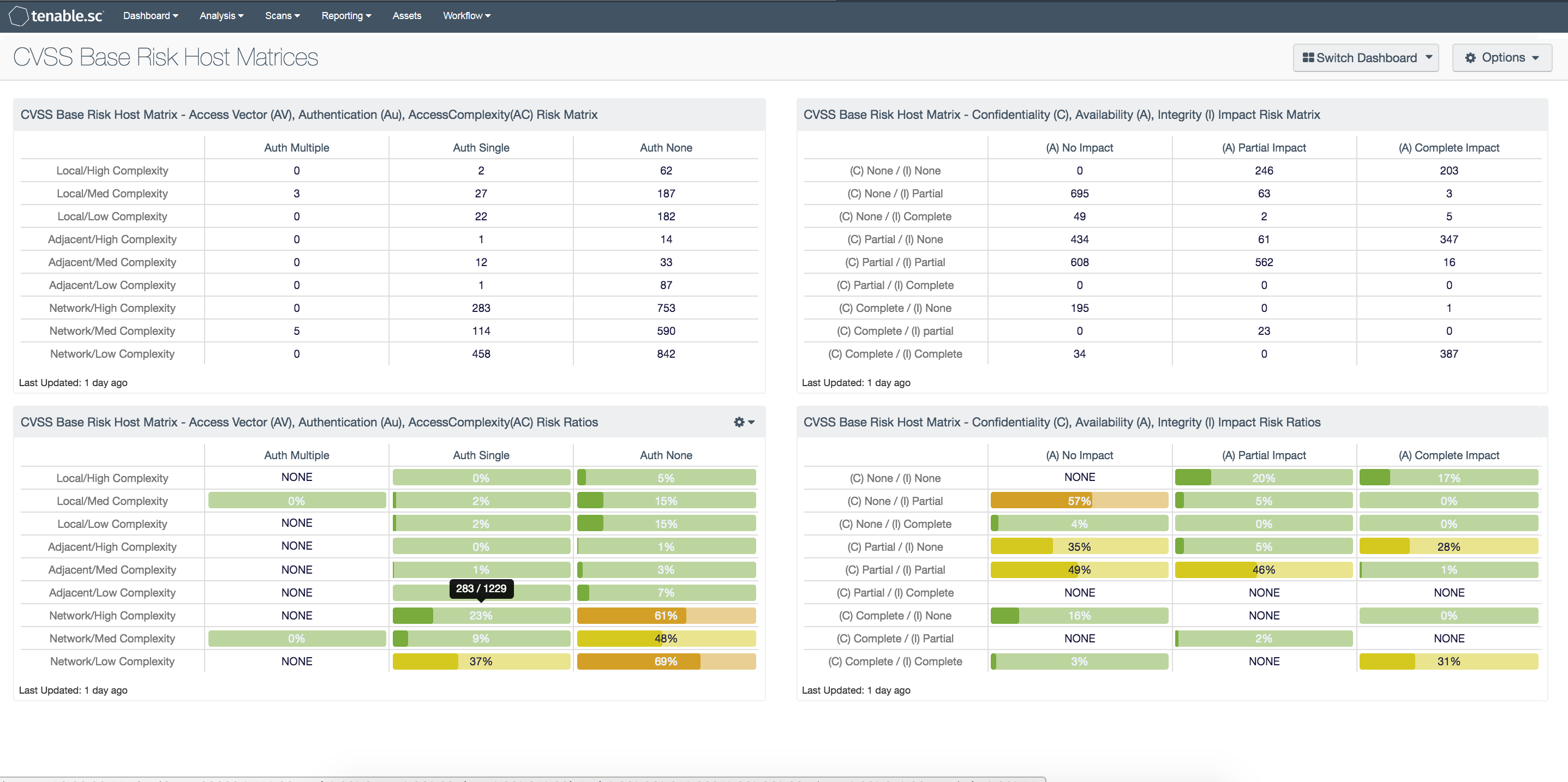
When performing a detailed risk analysis, the use of risk matrices is a common practice. The Forum of Incident Response and Security Teams (FIRST) created the Common Vulnerability Scoring System (CVSS) system to normalize the methodology of analyzing risk. The CVSS is a free and open industry standard for assessing the severity of computer system security vulnerabilities. CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to threat. The CVSS assessment measure three area of concerns: Base Metrics, Temporal Metrics, and Environmental Metrics
The “Base Metric” is the detailed focus of this dashboard. The Base metric group represents the inherent characteristics of a vulnerability that are constant over time and across user environments. Among other parameters, Base scoring is computed from confidentiality, integrity, and availability impact assessments. Base scoring serves as the foundation of the CVSS assessment that is modified by the Temporal and Environmental metrics for a final CVSS risk score. The Base score has the largest bearing on the final score and represents vulnerability severity.
The matrices are separated by the access and impact CVSS base metrics groups. The Access Vector (AV), Access Complexity (AC), and Authentication (Au) metrics are on the left side. The Confidentiality (C), Integrity (I), and Availability (A) metrics are on the right side. The AV, AC, and Au metrics measure how the vulnerability is accessed and whether or not special conditions are needed before the vulnerability can be exploited. The triad includes the C, I, & A metrics which measure the impact of the vulnerability. A key factor in the triad is that even though a vulnerability may breach integrity, the confidentiality or availability of the data may not be impacted.
This dashboard is comprised of four risk analysis matrices. The top two matrices provide analysis of hosts with vulnerabilities inherent of the CVSS metric, while the bottom two provide analysis of the percentage of total hosts that are found to have the designated risk level. The components are filtered by using the “CVSS_Vector” filter and “Severity” level ranging from low to critical. The CVSS_Vector is always arranged in sequential order, following this sequence:
- Access Vector (AV): [L,A,N]
- Access Complexity (AC):[H,M,L]
- Authentication (Au):[M,S,N]
- Confidentiality (C):[N,P,C]
- Integrity (I):[N,P,C]
- Availability (A):[N,P,C]
The Confidentiality, Integrity, and Availability metric values are common for all the metrics. The metric values are:
None (N) - There is no Confidentiality, Integrity, or Availability impact to the system.
Partial (P) – The system’s Confidentiality, Integrity, or Availability could be considerably impacted. An example of the impact would be if confidentiality is compromised and sedative information is disclosed. The attacker may have access to some system properties, but control over the system was not obtained, or the loss of information is limited. An example is a vulnerability that divulges routing tables in a compromised router.
Complete (C) – The system’s Confidentiality, Integrity, or Availability could be completely compromised. An example of such an impact is if information disclosure resulted in all system files being revealed, or if unfettered arbitrary command execution were to be allowed.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends.
The dashboard requirements are:
- Tenable.sc 5.5
- Nessus 8.6.0
- Nessus Network Monitor 5.9.0
Tenable's Tenable.sc Continuous View® (Tenable.sc CV™) provides continuous network monitoring, vulnerability identification and security monitoring. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities and new types of regulatory compliance configuration audit files. Tenable continuously analyzes information from our unique sensors, delivering continuous visibility and critical context, and enabling decisive action that transforms a security program from reactive to proactive. Active scanning periodically examines the applications on the systems, running processes and services, web applications, and configuration settings. With these tools, analysts can better analyze risk by utilizing the CVSS metrics from the environment. Tenable enables powerful, yet non-disruptive, continuous monitoring that will provide organizations with the information needed to reduce risk within the enterprise.
The dashboard components are:
CVSS Base Risk Host Matrix - Access Vector (AV), Authentication (Au), Access Complexity (AC) Risk Matrix: This matrix provides analysts with a traditional risk matrix using the CVSS Base Metrics. The cells in the matrix contain the number of hosts with vulnerabilities with applicable risk vector. For each Access Vector (AV) / Access Complexity (AC) combination, the number of hosts in each Authentication (Au) category is given.
CVSS Base Risk Host Matrix - Access Vector (AV), Authentication (Au), Access Complexity (AC) Risk Ratios: This matrix provides a ratio analysis using a traditional risk matrix comprised of the CVSS Base Accessibility Metrics. The cells in the matrix contain the number of hosts with vulnerabilities with applicable risk vector. For each Access Vector (AV) / Access Complexity (AC) combination, a ratio is provided for the Total IP’s with a low, medium, high and critical severity over the respective Authentication (Au) category.
CVSS Base Risk Host Matrix - Confidentiality (C), Integrity (I), Availability (A) Impact Risk Matrix: This matrix provides analysts with a traditional risk matrix using the CVSS Base Metrics. The cells in the matrix contain the number of hosts with vulnerabilities with applicable risk vector. For each - Confidentiality (C) / Integrity (I) combination, the number of hosts in each Availability (A) category is given.
CVSS Base Risk Host Matrix - Confidentiality (C), Integrity (I), Availability (A) Impact Risk Ratios: This matrix provides a ratio analysis using a traditional risk matrix comprised of the CVSS Base Accessibility Metrics. The cells in the matrix contain the number of hosts with vulnerabilities with applicable risk vector. For each Confidentiality (C) / Integrity (I) combination, a ratio is provided for the Total IP’s with a low, medium, high and critical severity over the respective Availability (A) category.