by Sharon Everson
June 18, 2020
The National Information Assurance (NIA) Policy v2.0 is associated with the State of Qatar’s Ministry of Transport and Communications (MOTC). This policy was developed to help agencies and entities in the State of Qatar enable a full-fledged information security management system within their agency. These entities need to show compliance with the NIA Policy v2.0 through an annual audit by a certification body. This policy includes a series of security governances and technical controls grouped into security domains that cover control areas that an agency needs to implement as baseline security to be compliant with the NIA Policy and in accordance with the NIA Manual.
Tenable.sc provides a series of audit checks against the CIS benchmarks. These benchmarks provide agencies with a set of generally accepted best practice guidelines to better harden their information systems. By implementing these hardening guidelines, agencies can meet and exceed many compliance standards. The NIA standard requires that agencies implement hardening guidelines according to the NIA policy. Tenable.sc uses the CIS audit files with a cross-reference to map these NIA controls. This mapping provides the security and risk analyst with a deep dive into measuring their compliance with NIA.
Using this dashboard, the analyst can readily investigate and remediate any audit failures. Audit checks that are out of compliance (shown in red) need to be reviewed in case the configured check does not align with the policies in place. For example, if the password length policy says 8 – 15 characters is compliant, a configured policy of 25 characters will be marked noncompliant even though the policy is certainly very secure.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment.
The dashboard requirements are:
- Tenable.sc 5.14.1
- Nessus 8.10.1
- Compliance data
- Audit files containing NIAv2
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provide the ability to Discover hardware assets, for a more details analysis. Not only detecting risks based on Common Vulnerabilities and Exposures (CVE), but also using more advanced methods such a Vulnerability Priority Rating (VPR). Tenable.sc provides customers with a full and completed Cyber Exposure platform for completing an effective Information Security Management System program. Tenable.sc supports configuration audits for more technologies than any other vendor, including operating systems, network devices, hypervisors, databases, web servers, and critical infrastructure.
This dashboard contains the following components:
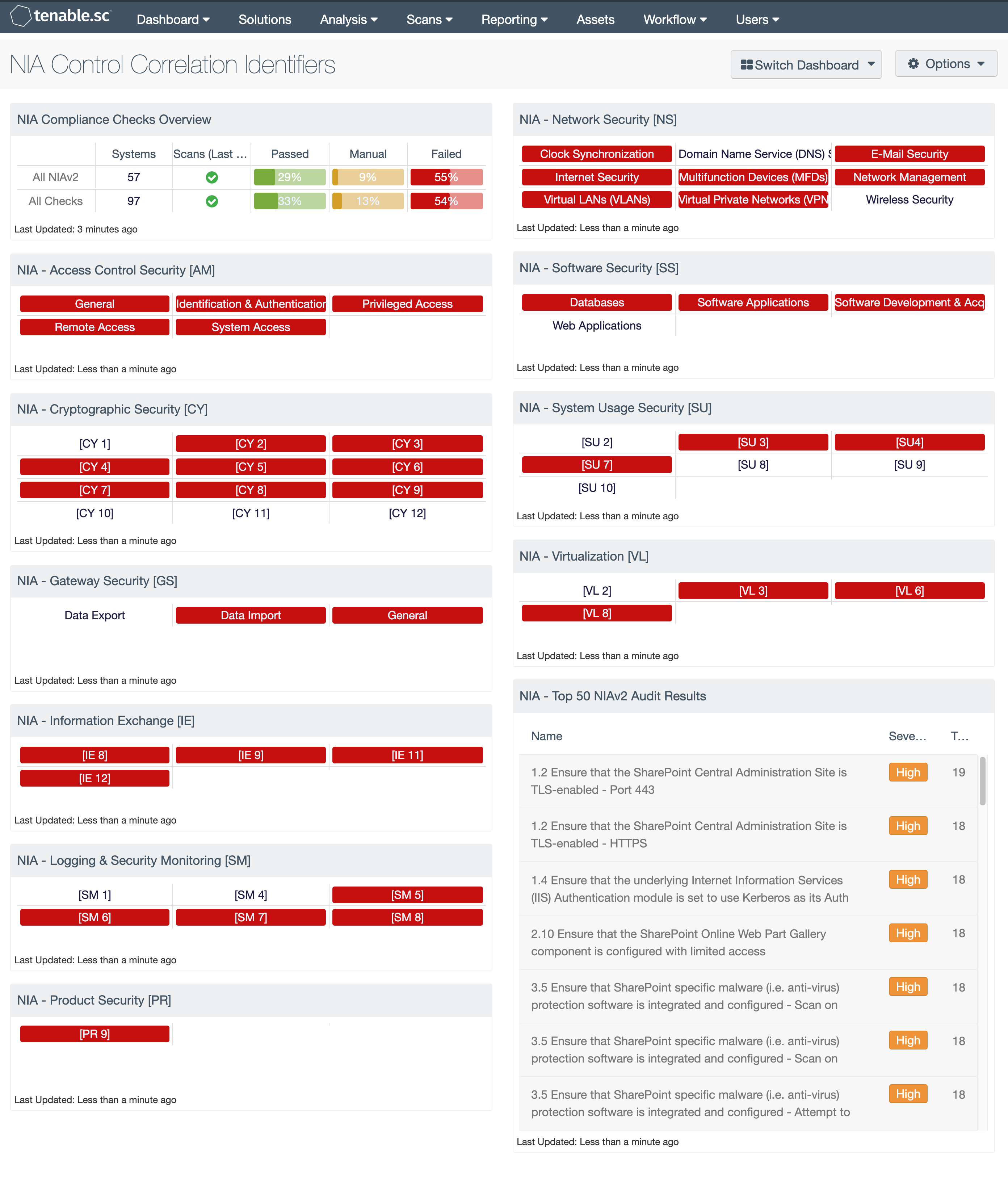
NIA Compliance Checks Overview: This component presents the results of compliance audits to verify secure system configurations. There are two rows, one for compliance checks specific to NIAv2 and one for all compliance checks. Each row includes the system count, whether scans were performed in the last 7 days, and the percentage of checks that passed, failed, or require manual verification. Passed checks are displayed in green, failed checks are in red, and checks that require manual verification are in orange. Clicking on a highlighted indicator will bring up the vulnerability analysis screen to display details on the compliance checks and allow further investigation. In the vulnerability analysis screen, setting the tool to IP Summary will display the systems on which the compliance checks are present. Setting the tool to Vulnerability Detail List will display the full details on each compliance check, possibly including further information such as the expected and actual policy values and the specific sections of the various standards to which the compliance check relates.
NIA - Access Control Security [AM]: This matrix provides indicators for failed audit checks which are controls of the NIA Access Control Security (AM) domain. The policy in this domain establish a series of controls used to ensure the confidentiality, integrity, and availability of information assets. The indicators in this matrix component turn red to show that the check was outside of the defined parameter. The component has indicators for the following controls in this domain: General (AM 1 to AM 11), Identification and Authentication (AM 12 to AM 27), System Access (AM 28 to AM 30), Privileged Access (AM 31 to AM 34), and Remote Access (AM 35 to AM 41).
NIA - Cryptographic Security [CY]: This matrix provides indicators for failed audit checks which are controls of the Cryptographic Security [CY] domain. The policy in this domain establish a baseline for the use of encryption technologies for keeping information assets confidential and/or integral. As a custodian of public and confidential information, Agencies must further protect private and sensitive data/information from all cyber threats and vulnerabilities whether external or internal. For this component, when the cell turns red, the indicator means the check was outside of the defined parameter. The component has indicators for the following controls in this domain: CY 1 through CY 12.
NIA - Gateway Security [GS]: This matrix provides indicators for failed audit checks which are members of the NIA Gateway Security [GS] policy. The policy in this domain provides a minimum security requirement for securing gateways used for inter-agencies communications as well as for external link communications. The indicators in this matrix component turn red to show that the check was outside of the defined parameter. The component has indicators for the following controls in this domain: General GS 1 to GS 10), Data Export (GS11, GS12, GS13, GS14), and Data Import (GS15, GS16, GS17).
NIA - Information Exchange [IE]: This matrix provides indicators for failed audit checks which are controls of the NIA Information Exchange [IE] domain. The policy in this domain primarily focus on the baseline security requirements when an agency is exchanging confidential information with other government agencies or third parties. When the cell turns red, the indicator means the check was outside of the defined parameter. The component has indicators for the following controls in this domain: IE 8, IE 9, IE 11, and IE 12.
NIA - Logging and Security Monitoring [SM]: This matrix provides indicators for failed audit checks which are controls of the NIA Logging and Security Monitoring [SM] domain. The policy for this domain primarily focus requirements for logging and monitoring to identify unauthorized data, application and resource access and to detect unauthorized changes or access privileges abuse. When the cell turns red, the indicator means the check was outside of the defined parameter. The component has indicators for the following controls in this domain: SM 1, SM 4, SM 5, SM 6, SM 7, and SM 8.
NIA - Product Security [PR]: This matrix provides indicators for failed audit checks which are controls of the NIA Product Security [PR] domain. The policy in this domain establishes the minimum security for selecting and acquiring information products through a proper selection and acquisition process. When the cell turns red, the indicator means the check was outside of the defined parameter. The component has indicators for the following controls in this domain: [PR 9].
NIA - Network Security [NS]: This matrix provides indicators for failed audit checks which are controls of the NIA Network Security [NS] domain. The policy in this domain provides guidance for the general use and connection of IT networks. When the cell turns red, the indicator means the check was outside of the defined parameter. The component has indicators for the following controls in this domain: Clock Synchronization, Domain Name Service (DNS) Servers, E-Mail Security, Internet Security, Multifunction Devices (MFDs), Network Management, Virtual LANs (VLANs), Virtual Private Networks (VPNs), Wireless Security.
NIA - Software Security [SS]: This matrix provides indicators for failed audit checks which are controls of the NIA Software Security [SS] domain. The policy in this domain defines the importance of including security in the process of software development and acquisition. This policy defines security as it applies to the various phases of the Software / System Development Life Cycle (SDLC). This policy also covers security controls for commercial applications deployed within an agency. When the cell turns red, the indicator means the check was outside of the defined parameter. The component has indicators for the following controls in this domain: Databases, Software Applications, Software Development and Acquisition, and Web Applications.
NIA - System Usage Security [SU]: This matrix provides indicators for failed audit checks which are controls of the NIA System Usage Security [SU] domain. The policy in this domain establishes the need for agencies to clearly define what behaviors and actions are permissible on their systems, and what is unacceptable. When the cell turns red, the indicator means the check was outside of the defined parameter. The component has indicators for the following controls in this domain: [SU 2], [SU 3], [SU 4], [SU 7], [SU 8], [SU 9], and [SU 10].
NIA - Virtualization [VL]: This matrix provides indicators for failed audit checks which are controls of the NIA Virtualization [VL] domain. The policy in this domain relates to securing the virtualized IT infrastructure at the agency. Agencies need to ensure that such virtualized environments are adequately secured. When the cell turns red, the indicator means the check was outside of the defined parameter. The component has indicators for the following controls in this domain: VL 2, VL 3, VL 6, and VL 8.
NIA - Top 50 NIAv2 Audit Results: This component provides a list of the top 50 audit results with a NIAv2 cross-reference present. The table is sorted based on severity and provides the plugin name, severity, and the number of hosts for which the NIA configuration checks have been detected.