by Cesar Navas
November 19, 2020
The National Information Assurance (NIA) Policy v2.0 is associated with the State of Qatar’s Ministry of Transport and Communications (MOTC). This policy was developed to help the organization in the State of Qatar enable a full-fledged information security management system within their agency. The organization needs to show compliance with the NIA Policy v2.0 through an annual audit by a certification body. This policy includes a series of security governances and technical controls, grouped into security domains that cover control areas that an agency needs to implement as baseline security to be compliant with the NIA Policy and in accordance with the NIA Manual. This dashboard will enable the executive team to gauge the compliance of the NIA Policy in relation within their organization.
Tenable.sc can identify compliance checks that relate to these technical controls. The date presented to the CISO provides an understanding of which security domains require attention or which are compliant. The combination of Vulnerability Priority Rating (VPR), Service Level Agreements (SLA), and compliance components allows the viewer to examine the state of NIA implementation and track risk mitigation efforts. The CISO uses this dashboard to brief the executive team and prepare for the NIA auditors.
The NIA Manual provides, baseline controls which an organization should implement at minimum, to protect their information system. The security controls are grouped into the following domains:
- Access Control Security [AM]
- Cryptographic Security [CY]
- Gateway Security [GS]
- Information Exchange [IE]
- Logging, Auditing & Security Monitoring [SM]
- Network Security [NS]
- Product Security [PR]
- Software Security [SS]
- System Usage Security [SU]
- Virtualization [VL]
According to section 2 of the NIA Policy v2.0 Overview chapter, Agencies conforming to the NIA manual may implement over and above the baseline. In case NIA controls intersect with other laws and regulations, such as Center for Internet Security (CIS) or the NIST Cybersecurity Framework, the organization must consider compliance to both or whichever is providing higher degree of security.
The dashboard is grouped with 3 areas of focus; NIA compliance, SLA progression, and VPR summary.
By tracking system hardening efforts over time, and current configuration stats, the CISO can understand how best practices are being implemented. The VPR components shows risk reduction tasks that will reduce the most prevalent risks seen in the wild. The SLA components allow the executive team the ability to monitor progress in the wider vulnerability management arena. This dashboard can serve as a quick glance summary of NIA compliance and the overall state of vulnerability within the organization. Using this dashboard, the CISO is provided with the required data that is needed to prove compliance.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment.
The dashboard requirements are:
- Tenable.sc 5.14.1
- Nessus 8.10.1
- Compliance data
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provide the ability to continuously Assess an organization’s adherence to best practice configuration baselines. Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective Information Security Management System program prescribed by the NIA standard.
Components
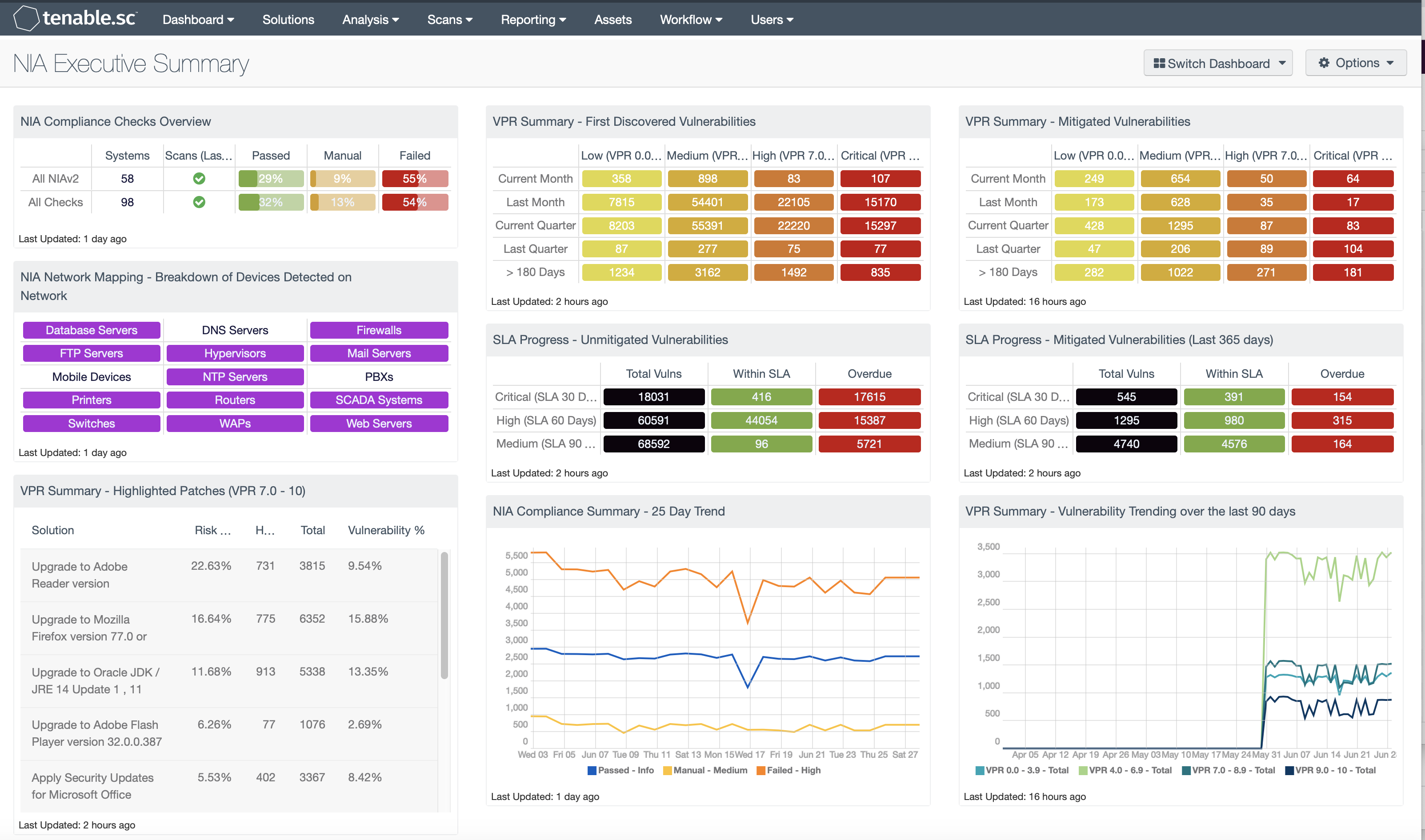
NIA Compliance Checks Overview: This component presents the results of compliance audits to verify secure system configurations. There are two rows, one for compliance checks specific to NIAv2 and one for all compliance checks. Each row includes the system count, whether scans were performed in the last 7 days, and the percentage of checks that passed, failed, or require manual verification. Passed checks are displayed in green, failed checks are in red, and checks that require manual verification are in orange.
NIA Network Mapping – Breakdown of Devices Detected on Network: This matrix presents a breakdown of detected network systems by type. A purple indicator denotes that systems of that type were detected; clicking on the indicator will bring up information on each of the detected systems, including IP address and MAC address. This information assists an organization in maintaining an accurate inventory and detecting any unauthorized systems.
VPR Summary – Highlighted Patches (VPR 7.0 – 10): The component uses the High and Critical VPR levels (VPR 7.0 - 10) combined with the remediation summary tool to provide a focused view of patches that should be considered at a higher priority than other patches. The tool provides a list of patches to apply, the amount of risk reduced (based on vulnerability weight score), hosts affected, and percentage of vulnerabilities.
VPR Summary – First Discovered Vulnerabilities: This component provides organizations with a view of vulnerabilities over a period of time. The columns are grouped using the VPR score levels, ranging from least risk to the greatest risk. Each row uses the Vulnerability First discovered filter to track when a risk first appeared on the network. The rows progress from the current month, last month, current quarter, last quarter, to vulnerabilities first discovered over 180 days ago. Most SLA’s allow for the vulnerability to exist on the network for 30 days, due to a standard 30-day patch cycle. Organizations can modify this matrix to support the SLA as defined by their risk management officer.
VPR Summary – Mitigated Vulnerabilities: This component provides organizations with a view of vulnerabilities that have been mitigated, showing progress towards risk management SLA’s. The columns are grouped using the VPR score levels, ranging from least risk to the greatest risk. Each row uses the Vulnerability Mitigated filter to track when a risk first appeared on the network. The rows progress from the current month, last month, current quarter, last quarter, to vulnerabilities first discovered over 180 days ago. Most SLA’s allow for the vulnerability to exist on the network for 30 days, due to a standard patch cycle. Organizations can modify this matrix to support the SLA as defined by their risk management officer.
SLA Progress – Unmitigated Vulnerabilities: The matrix provides a summary of vulnerabilities based on the CVSS score and the SLA of 30, 60, 90 days. Each of the three rows are based on the CVSS severity from Medium to Critical. The three columns illustrate the count of vulnerabilities across all systems. To provide more focus to an asset group, the component can be installed with focus option set accordingly. The black cells are the count of vulnerabilities, with green meaning newly discovered and are within the prescribed SLA, while the red count are vulnerabilities that have been detected on the network for more than the allotted mitigation time.
NIA Compliance Summary – 25 Day Trend: This component provides a 25-day trend analysis for all NIA compliance checks. The data points are calculated using the 'Days Since Observation' set to 'within the last day'. Thus, each data point only calculates the new compliance checks observed daily. The resulting graph more accurately depicts the change in compliance over the period of 25 days.
VPR Summary – Vulnerability Trending over the last 90 days: This component contains a trend analysis for each of the VPR levels: low (VPR 0-3.9), medium (VPR 4.0-6.9), high (VPR 7.0-8.9) and critical (VPR 9.0 - 10) over the past 90 days. Each line in the chart uses the Vulnerability Last Observed filter to allow the analysts to observe changes from day to day. As you move the mouse over the lines, you will see data points, with Vulnerability Last Observed filter the query between the data points will highlight the change from day-to-day. If the scanning strategy is to scan every 7 days, the graph will show spikes every seven days. However, if the organization is scanning daily, then a more accurate view of the trend data will be displayed, as the daily changes are shown.