by Stephanie Dunn
December 19, 2016
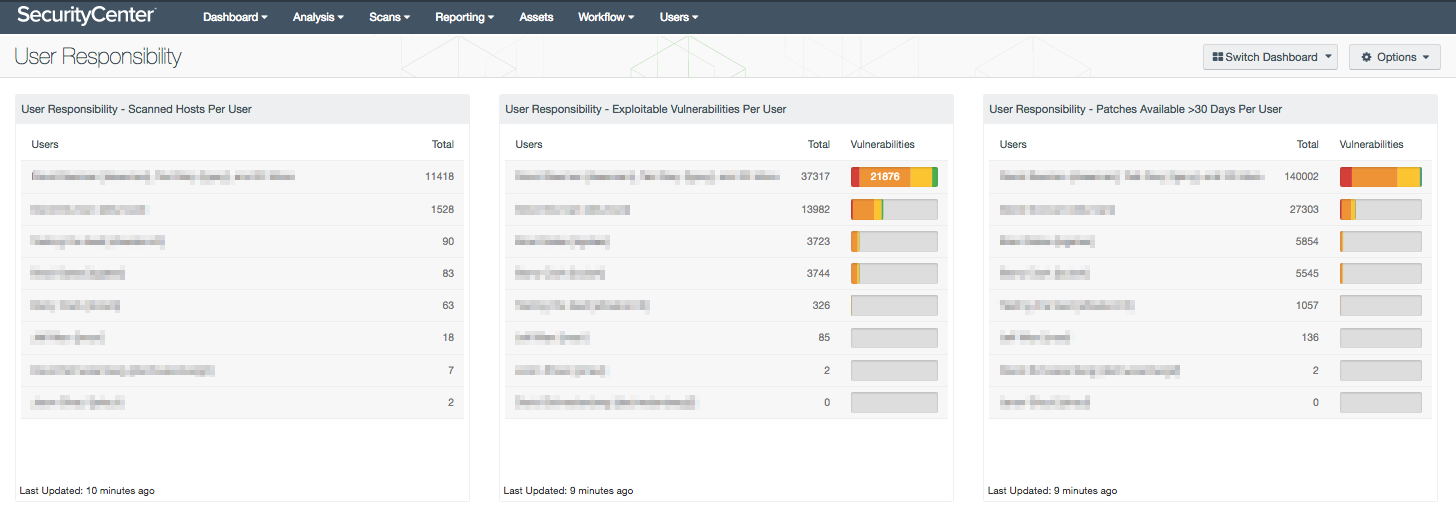
Assigning responsibility for patching systems can vary depending on the number of locations, industry type, and size of the organization. Organizations can have multiple locations throughout the world with individuals or teams responsible for patching specific corporate sites or systems on the network. Without having an effective patch management process in place, organizations can easily lose track of who is responsible for managing and patching systems. This dashboard can assist an organization in tracking patch management responsibilities, and provide a clear understanding on how often systems are being patched.
Tenable.sc Continuous View (CV) provides a variety of asset templates that can be customized for every type of organization. Analysts can create custom assets based on specific subnets, DNS names, operating systems, or a combination of collected data. Organizations can then assign users accounts to specific assets based on their job responsibilities. This data can also be used for auditing and inventory purposes to identify specific individuals responsible for managing specific devices, but not necessarily patching them. Knowing who is responsible for patching systems can help to reduce security risks that could impact critical systems and services within an organization.
This dashboard will provide a summary of hosts each user is responsible for, exploitable vulnerabilities per user, and count of patches available for more than 30 days per user. Using active scanning with Tenable Nessus, and passive listening using Tenable's Nessus Network Monitor (NNM), analysts will be able to track transient host changes. Both security teams and management will obtain valuable information on how often systems are being patched by patch management personnel. Organizations can use the information presented within this dashboard to address security gaps, ensure timely patching, and reduce overall risks. More information on the User Responsibility functionality in Tenable.sc can be found in the User Responsibility How-To Guide.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Monitoring. The dashboard requirements are:
- Tenable.sc 5.1.0
- Nessus 8.7.1
- NNM 5.10.1
Tenable.sc CV is the market-defining continuous network monitoring solution, and can assist in securing an organization’s internal network. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to determine vulnerabilities and compliance concerns. Agent scanning enables scanning and detection of vulnerabilities on transient and isolated devices. Passive listening provides real-time discovery of vulnerabilities on operating systems, browsers, desktop applications, wireless devices, and critical infrastructure. Tenable.sc CV provides an organization with the most comprehensive view of the network, and will be able to establish prioritized, actionable remediation plans based on true threat intelligence and user responsibility.
The following components are included within this dashboard:
- User Responsibility - Scanned Hosts Per User: This table displays the number of scanned hosts for which each user (or group of users) is responsible. Only those hosts scanned by Nessus are counted. To obtain information on the specific systems for which a User is responsible, click on the Browse Component Data button, click on the desired User, and change the tool from Vulnerability Summary to IP Summary.
- User Responsibility - Exploitable Vulnerabilities Per User: This table displays the count of exploitable vulnerabilities on all systems for which each user (or group of users) is responsible. Both actively and passively discovered exploitable vulnerabilities are included. A bar graph of the vulnerabilities by severity is also displayed. The responsible user should take steps to remediate these vulnerabilities. To obtain detailed vulnerability information on the systems for which a User is responsible, click on the Browse Component Data button and click on the desired User. If desired, change the tool to Detailed Vulnerability List. To obtain remediations, change the tool to Remediation Summary.
- User Responsibility - Patches Available >30 Days Per User: This table displays the count of patches that have been available for more than 30 days for vulnerabilities on all systems for which each user (or group of users) is responsible. Both actively and passively discovered vulnerabilities are included. A bar graph of the vulnerabilities by severity is also displayed. The responsible user should take steps to apply these patches to remediate the vulnerabilities. To obtain detailed vulnerability information on the systems for which a User is responsible, click on the Browse Component Data button and click on the desired User. If desired, change the tool to Detailed Vulnerability List. To obtain remediations, change the tool to Remediation Summary.