Assess Log4Shell Like an Attacker With Tenable’s Dynamic Detections

Defenders need to pull out all the stops when it comes to Log4Shell. Tenable provides dynamic remote Log4Shell vulnerability detections to incorporate the attacker’s perspective of your organization.
The Log4Shell vulnerability in Apache Log4j presents significant challenges for security teams. Tenable is now providing dynamic remote checks, local plugins and tactical scan templates to make it easy for security professionals to detect this internet-breaking vulnerability.
Not only does Log4Shell introduce new open-source and software supply-chain issues, but detecting Log4Shell requires the industry to think differently about how to discover this critical vulnerability. There are a number of techniques that vulnerability management providers use to assess targets for exposures. One common approach is using local checks to identify current software versions and enumerate vulnerabilities contained in outdated software.
However, with distributed software systems like Java and its many open-source libraries, it’s difficult to find software libraries like Log4j embedded in enterprise applications. The result is that local checks that are simply querying for installed software often have many false negative results, leading to a false-sense of security in instances like Log4Shell. Security teams are simply not aware of all the instances where Log4j is used in their environment. Local checks must be used in conjunction with dynamic remote checks to cover a larger attack surface area.
Enter: Dynamic Remote Checks
This is where a new approach to remote checks comes into play. Dynamic remote checks send pseudo-exploit code to a target with the aim of discovering vulnerabilities throughout the entire system. This is the same approach an attacker would use to exploit the vulnerability but better: dynamic remote checks are completely safe to run. This method provides direct evidence that a system or application is vulnerable and has no negative impact on your security posture, systems or service levels..
In addition to the accuracy advantage, these checks can be remotely operated: they don’t require agents or authenticated scans to identify the vulnerability that local checks rely on for deep insight and accuracy. Remote scans are preferred by security teams responding urgently to a headline security event and don’t have time to install software or search for credentials.
Using Dynamic Remote Checks for Log4Shell
Since December 10, Tenable Research has released a number of dynamic remote checks across multiple products to help detect Log4Shell. The way we have built these plugins follow these steps:
- Tenable scanners send out a request to a scan target using a benign payload containing a crafted JNDI script.
- The target, if vulnerable to Log4Shell, will act on the payload.
- Tenable tracks the target’s action on the payload using a couple of techniques tailored to work in different deployment environments.
Here’s the secret sauce: how we perform step three varies depending on whether customers have deployed on-premises scanners versus cloud scanners. For on-premises scanners we simply use the Lightweight Directory Access Protocol (LDAP) connection for the callback to the scanner. If the callback happens, the target is confirmed to be vulnerable. See figure 1 below for how this works in Plugin 155998.
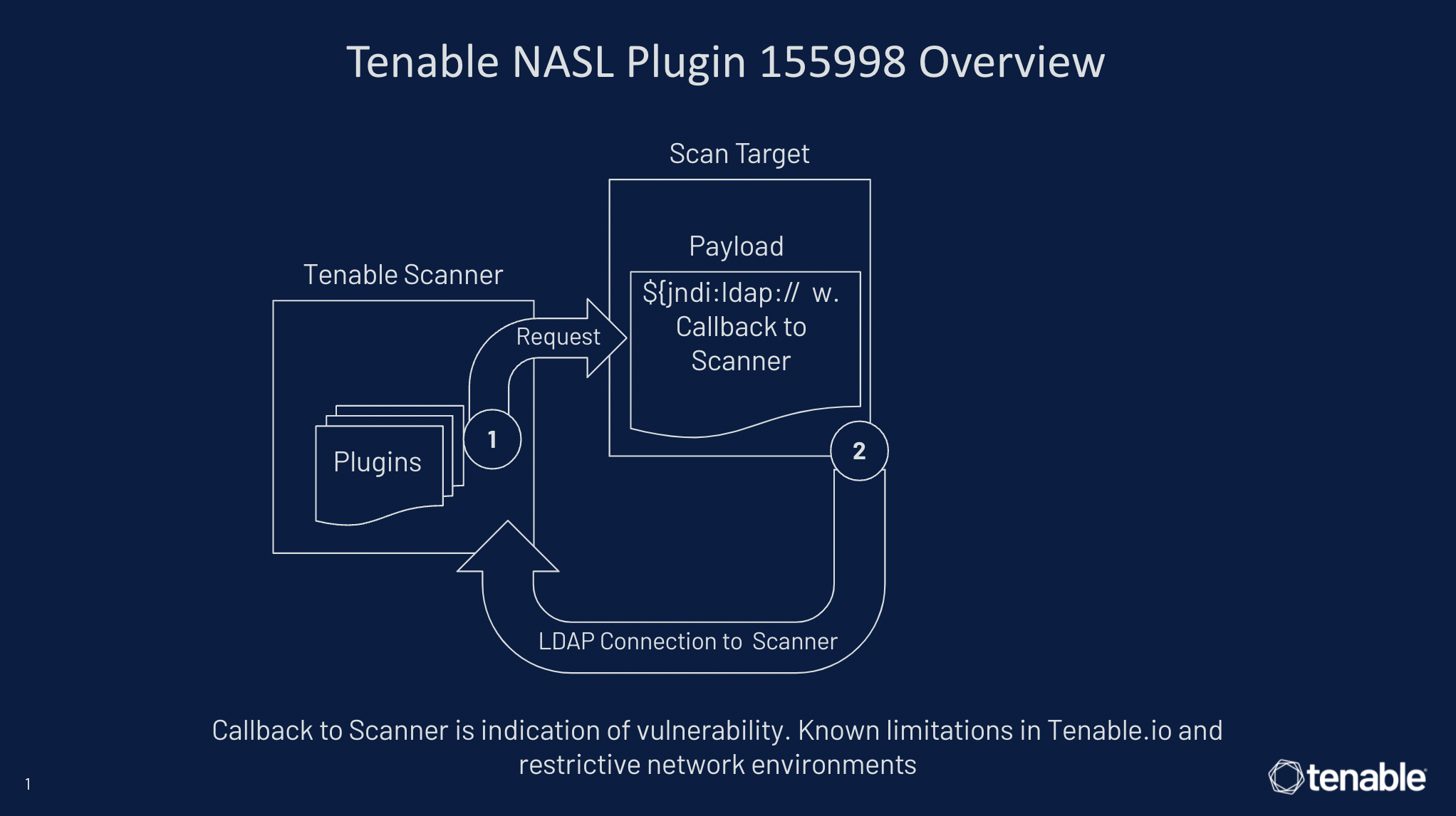
Figure 1
However, for cloud scanners we had to adjust tactics since they are outside of the firewall and external to the target. To address this issue, Tenable created a separate, secure, hosted environment in order to track the payload injection (and token) via DNS using default port 53. The scanner then performs a lookup against the Tenable controlled server to find the unique token that was sent in the initial request. If the token is there, the target is confirmed to be vulnerable. See figure two below for how this works in Plugin 156014. We have also expanded upon this approach in additional plugins to assess any open port and include SIP, SMTP, POP3, FTP, Telnet, IMAP and SSH.
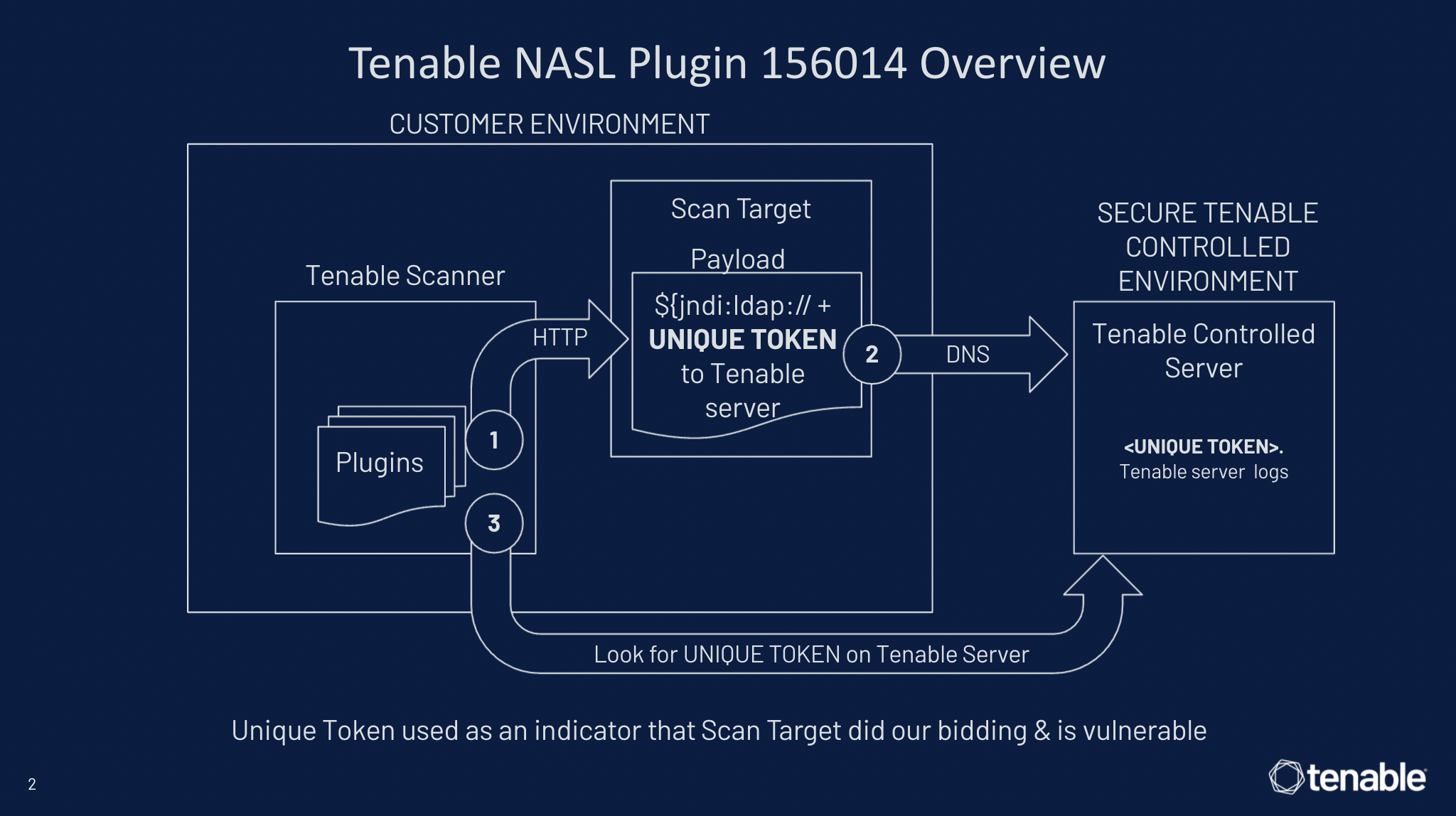
Figure 2
To discover web apps vulnerable to Log4Shell, we used a similar approach as Plugin 156014 to support cloud scanners in Tenable.io Web App Scanning (WAS). The key difference is that this dynamic check injects a payload into numerous portions of the web application, including various inputs, HTTP headers, POST/GET values, XML, JSON and cookies. Just as we used a Tenable controlled server to find unique tokens of vulnerable targets, we do the same for vulnerable web apps in exactly the same way. See figure 3 below for how this works in Plugin 113075.
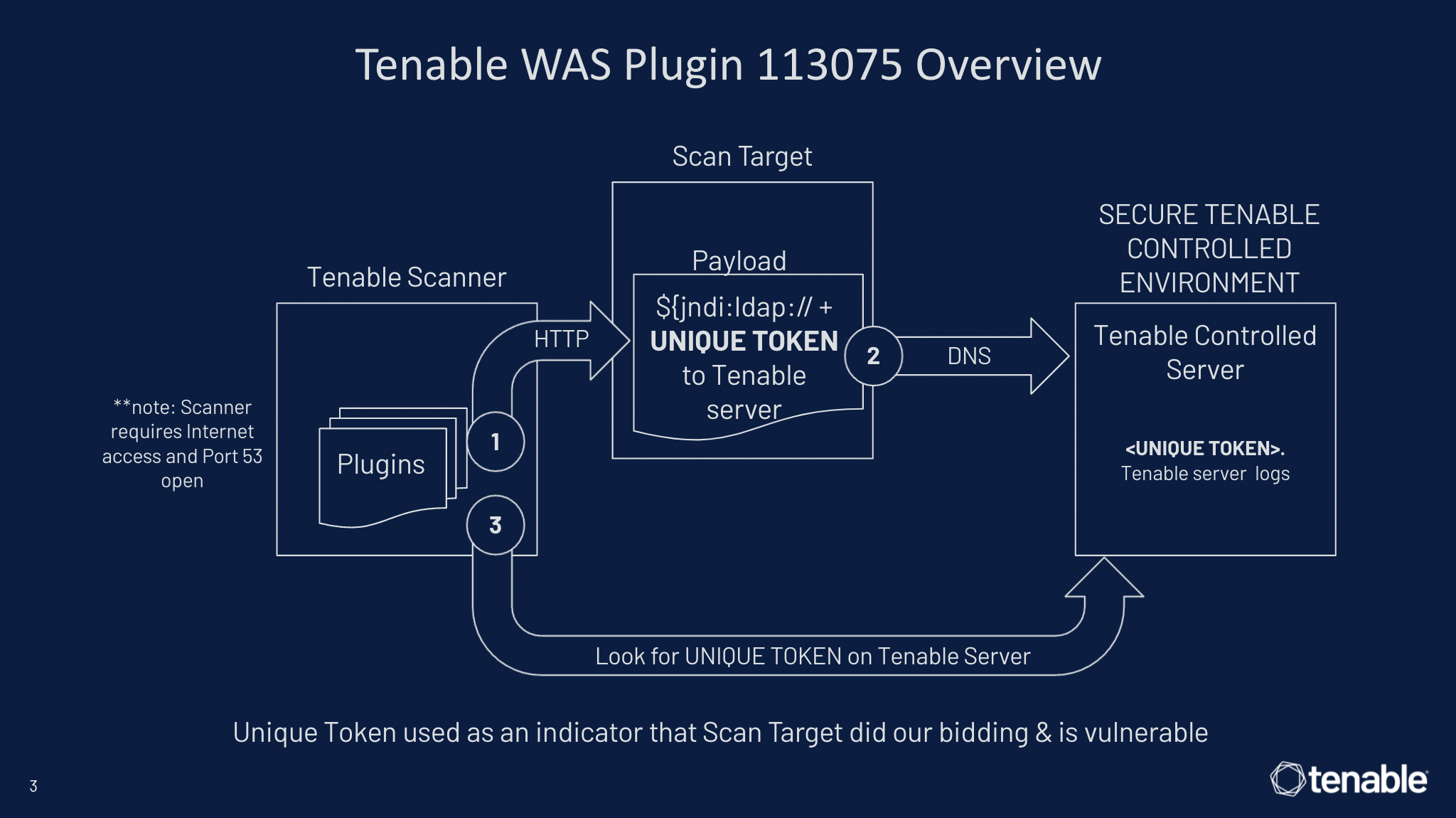
Figure 3
Best of Both Worlds
While dynamic remote checks are one of the most effective ways to minimize false negatives in the early days of Log4Shell, it is only part of the solution. You still need a combination of checks to gain full visibility into your Log4Shell exposures, especially as security advisories are issued by vendors impacted by vulnerable Log4j libraries. As always, using credentials to enable authenticated scans is essential for many static checks in order to gain “inside-out” visibility of the asset.
Tenable has released a number of local checks supporting Log4Shell that cover both “generic” version detections that check RPM packages and search file system paths for vulnerable Log4j matches on the local system and “specific” version detections that support product specific vendor advisories that require security updates.
This link provides the latest list of Tenable plugins available to help you identify Log4Shell and related vulnerabilities in your organization. In addition, this Tenable Community post provides additional supporting information about the plugins Tenable has released and how they work in more detail.
Take Action Today with Tactical Scans
As the list of Log4j-related vulnerabilities are growing and as new Tenable plugins are quickly being developed, it can be overwhelming to keep track of all of the changes while you’re putting out Log4Shell fires internally. Thankfully, you don’t have to. Tenable has created several scan templates to make it easy to configure and run assessments looking for Log4Shell.
For Nessus Professional, Tenable.sc and Tenable.io customers, we recommend using the Log4Shell Vulnerability Ecosystem scan, which will dynamically update automatically to include the latest vulnerability plugins as 3rd-party vendors patch their software. For Tenable.io Web App Scanning customers, please also use the preconfigured Log4Shell web app scan template. We recommend frequent rescanning at regular intervals to keep up-to-date and using credentials for local static checks.
We’re Here to Help!
To help you better defend against Log4Shell, we will be holding a series of live, how-to sessions in early January. These sessions will provide live product demos, recommended best practices and extended Q&A. We hope to see you there!
You can register here:
- How-To Scan for Log4Shell with Tenable.sc
- How-To Scan for Log4Shell with Tenable.io
- How-To Scan for Log4Shell with Nessus Pro
Finally, please check out the following product video tutorials on discovering Log4Shell to help you get the most value out of your investment with Tenable.
- Tenable.sc: Discovering Log4Shell Vulnerabilities
- Tenable.io: Discovering Log4Shell Vulnerabilities
- Tenable.io Web App Scanning: Discovering Log4Shell Vulnerabilities
- Nessus Professional: Discovering Log4Shell Vulnerabilities
Learn more
- Read the SRT alert: CVE-2021-44228: Proof-of-Concept for Critical Apache Log4j Remote Code Execution Vulnerability Available (Log4Shell)
- Read the SRT blog: CVE-2021-44228, CVE-2021-45046, CVE-2021-4104: Frequently Asked Questions About Log4Shell and Associated Vulnerabilities
- Read the CISO perspective: Apache Log4j Flaw Puts Third-Party Software in the Spotlight
- Read the CTO view: Apache Log4j Flaw: A Fukushima Moment for the Cybersecurity Industry
- Vulnerability Scanning

