Cloud Security: Improve Cyber Hygiene with Resource Tagging

Adopting consistent tagging practices can help to quickly identity resources, ensure change control efforts, and reduce security risks within your cloud environments.
Many organizations use the cloud to quickly deliver and scale applications across multiple cloud platforms. While engineering teams often work in parallel to build, test and deploy code across production and development environments, security teams are also working to continuously monitor and assess their cloud security posture.
As cloud footprints continue to scale, containing cloud costs and ensuring resource asset management have become top priorities. Without an effective plan to manage these changes, organizations can easily lose visibility on resources within their cloud environments. Over time, the number of unused resources will continue to increase, as will the number of resources with excessive permissions and other misconfigurations. Implementing a global tagging strategy provides an effective way to manage resources, control costs and prevent unnecessary risks. While tagging can be done manually, we see clear benefits in using Infrastructure as Code (IaC) to tag your resources.
We understand that IaC doesn't lend itself to every application or configuration; in some cases resources and tags need to be manually created. Some teams may not be using IaC at all, and have to manually deploy and tag resources. For these reasons, we also provide guidance on options available from cloud service providers that can help jumpstart your tagging strategy regardless of which method you choose.
Why Tagging?
According to Amazon Web Services (AWS), tagging provides an effective way to "manage, identify, organize, search for, and filter resources." While tagging can be used for cost optimization purposes, it can also be used to promote accountability within your organization. When security issues or incidents arise, adding consistent tagging practices enables your security practitioners to easily identify the team that owns any given cloud resource in order to quickly address issues and mitigate risk.
Getting Started: Establish Requirements
Tagging all of your cloud resources is considered best practice. But where do you begin? Business requirements can dictate whether to take a phased approach to your tagging strategy and help you identify priorities. We recommend identifying your critical services (i.e.: Identity and Access Management [IAM], Compute, etc.) first and applying tags to those resources. From there, you can work with your stakeholders to implement tagging on other services within your cloud environments.
One of the first items that should be established in your global tagging policy is determining a set of required tags. Depending on business requirements, using a unique and consistent set of tags is ideal. Reviewing whether your required tags are in use by teams internally will help to prevent overlap and conflicts. Other factors to consider are whether application ownership or team names change within your organization. If so, then using tags such as "owner" or "team" may not be useful. Lastly, you should determine how your "required" tags will be applied and enforced.
Tagging using Infrastructure as Code
If your organization is using IaC in some form, your first step should be to work with your stakeholders and understand if, where and how these tools are being used across your cloud environments. Whether you have one cloud account or hundreds of accounts, tags can be easily added into your IaC with just a few lines of code, as shown in the examples below.
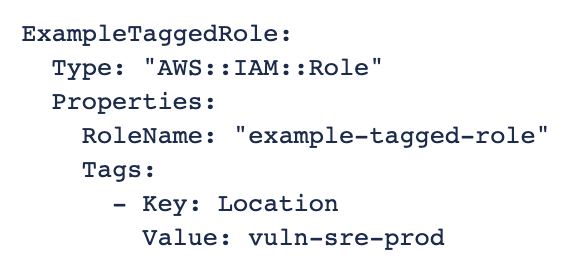
Image: Adding tags using CloudFormation

Image: Adding tags using Terraform
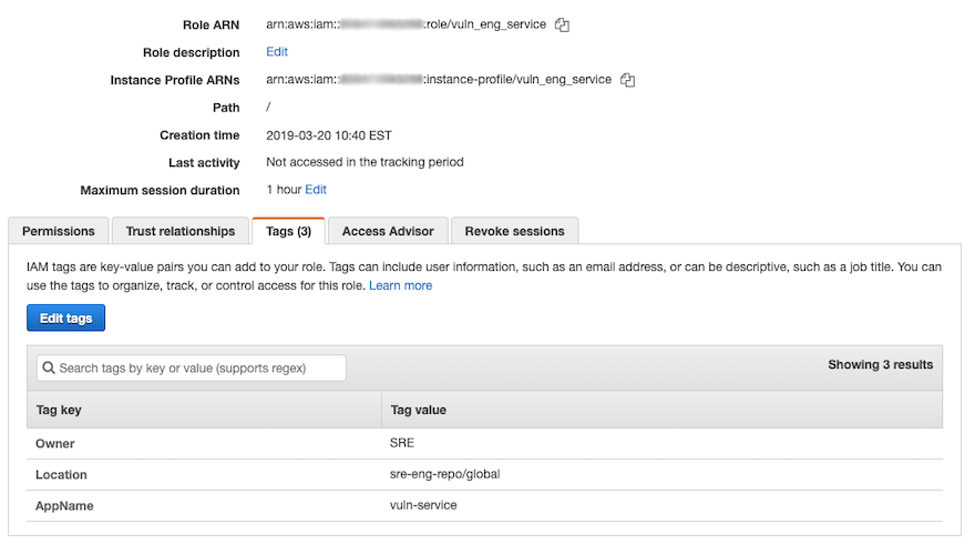
In this example, the Location tag value includes the name of the code repository from which the IAM role is deployed. Using Creation Time and Last Activity details, this IAM role was deployed from code and has not been accessed in the last 400 days. Security teams can work with code owners to remove the unused role from the account.
Cloud Vendor Support for Tagging
For teams that have yet to embrace tagging using IaC, or simply need a solution to quickly deploy tags, AWS, Microsoft Azure and Google Cloud Platform (GCP) have several options that can help.
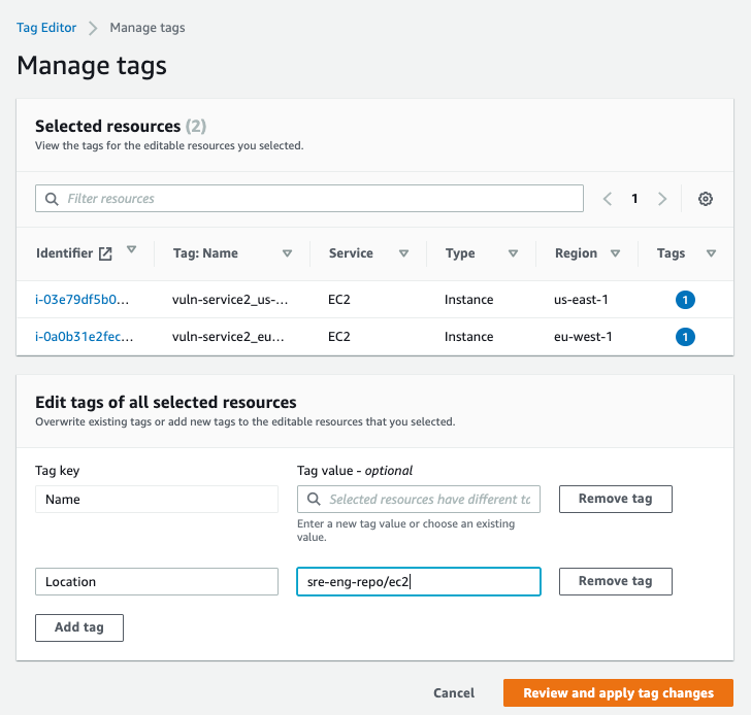
- AWS - Tag Editor provides a centralized solution to view and add tags on your resources across any region within an AWS account. In the example below, Location tags are being applied to two Elastic Compute Cloud (EC2) instances in separate regions.
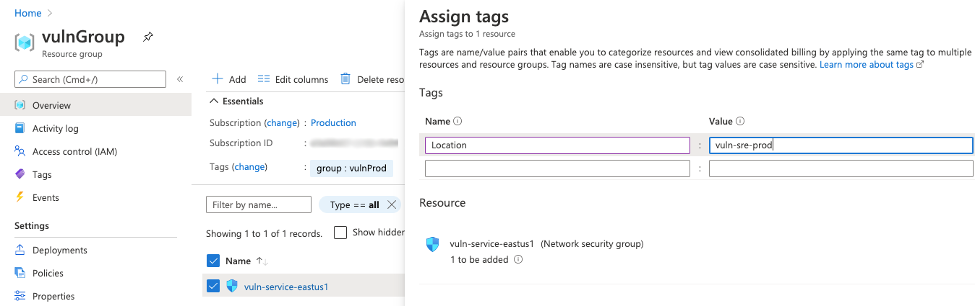
- Azure - Resource Groups provide a great way to apply tags to resources, resource groups and subscriptions. Once you've created and associated resources with your group, you can then assign tags to any of your target resources.
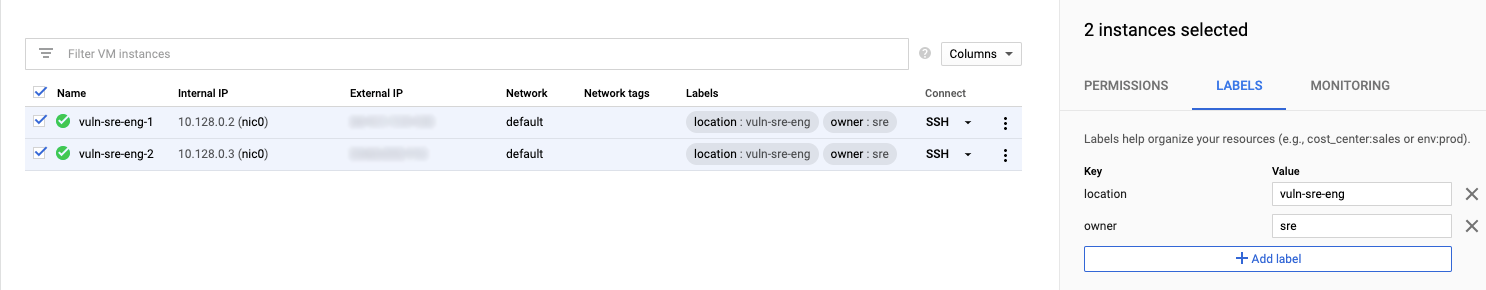
- GCP - Labels are key/value pairs used to organize existing resources. By adding Labels to your resources, you can easily filter on production versus development resources, teams and services.
All three cloud platforms provide additional services and API support for advanced use cases that will help to audit and enforce tagging practices.
Understand the Benefits
Ensuring cyber hygiene practices though tagging should be a critical part of your cloud security program. Once consistent tagging practices are in place, less time is spent searching for resources and finding owners to address security risks. Below are just some of the benefits of an effective global tagging strategy:
- Improve incident response time
- Remediate security risks
- Prevent privilege escalation
- Enforce change management policies
- Identify resource owners
- Support auditing and compliance efforts
- Remove unused resources
- Reduce cloud costs
Implementing a global tagging strategy will take time and buy-in from teams across the organization. Once these practices are in place, security teams will have improved visibility into cloud assets, enabling them to effectively reduce cyber risk and understand the organization's exposure across any cloud environment.
Learn More:
- Download the solution brief: Frictionless Assessment of AWS Assets
- Amazon Web Services (AWS) Whitepaper: Tagging Best Practices
- Cloud
- Vulnerability Management
- Vulnerability Scanning

