Cybersecurity Snapshot: CISA Analyzes Malware Used in SharePoint Attacks, as U.K. Boosts Cyber Assessment Framework

Check out what CISA found after it dissected malware from the latest SharePoint hacks. Plus, the U.K.’s cyber agency is overhauling its cyber framework to keep pace as threats escalate. In addition, CISA is sounding the alarm on a high-severity vulnerability impacting hybrid Exchange environments. And get the latest on the sophistication of cloud attacks and on a CISA report about a critical infrastructure org’s cyber flaws.
Editor's note: This blog was updated on Friday, August 8 with an item about CISA's Emergency Directive 25-02 regarding CVE-2025-53786, an elevation-of-privilege vulnerability impacting hybrid Microsoft Exchange environments.
Here are six things you need to know for the week ending August 8.
1 - CISA unpacks malware linked to exploited SharePoint bugs
CISA has published an analysis of six malware files associated with SharePoint vulnerabilities that have been actively exploited in recent weeks.
Hackers are using the files – including web shells and a key stealer – to swipe cryptographic keys and exfiltrate data by running malicious code, CISA said in a statement this week.
“CISA encourages organizations to use the indicators of compromise (IOCs) and detection signatures in this Malware Analysis Report to identify malware samples,” reads the report titled “MAR-251132.c1.v1 Exploitation of SharePoint Vulnerabilities.”

The vulnerabilities – CVE-2025-49706, CVE-2025-49704, CVE-2025-53770 and CVE-2025-53771 – impact on-premises versions of SharePoint Server: SharePoint Server Subscription Edition, SharePoint Server 2019 and SharePoint 2016. SharePoint Online in Microsoft 365 isn’t affected.
The first attacks were reported on July 19, as hackers linked CVE-2025-49706 and CVE-2025-49704 in an exploit chain dubbed “ToolShell.” The exploitation of CVE-2025-53770, a zero-day bug Microsoft described as a variant of CVE-2025-49706, soon followed.
Although Microsoft has not confirmed it, it’s likely that CVE-2025-53771 has also been exploited, since it can be chained with CVE-2025-53770, according to CISA.
To get the details on these SharePoint vulnerabilities, check out the Tenable Research Special Operations team’s blog “CVE-2025-53770: Frequently Asked Questions About Zero-Day SharePoint Vulnerability Exploitation.”
Attackers exploiting these SharePoint vulnerabilities include, according to Microsoft, Chinese nation-state groups Linen Typhoon and Violet Typhoon, as well as China-based ransomware actor Storm-2603..
To get more information about these SharePoint vulnerabilities, check out:
- “Disrupting active exploitation of on-premises SharePoint vulnerabilities” (Microsoft)
- “Customer guidance for SharePoint vulnerability CVE-2025-53770” (Microsoft)
- “CVE-2025-53770: Frequently Asked Questions About Zero-Day SharePoint Vulnerability Exploitation” (Tenable)
- “SharePoint 0-day uncovered (CVE-2025-53770)” (Eye Security)
- ““Microsoft Releases Guidance on Exploitation of SharePoint Vulnerabilities” (CISA)
2 - NCSC updates cyber framework to tackle advanced threats
In response to the growing sophistication of attacks impacting British critical service providers, the U.K.’s cyber agency has revamped its core cybersecurity framework.
Version 4.0 of the National Cyber Security Centre’s (NCSC) Cyber Assessment Framework, published this week, features new and updated information in four key areas:
- Attacker methods and motivations
- Secure development of software used in essential services
- Cyber threat detection via security monitoring and threat hunting
- AI-related cyber risks

(Image generated by Tenable using Google Gemini)
For example, a new section about cyber risk management explains how policies, processes and procedures can help organizations better understand, assess and manage cybersecurity risks. Another new section focuses on supply chain risk in areas like software development and cloud services.
“Keeping pace with the evolution of attack methods is essential to close the widening gap between the escalated cyber threats to critical services, and our collective ability to defend against them,” the NCSC said in a statement.
“These two themes have driven our updates to the CAF to ensure the framework remains relevant, and that organisations' defences are up to date,” it added.
The Cyber Assessment Framework is designed to help organizations that provide critical services enhance their cyber resilience to prevent operational disruptions in areas such as energy, healthcare, government and transportation.
For more information about the benefits of adopting cybersecurity frameworks:
- “A Complete Guide to the NIST Risk Management Framework” (EC-Council)
- “A Comparison of Leading Security Frameworks: NIST, ISO 27001, and Zero Trust” (Quick and Dirty Tips)
- “Top 12 IT security frameworks and standards explained” (TechTarget)
- “Essential Cybersecurity Frameworks and Standards for Start-ups and Fast-Growing Tech Companies” (CTO Academy)
- “SOC2 vs NIST VS ISO: Understanding the Differences Between Cybersecurity Frameworks” (Security Scientist)
5 Cybersecurity Frameworks Every GRC Professional Needs To Know (GRC for Mere Mortals)
3 - CISA tells fed agencies to patch high severity Exchange bug ASAP
U.S. federal civilian agencies with cloud and on-premises versions of Microsoft Exchange must fix an elevation-of-privilege vulnerability that, if exploited, would open the door to potentially massive breaches.
So said CISA this week via Emergency Directive 25-02, which instructs agencies with hybrid Exchange environments to mitigate the vulnerability by no later than 9 am ET on Monday, August 11.
This post-authentication vulnerability – CVE-2025-53786 – could allow an attacker to move laterally from on-premises Exchange to Exchange Online in Microsoft 365, according to CISA. There have been no observed exploits of this vulnerability at this time.
“An attacker with administrator privileges to an on-premises Exchange Server can escalate their privileges within a connected cloud environment,” reads Tenable Research Special Operations (RSO) team’s blog “CVE-2025-53786: Frequently Asked Questions About Microsoft Exchange Server Hybrid Deployment Elevation of Privilege Vulnerability.”
“This flaw exists due to Exchange Server and Exchange Online sharing ‘the same service principal in hybrid configurations,’” the Tenable blog adds.

While CISA’s directive applies only to Federal Civilian Executive Branch (FCEB) agencies, the agency is urging all organizations impacted by this Exchange vulnerability to address it immediately.
“The risks associated with this Microsoft Exchange vulnerability extend to every organization and sector using this environment. While federal agencies are mandated, we strongly urge all organizations to adopt the actions in this Emergency Directive,” CISA Acting Director Madhu Gottumukkala said in a statement.
Microsoft first disclosed CVE-2025-53786 on August 6, after “further investigation of a non-security Hot Fix released on April 18 alongside an announcement on Exchange Server Security Changes for Hybrid Deployments,” according to the Tenable RSO blog.
In a LinkedIn post, Tenable Chief Security Officer Robert Huber said Microsoft should have stressed the urgency of this issue when it issued the hot fix months ago.
“This left a dangerous three-month window where organizations were exposed to a threat that strikes at the heart of the modern enterprise: Active Directory and the cloud,” Huber wrote in his post titled “The Exchange Vulnerability Is a Bigger Deal Than You Think.”
“This vulnerability provides a direct path for an attacker to escalate privileges from an on-premise server to the cloud, effectively handing them the keys to your kingdom,” Huber added.
To get more details, check out:
- CVE-2025-53786 (Tenable)
- “CVE-2025-53786: Frequently Asked Questions About Microsoft Exchange Server Hybrid Deployment Elevation of Privilege Vulnerability” (Tenable)
- “Microsoft Exchange Server Hybrid Deployment Elevation of Privilege Vulnerability” (Microsoft MSRC)
- “Exchange Server Security Changes for Hybrid Deployments” (Microsoft blog)
- “Released: April 2025 Exchange Server Hotfix Updates” (Microsoft blog)
- “Microsoft Releases Guidance on High-Severity Vulnerability (CVE-2025-53786) in Hybrid Exchange Deployments” (CISA)
- “ED 25-02: Mitigate Microsoft Exchange Vulnerability” (CISA)
4 - Google: Cloud attacks are getting smarter and nastier
Hackers are sharpening their attacks on cloud environments with new advanced tactics – and inflicting disruptive damage.
That’s a key takeaway from Google’s “Cloud Threat Horizons Report H2 2025,” published this week.
“Cloud environments face an increasingly sophisticated threat landscape as actors advance their methods for data exfiltration, identity compromise and supply chain attacks, while simultaneously improving evasion and persistence techniques,” reads the report.
Cloud hackers’ new playbook includes:
- Wrecking your disaster recovery: Hitting backup systems first to cripple your safety net
- Bypassing multi-factor authentication: Stealing credentials and session cookies with slick social engineering to walk right past your defenses
- Hiding in plain sight: Planting malicious files – usually PDFs – inside legitimate cloud storage services
Still, their favorite entry points remain the good old methods of credential compromise and misconfiguration exploitation. Google’s advice? Double down on foundational cybersecurity, including solid identity and access management, and proactive vulnerability management.
H1 2025 Distribution of Initial Access Vectors Exploited by Threat Actors
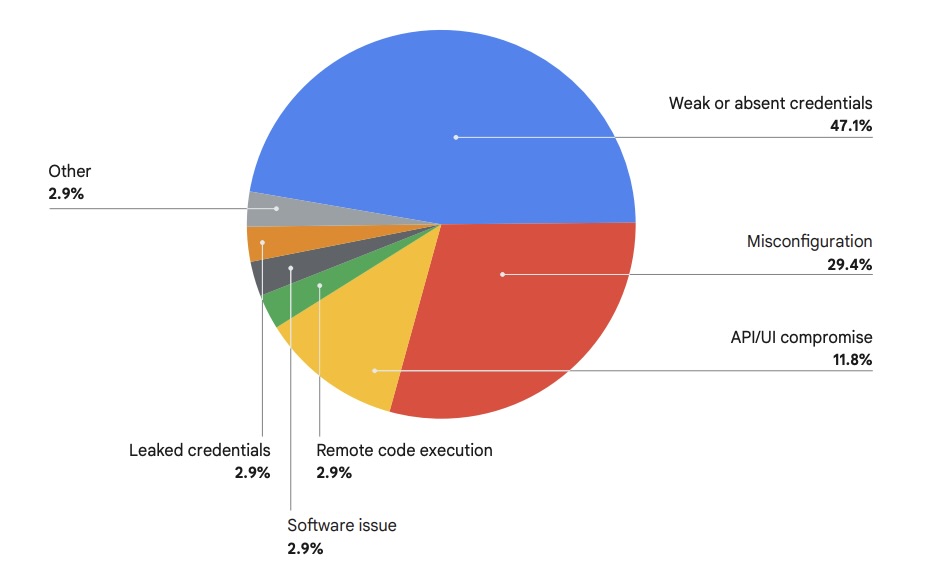
(Source: Google’s “Cloud Threat Horizons Report H2 2025,” August 2025)
Specifically, the report recommends embracing a defense-in-depth strategy centered on:
- identity security
- recovery mechanisms
- vigilance against sophisticated social engineering and deception tactics
- supply chain integrity
For more information about cloud security, check out these Tenable resources:
- “Identity is the New Perimeter: Why Your IdP Isn’t Enough” (blog)
- “Tenable Cloud Security Risk Report 2025” (report)
- “Why Your Cloud Data May Not Be Secure After All: Insights from Tenable Research” (on-demand webinar)
- “Tackling Shadow AI in Cloud Workloads” (blog)
- “The Future of Cloud Access Management: How Tenable Cloud Security Redefines Just-in-Time Access” (blog)
5 - Report finds alarming cyber gaps in critical infrastructure org
Plaintext passwords. Shared admin accounts. Unrestricted remote access.
These aren’t rookie mistakes. They’re real-world cybersecurity missteps found by CISA and the U.S. Coast Guard (USCG) during a recent threat hunt at an unnamed critical infrastructure organization.
While no active breach was discovered, the gaps put the organization at an elevated risk. The audit also revealed poor network segmentation between IT and operational technology (OT) environments, as well as insufficient logging.
“Critical infrastructure organizations are advised to review and implement the mitigations listed in this advisory to prevent potential compromises and better protect our national infrastructure,” reads the document, published this week.

(Image generated by Tenable using Google Gemini)
Mitigation recommendations include:
- Never store passwords or credentials in plain text. Instead, use tools such as encrypted password vaults and managed service accounts.
- Protect credentials by encrypting them at rest and in transit, and by adopting strong access controls. Conduct regular audits of scripts and tools that access credentials.
- Don’t share local admin account credentials. Rather, create unique, complex passwords for each account.
- Secure access to admin accounts and to remote access services with multi-factor authentication.
- Conduct granular and comprehensive logging across all systems, and ensure captured logs include authentication attempts and command-line executions.
The critical infrastructure organization asked CISA and USCG to conduct the threat hunt, and it participated in the drafting of the report.
To get more details, check out the full advisory “CISA and USCG Identify Areas for Cyber Hygiene Improvement After Conducting Proactive Threat Hunt at US Critical Infrastructure Organization.”
For more information about protecting critical infrastructure against cyber attacks:
- “Critical Infrastructure Security and Resilience” (CISA)
- “How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform” (Tenable)
- “Identity Security Is the Missing Link To Combatting Advanced OT Threats” (Tenable)
- “Cybersecurity of Critical Sectors” (EU Agency for Cybersecurity)
- “Critical Infrastructure Protection” (MITRE)
6 - CISA releases Thorium to boost malware analysis
Tired of juggling a dozen siloed malware analysis tools?
If so, you’re not alone, which is why CISA and Sandia National Laboratories have developed a new platform designed to unify and automate your malware analysis workflow.
Called Thorium and announced this week, the free platform is designed to integrate and orchestrate different malware analysis tools. Thorium also allows users to modify their toolsets.
“By publicly sharing this platform, we empower the broader cybersecurity community to orchestrate the use of advanced tools for malware and forensic analysis,” CISA Associate Director for Threat Hunting Jermaine Roebuck said in a statement.
(Credit: CISA)
Thorium is built for high performance. It can ingest 10 million files per hour and schedule 1,700 jobs per second, and it integrates with commercial, custom and open-source tools.
It's designed to give cyber defenders the speed and scale needed to combat modern threats.
“The goal of Thorium is to enable cyber defenders to bring automation to their existing analysis workflows through simple tool integration and intuitive event-driven triggers,” reads the Thorium fact sheet.
Key Thorium features include:
- the ability to integrate tools using Docker images
- filter results with tags and full-text searches
- manage access with group-based permissions
- scale operations with Kubernetes and ScyllaDB
To get more details, you can visit the Thorium GitHub page.
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- Malware
- OT Security
- Threat hunting


