Cybersecurity Snapshot: AI Security Tools Embraced by Cyber Teams, Survey Finds, as Vulnerability Research Gets a Boost from UK Cyber Agency

Check out why AI security tools are turning into “must have” assets for cyber teams. Plus, get the details on the NCSC’s efforts to supercharge its bug hunting capabilities. Meanwhile, Tenable webinar attendees shared their experience securing machine identities. And get the latest on the crypto crime explosion and on open-source developers’ compliance with the EU’s CRA law.
Here are five things you need to know for the week ending July 18.
1 - Survey: AI security tools becoming standard issue
AI security products are no longer in the “nice to have” category, and are instead becoming a staple of cybersecurity teams’ tool suites.
That’s a key finding from a survey of almost 440 cybersecurity pros conducted by the International Information System Security Certification Consortium (ISC2), which published the results this week. ISC2 looked at not just the adoption of AI security tools but also at how they are transforming teams, entry-level jobs and training.
“AI is reshaping how organizations operate, and cybersecurity is no exception," ISC2 Chief Qualifications Officer Casey Marks said in a statement. "Our latest AI Survey shows cautious but growing interest in AI security tools, with adoption expected to accelerate in the future.”
Specifically, ISC2 found that 30% of respondents are already using AI security tools, while 42% are either evaluating or actively testing them. Only 10% of respondents said they have no plans to adopt AI security tools.

What’s driving this trend? Concrete benefits. Among teams who are using AI security tools, 70% credit these new wares with improving their cyber operations.
“AI-based security tools have the potential to enhance cybersecurity capabilities, increase efficiency and reduce human error, while increasing the ability to address the growing scale and sophistication of modern threats,” reads the “2025 AI Adoption Pulse Survey” from ISC2, which is a large non-profit organization that offers cybersecurity training and certifications.
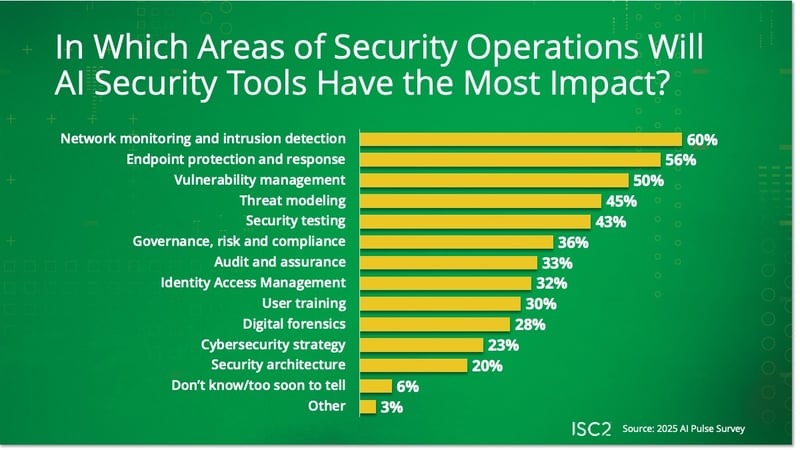
The cybersecurity areas in which respondents see AI having the greatest impact are network monitoring and intrusion detection; endpoint protection and response; and vulnerability management. Why? AI is particularly good at crunching large data sets quickly, generating insights in real time, automating repetitive tasks, and accelerating detection and responses.
However, AI use raises questions about the future of cyber roles. Over half (52%) of respondents say AI could decimate entry-level staff jobs as it takes over the repetitive, time-consuming tasks typically assigned to junior members of the team. If this happens, it could result in a significant skills gap, since less experienced cyber pros eventually grow their skills and knowledge, and take on more complex roles.
Still, 31% of respondents see a potential upside: Instead of reducing the hiring of entry-level staffers, organizations could instead assign them to areas such as AI governance, automation and security data analysis. And there’s evidence of this shift. ISC2 reports that it has seen entry-level cyber jobs advertised for AI-assisted SOC analyst; AI governance / compliance associate; and cloud security support analyst.
For more information about the uses of AI-boosted cybersecurity tools:
- “How AI is becoming a powerful tool for offensive cybersecurity practitioners” (CSO)
- “How has generative AI affected cybersecurity?” (TechTarget)
- “GenAI use cases rising rapidly for cybersecurity — but concerns remain” (CSO)
- “How AI Can Boost Your Cybersecurity Program” (Tenable)
- “How AI threat detection is transforming enterprise cybersecurity” (TechTarget)
2 - U.K.’s NCSC boosts vulnerability research efforts
In a move aimed at strengthening the U.K.’s ability to discover and tackle software bugs, the country’s cybersecurity agency has launched a new project called the Vulnerability Research Initiative (VRI).
Specifically, the VRI’s main charter will be to boost the collaboration between the vulnerability research team at the U.K. National Cyber Security Centre (NCSC) and external partners, such as other U.K. government agencies, technology companies and others.
“The VRI’s mission is to strengthen the U.K.’s ability to carry out VR. We work with the best external vulnerability researchers to deliver deep understanding of security on a wide range of the technologies we care about,” reads an NCSC statement.

The VRI will focus on partnering with external researchers to deepen the NCSC’s understanding of:
- Software product vulnerabilities
- Vulnerability mitigation
- Vulnerability research methods and tools
A core team consisting of technical experts, relationship managers and project managers will manage the VRI and be responsible for communicating research requirements to industry partners and monitoring the progress and outcomes of research efforts.
“As well as informing our advice and guidance as the National Technical Authority on cyber security, our research allows us to engage with technology vendors to encourage them to fix the bugs we find and build more secure products,” the statement reads.
The NCSC is also looking to the future, with plans to extend its engagement on specific topics, including the application of artificial intelligence to vulnerability research. Researchers and organizations interested in participating in the VRI can contact the NCSC for more information.
For recent research and analysis of software vulnerabilities, check out these Tenable blogs:
- CVE-2025-32756: Zero-Day Vulnerability in Multiple Fortinet Products Exploited in the Wild
- CVE-2025-4427, CVE-2025-4428: Ivanti Endpoint Manager Mobile (EPMM) Remote Code Execution
- Salt Typhoon: An Analysis of Vulnerabilities Exploited by this State-Sponsored Actor
- Microsoft Patch Tuesday 2024 Year in Review
- AI Security: Web Flaws Resurface in Rush to Use MCP Servers
- CVE-2025-5777, CVE-2025-6543: Frequently Asked Questions About CitrixBleed 2 and Citrix NetScaler Exploitation
3 - Tenable webinar poll looks at securing machine identities
During our recent webinar “Rage Against the Machines: How to Protect Your Org's Machine Identities,” we polled attendees on their challenges securing non-human identities. Check out what they said.
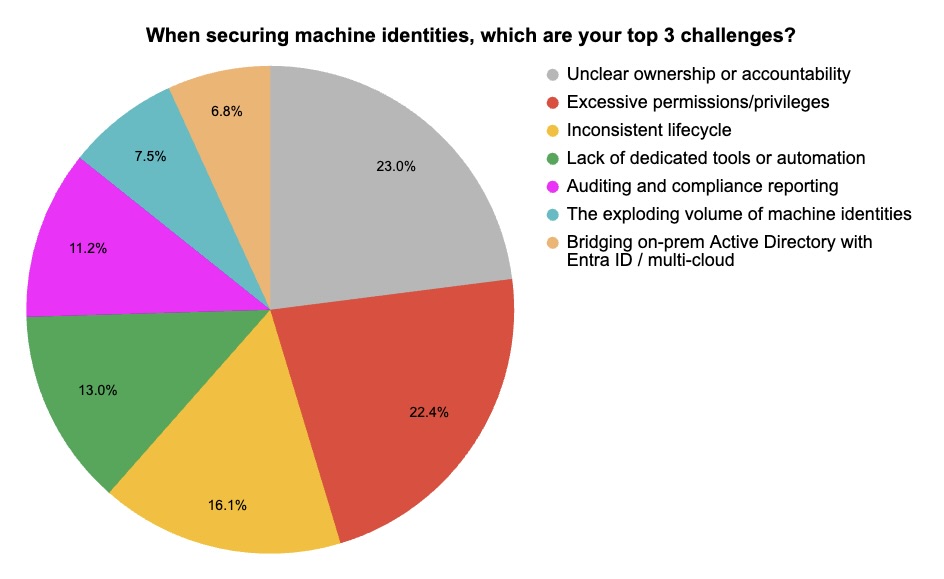
(58 webinar attendees polled by Tenable, July 2025)
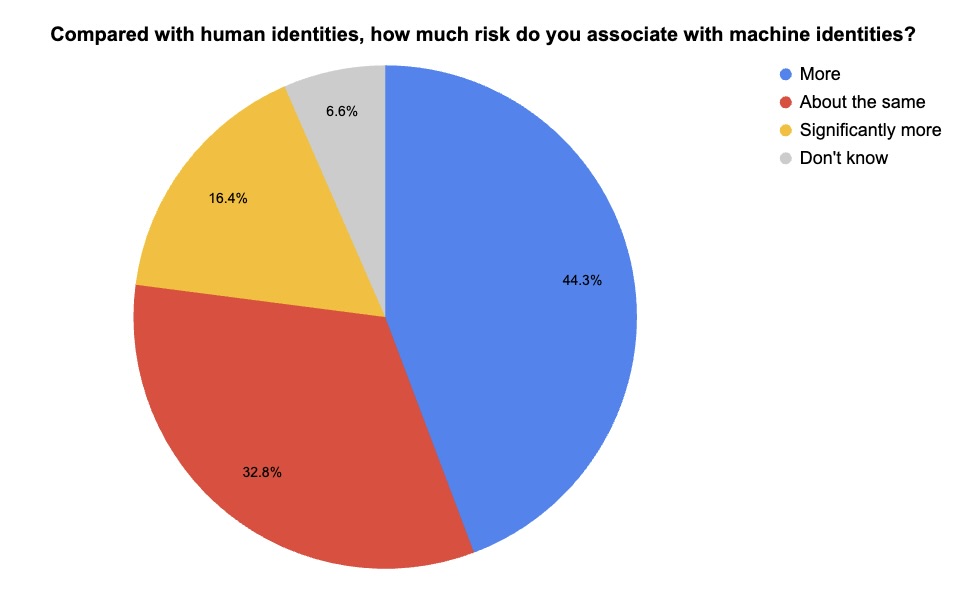
(61 webinar attendees polled by Tenable, July 2025)
To get more details about mitigating machine identity risk, watch this webinar on demand.
4 - Open source devs get guidance for CRA compliance
Developers of open source software (OSS) who want to learn more about staying compliant with the EU’s Cyber Resilience Act (CRA) now have a new resource to check out.
The Open Source Security Foundation (OpenSSF) this week published its “CRA Brief Guide for OSS Developers,” which it describes as a document meant to help OSS developers better grasp this new law’s scope and key concepts.
“If you develop OSS, we think you’ll appreciate this straightforward guide,” David A. Wheeler, Director of Open Source Supply Chain Security at OpenSSF, wrote in a blog.
“It is not legal advice; rather, it is an overview to help you understand the situation — but understanding is the first step,” he added.

Here are some high-level takeaways from the OpenSSF guide:
- Developers who publish their OSS code in their own repository, or who contribute to others’ OSS projects, are likely fine, as long as they’re not monetizing the code.
- The CRA rules kick in when your OSS is distributed as part of a commercial activity.
- When manufacturers integrate OSS components into their commercial products, they’re within the scope of compliance.
The CRA, which was adopted in October 2024, will begin to apply in December 2027, although some of its provisions will become enforceable earlier. It applies to makers of digital products — both software and hardware — that directly or indirectly connect to networks and to other devices.
The CRA outlines cybersecurity requirements for the design, development, production and lifecycle maintenance of these types of products, including that they:
- Don’t ship with known exploitable vulnerabilities
- Were built using a “secure by default” configuration
- Can have their vulnerabilities fixed via automatic software updates
- Use access-control mechanisms
- Secure the data they store, transmit and process
For more information and analysis about the EU’s Cyber Resilience Act:
- “Cyber Resilience Act Requirements Standards Mapping” (ENISA)
- “The Cyber Resilience Act, an Accidental European Alien Torts Statute?” (Lawfare)
- “EU Cybersecurity Regulation Adopted, Impacts Connected Products” (National Law Review)
- “Open source foundations unite on common standards for EU’s Cyber Resilience Act” (TechCrunch)
- “The Cyber Resilience Act: A New Era for Mobile App Developers” (DevOps.com)
VIDEO
The EU Cyber Resilience Act: A New Era for Business Engagement in Open Source Software (Linux Foundation)
5 - Report: Crypto theft balloons in 2025’s first half
Cyber thieves are doubling down on cryptocurrency targets, having already exceeded 2024’s crypto thefts. So says blockchain analysis firm Chainalysis, which this week reported that a staggering $2.17 billion was stolen from crypto services in the first six months of 2025.
The dramatic surge in crypto crime has been driven by massive breaches, including the $1.5 billion theft from ByBit attributed to North Korean cyber actors – the largest crypto hack ever. If the pace of crypto theft holds, total stolen funds could top $4 billion by year's end.
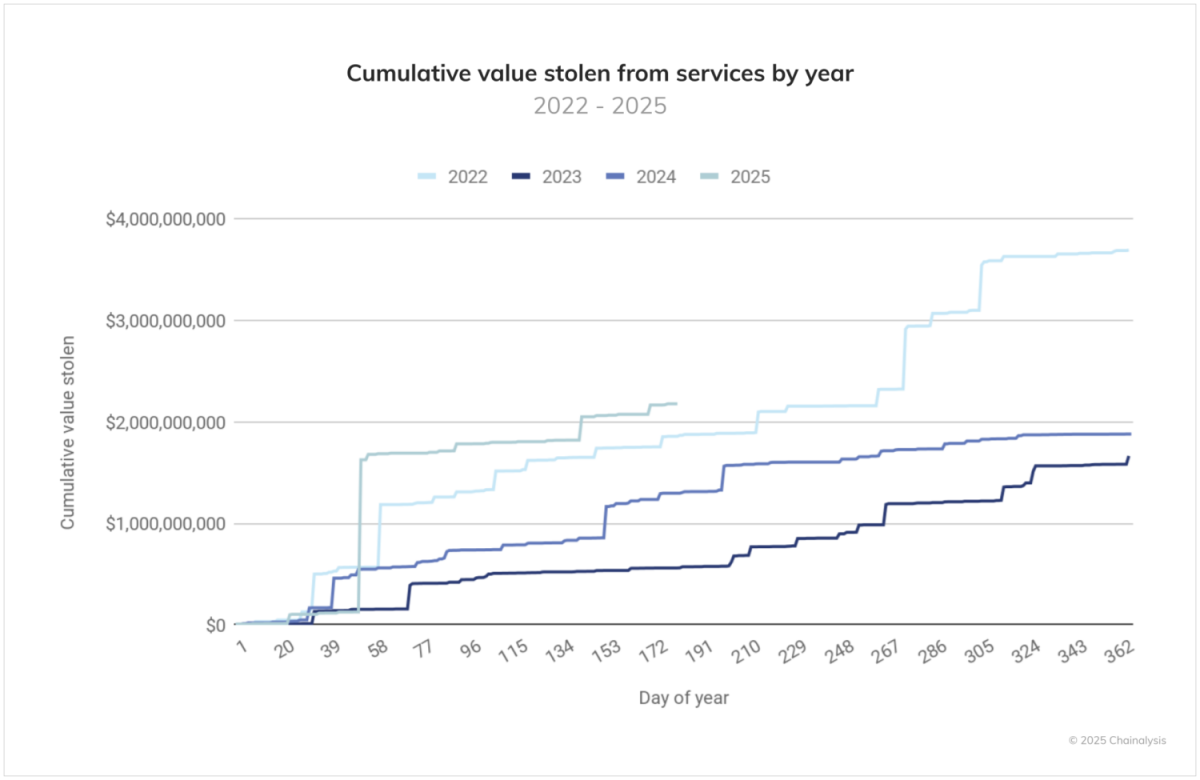
(Source: Chainalysis’ “2025 Crypto Crime Mid-year Update” report, July 2025)
Key findings include:
- Attacks on personal crypto wallets are on the upswing, accounting for 23.4% of stolen funds.
- Victims are concentrated in Canada, Germany, Indonesia, Japan, Russia, South Korea and the U.S.
- The largest growth in total victims year-on-year happened in Eastern Europe and the Middle East.
- Crypto thieves are adapting their laundering techniques, even overpaying significantly to move funds through complex chains.
“The surge in cryptocurrency thefts represents both an immediate threat to ecosystem participants and a long-term challenge for the industry’s security infrastructure,” reads Chainalysis’ “2025 Crypto Crime Mid-year Update: Stolen Funds Surge as DPRK Sets New Records” report.
To prevent and mitigate crypto crime, Chainalysis recommendations for service providers and individual users include:
- Service providers, such as exchanges, should foster robust security cultures, conduct regular code audits and adopt safeguards like multisignature hot wallets.
- Individuals should increase their focus on physical security, as violent crimes and kidnappings targeting crypto holders rise. They should also be discreet about their holdings and keep their crypto assets in cold storage wallets.
“Thus far, 2025 data present a sobering picture of how crypto crime is evolving. While the ecosystem has matured in terms of regulatory frameworks and institutional security practices, threat actors have correspondingly upgraded their capabilities and expanded their range of targets,” Chainalysis wrote.
“The industry’s response in the coming months will likely determine whether crypto crime continues its concerning trajectory or begins to plateau as defensive measures mature,” it added.
For more information about crypto cyber crime:
- “Cybercrime on the ethereum blockchain” (ScienceDirect)
- “Cryptocurrency Investment Fraud” (FBI)
- “How North Korea became a mastermind of crypto cyber crime” (Financial Times)
- “Crypto crime continues to grow, evolve” (Investment Executive)
- “Crypto crime spills over from behind the screen to real-life violence” (AP)
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- Incident Response
- Risk-based Vulnerability Management

