How Tenable’s Security Team Went from Thousands of Alerts to a Handful of Tickets with Exposure Management

Each Monday, the Tenable Exposure Management Academy provides the practical, real-world guidance you need to shift from vulnerability management to exposure management. In this post, we learn about life before and after exposure management, from members of Tenable’s own security team. You can read the entire Exposure Management Academy series here.
If you’re a cybersecurity pro, you know the drill: You log in to face a deluge of alerts from a dozen (or more!) different tools. Armed with little more than a cup of coffee and a protein bar, you forge ahead into the sea of red.
One system flags a cloud misconfiguration. Another finds a critical vulnerability. Oh, and all the while, the vulnerability management dashboard is still glowing scarlet. Like you need that reminder.
Recently, two members of the Tenable cybersecurity team, Saeed Elahi, Head of Cyber Risk and Assurance, and Arnie Cabral, Senior Staff Information Security Engineer, joined a webinar, How Tenable Optimized Security Effectiveness and Efficiency with Exposure Management, to share their journey from the kind of security chaos we just described to the clarity that comes with exposure management.
The organizational drag of disparate data
Elahi and Cabral described the initial state of their cybersecurity program. If you’re in cybersecurity, the story will ring a few bells. Like many of their peers, their security organization was built around silos. There were dedicated teams for identity management, application security and cloud infrastructure. They operated pretty well within their own domains. But each used specialized tools.
Elahi described this structure as creating “organizational drag,” with inefficient communication and challenges aligning priorities across the organization.
A visualization of the organization looked like a plate of spaghetti. But rather than a delectable Bolognese, this was a chaotic web, with data from a dozen security tools flowing from various engineering and IT teams. A lack of central aggregation made getting a unified view of the organization’s risk posture an impossibility.
Before exposure management
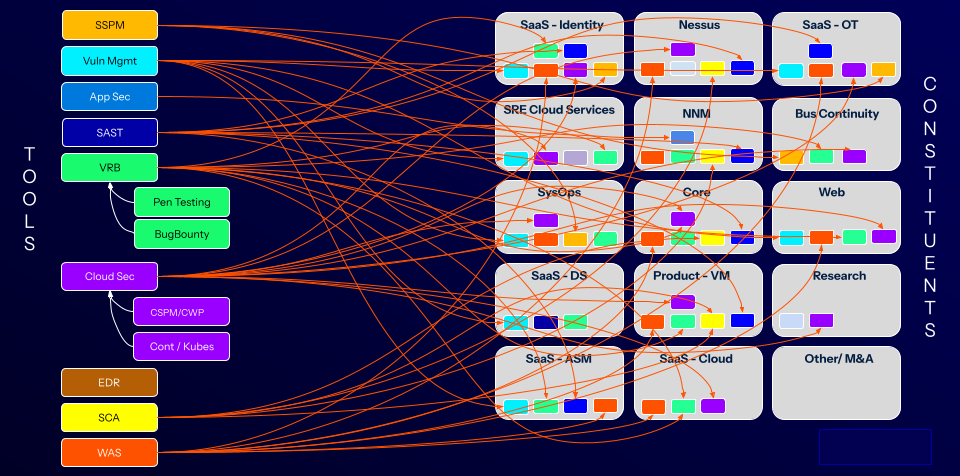
Source: Tenable, 2025
Three significant challenges arose from the silos:
- Data overload: Alerts were unrelenting and impossible to wrangle, with multiple tools often flagging the same problem on the same asset. This added up to duplicate work and overwhelmed analysts.
- No attacker’s view: Cabral said that, although internal sensors were robust, the siloed data didn’t see the whole picture. He added that not being able to see things from the bad guy’s perspective put them at a disadvantage because they couldn’t see how an attacker could piece together disparate weaknesses or exploit shadow IT assets.
- Too many manual tasks: Engineers were consumed by low value tasks like pulling data, consolidating it in a spreadsheet and correlating the findings. Daily life was a struggle to balance the need to understand the piles of data streaming in with equally critical security work.
The change catalyst
The turning point came when CSO Robert Huber issued a clear directive: Get everything into one place. And do it now!
The mandate forced a rethink. The old processes and technologies needed a thorough overhaul, and that meant the vulnerability management team went from managing about five tools to two- to three-times that number.
Like many engineers, their first thought was to build a new solution themselves. So, using a business intelligence tool, they made a valiant effort to create a custom dashboard that would unify all their security data. There’s often nothing as bracing as a first effort that doesn’t quite work. That was the case here. It was simply not feasible.
Cabral said the effort was "taking too long and costing too much money." Two months in, data was still siloed and all they’d done was some testing.
Soon, Elahi and Cabral had a strategic realization. A security program shouldn’t turn its engineers into full-time software developers. Instead, with limited resources, the team needed to focus on securing the company. So they started looking for a dedicated platform. And the solution was right in front of them.
The pivot: Finding the signal with exposure management
The team quickly moved to adopt a Continuous Threat Exposure Management (CTEM) program, in which an exposure assessment platform helped lead to a fundamental redesign of their workflow. They transformed that chaotic spaghetti diagram into an elegant, logical model with all security tools feeding into a single, intelligent system.
After exposure management
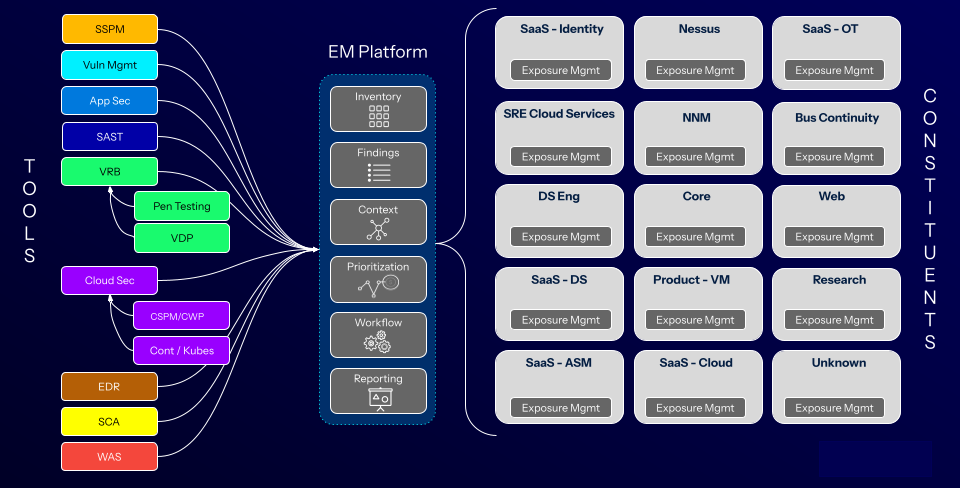
Source: Tenable, 2025
Those pesky silos, including everything from vulnerability scanners to cloud security agents, were essentially a thing of the past.
With this unified platform in place, the team gained a few powerful capabilities:
- Complete visibility: The team said that the unified platform provided an immediate and complete picture of the attack surface. They discovered “thousands upon thousands” of assets they didn’t know existed.
- Smart deduplication: The way the platform is able to understand context changed the game for the team. When three tools flagged the same vulnerability on the same server, those findings were consolidated into a single alert.
- Automated workflow: The shift eliminated all that manual drudgery. Cabral said the platform now handles the “dirty work” of automatically correlating findings and prioritizes them based on factors like exploitability and asset criticality. It also creates a single, actionable JIRA ticket that automatically goes to the right team.
Talk about night and day, right? The old problem of more noise than signal was finally solved. That flood of alerts was reduced to a trickle. And finally, the security team had a short, clear list of exactly what needed to be fixed and why.
Takeaways: Quantifiable results and reclaimed time
The results of the transition were immediate and quantifiable.
One dramatic metric jumped out. The team was able to reduce thousands of raw security alerts into just 10 actionable tickets. You read that right. It’s a pretty powerful demonstration of the value of exposure management.
But the benefits didn’t end there.
The team’s overall productivity doubled and reports that once took days of manual effort became available in seconds.
The most significant (and positive!) impact was on the team itself. Freed from all the manual administrivia, engineers could finally be engineers again. They had time to focus on more specialized, engaging, high-value work like threat hunting.
The journey of Tenable's cybersecurity team shows how security operations have evolved. By moving from a siloed, reactive model to unified exposure management, they were able to eliminate noise, increase efficiency and ultimately strengthen the company’s security posture.
Learn more
Check out the Tenable exposure management resource center to discover the value of exposure management and explore resources to help you stand up a continuous threat exposure management program.
- Exposure Management
- Exposure Management Academy


