Transforming Security: The Thousand Mile Journey Begins with a Single Step

Information security professionals are all on the same journey, to protect customer and employee data, safeguard our company’s intellectual property and trade secrets, and strengthen our company’s brand and reputation. It’s a long, difficult journey, filled with many twists and turns. But it’s our passion for security that keeps us going.
The waves of change are also surrounding us. It’s human nature to evolve; in business we strive to adapt quickly for improvements that can yield better results. But with these changes come new challenges, requiring new approaches and new solutions. This includes security.
To understand the impact of these changes, we need to understand our history. Security has always been an afterthought. We layer security controls around existing IT infrastructure. Therefore, if we don’t understand the future of IT, we won’t understand the future of security. Let’s review a few of these IT trends and changes that will continue to impact our industry.
IT infrastructure migrates to the cloud
The most significant shift in the security market is the move to the cloud
The most significant shift is the move to the cloud. I’m not just talking about the use of cloud application or cloud services, but the outright migration of IT infrastructure from corporate data centers to the cloud. This trend will affect security—drastically.
- Traditional network and infrastructure controls will no longer be an afterthought in designing and deploying systems. They will be embedded into the cloud infrastructure.
- System hardening and patching will be accomplished simply with a new image that is created and destroyed as needed.
- The perimeter is now the cloud—and the need for perimeter controls will vanish.
Last year GE announced they would move all but four datacenters to the cloud. That was 30 data centers and 9,000 workloads around the world. Why? A 52% reduction in total cost of ownership. In Australia, companies are blazing ahead with cloud deployments to offer new services, both in the public and private sectors. With the rapid growth of cloud services in Australia, AWS is looking to open a second regional zone in Melbourne just to keep up with the demand.
But that’s not the only trend impacting security.
Applications are the future
The future of security is the application. It’s the critical component of digital business and the digital economy, storing your most sensitive data and intellectual property. Think about it… Every day we use applications on our smart devices to play games, check email, talk to friends, pay bills and book travel by communicating with other cloud based applications.
The future of security is the application
As a society, we are already in the future, but security is trailing behind. We are focused on securing the infrastructure that will soon be outsourced, and ignoring the application. And it’s only getting harder, as new application technologies continually emerge. The devops and container movements are having a dramatic impact on how we secure applications and few are paying attention.
Traditional endpoints shift
Endpoint security management is changing
BYOD (bring your own device) policies move beyond the mobile device to all end user devices. Once all of your IT infrastructure is in the cloud, employees will have their choice of endpoint. Corporations might provide a stipend for employees to purchase their device of choice or just simply require them to use their own. In either case, endpoint security management is changing, including:
- Anti-virus, anti-malware and other preventive controls
- File integrity, event logging and other monitoring controls
- Forensics, incident investigation and other response controls
Ultimately, these endpoint security controls will be embedded in the base operating system or integrated within the hosts by the cloud providers rather than implemented as stand-alone security controls.
Layered security creates gaps
Defense in depth leaves gaps in our security defenses
It’s obvious our approach to security is outdated. Defense in depth has created a culture of deploying isolated, point solutions that leave gaps in our security defenses. It’s these gaps that allow attackers to hide from detection, thus maximizing potential exposure and loss to the organization. Not only is the approach outdated; the technologies we’re deploying today won’t address the needs of the future. In our future world, these gaps get bigger before they get smaller. We need a new approach to resolve these gaps today and in the future.
Transforming security
It’s time to transform our approach to security. We must look at our security defenses as an integrated, holistic set of capabilities, working together to continuously improve our security defenses. We need to focus on capabilities, not tools.
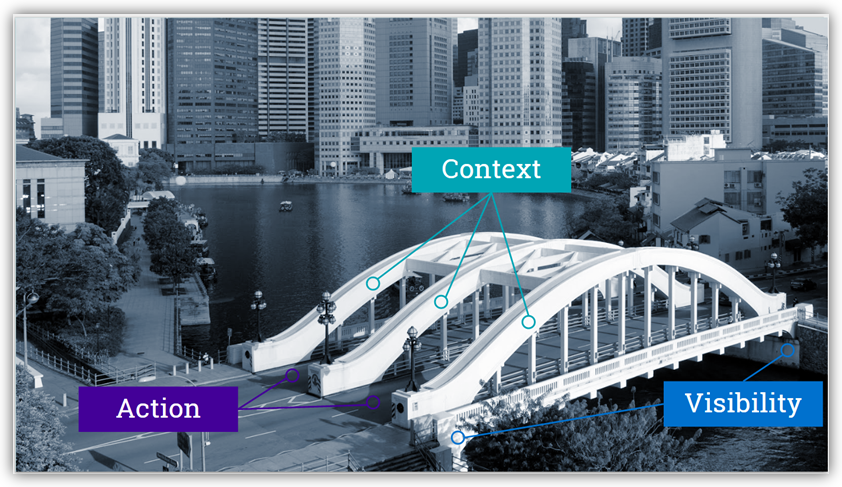
Bridging the gaps
On every journey, we’ll encounter gaps along the route. We need to bridge these gaps to continue on.
Before we begin our new security journey, let’s define the elements needed to build the bridge.
A bridge requires a strong foundation. Use the Visibility domains of Discover and Assess to build the foundation of the bridge; Discover to inventory your infrastructure and to eliminate blind spots; Assess to evaluate the security state of each asset and address any weaknesses. A strong foundation provides a resilient security roadmap.
With a foundation in place, you need spans to support the road. Use the Context domains of Monitor and Analyze to span the bridge. Monitoring the activities of your assets creates the long spans across the gaps, while analysis supports the future road.
With the supports in place, it’s time for the road, enabling action. Use the Action domains of Respond and Protect to build your road. Rapid response minimizes exposure and loss, while protection allows for future automation.
The journey
The journey to comprehensive security is fraught with gaps and delays. Take each leg of the journey one step at a time, being careful to check back with your roadmap plan for guidance.
- Inventory all your assets – You can’t protect what you aren’t aware of. This is the first step on your journey, and the one step that is commonly skipped.
- Continuously assess device vulnerabilities – Regardless of your route, device vulnerabilities will always be landmines along the way.
- Assess application vulnerabilities – On your journey to the future, your main focus will change to application vulnerabilities rather than device vulnerabilities. Check such new landmarks as containers and microservices.
- Audit security configurations – Misconfigurations in device settings, cloud applications and cloud services can veer you off course. These are the core visibility areas that clear the way for your journey.
- Monitor and analyze all logs – Your map details expand as you drive into the future. Check network and device logs, but also be sure to monitor application, cloud service and cloud infrastructure logs.
- Monitor and analyze all user accounts – There are lots of other vehicles on the road with you. Drive defensively; check user controls and their access to all applications.
- Monitor and analyze all network traffic – As you leave the confines of your perimeter, you need to constantly check the traffic and behavior in the cloud.
- Respond to all incidents – Incidents are now prioritized, based on the intelligence you have gathered along the way. Stop and respond to critical incidents that impact your progress.
- Automate remediation – The final step requires trust in the data and analytics you have gathered. Just as it requires trust in technology to ride a self-driving car, so your journey into the future of security takes a while to achieve trust in cloud deployments.
The journey from defense in depth security to comprehensive security requires planning, a detailed map, and accurate directions. The route may be long, but your end goal is readily achieved if you take it one step at a time.
Reaching your destination
The security journey may start with a small step, but it is a challenging adventure through threats, attacks, and vulnerabilities. Plan your trip wisely and map out your priorities carefully to move toward your destination of comprehensive security for a brighter, more resilient future.
This blog is based my talk at the RSA Conference 2016 in Singapore. See the complete presentation on the RSA website.
This blog was updated on August 10, 2016.
- Security Policy