by Josef Weiss
June 3, 2021
A benefit of an effective database security program is that organizations are better positioned to safeguard against the risks of compromise, and to thwart attacks such as malware and ransomware. Steps to building such a program include following best practices and regulatory requirements. Key initiatives include conducting and reviewing vulnerability assessments, and compliance audits.
Databases typically contain sensitive material such as financial data, personnel information, business intelligence, client information, and more. Organizational secrets were once contained in a locked file cabinet, within secure rooms, or entombed deep within an organization. Access was controlled with a key requiring on-site access, and copying or removing files was difficult at best. Today this information is commonly stored in a database that is connected to a wider network. Configuration errors can inadvertently provide access to a global audience. This practice makes a database a primary target of threat actors. Compromised databases are a common element of most data breaches, resulting in the exfiltration or loss of massive amounts of privileged information.
Information that is collected and stored in a database is important, and safeguarding that data is critical to business continuity. Costs associated with damages, fees, legal considerations and loss of reputation resulting from damaged and corrupt databases can be a financial burden for any organization. Depending on the type of data being stored, many established regulations and standards exist, which reduce the risk that information will be mishandled. Successful implementation means that customer confidence is maintained and organizations avoid costly financial ramifications.
Organizations are obligated to protect sensitive data, and many times comply with laws and regulations regarding the data being stored. To best accomplish this, database teams require vulnerability details which easily identify the most significant vulnerabilities, and provide guidance towards mitigation. The ability to act quickly in mitigating database vulnerabilities requires information to be presented in a manner which focuses on findings that should be prioritized and mitigated first. As a result, vulnerability remediation is more successful, the attack surface is reduced, and efforts can be visually tracked and measured against established goals.
Tenable.sc provides a risk-based view of your IT, security and compliance posture, allowing database teams to analyze findings, remediate identified risk, track progress, and measure success. Designed with the principles of the Cyber Exposure Lifecycle in mind, this dashboard assists database teams in maintaining a high level of awareness and vigilance. The dashboard is tailored to guide the database team in detecting, predicting, and acting to reduce risk across their entire attack surface. Components not only include detailed vulnerability findings, but also provide guidance on remediation actions that will reduce the greatest risk first. Database compliance components assist database teams by presenting pass/fail compliance results. Compliance results also include details for manuals checks which allow teams to follow up on items such as disaster recovery plans, backup policies, and backup integrity validations. Utilizing Tenable’s Predictive Prioritization technology of combining vulnerability data, threat intelligence and data science, this dashboard directly benefits database teams in determining where to start when navigating a sea of vulnerabilities.
The dashboard components do not require specific asset list filters to be applied prior to use. However, organizations that have teams that do focus on a specific group of assets will benefit from using custom asset lists. Database teams can visualize findings against database assets within the organization using this method. Additionally, setting an Output Assets filter provides greater insight into where additional resource need to be allocated to mitigate vulnerabilities.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessments.
The dashboard requirements are:
- Tenable.sc 5.18.0
- Nessus 8.14.0
Tenable.sc unifies security data from across the organization, providing a single-pane-of-glass to view and understand the organizations overall security posture. Using a diverse array of sensors, administrators have complete visibility into network connected assets with comprehensive vulnerability assessment coverage. When a security vulnerability is identified Tenable.sc quickly provides alerts via workflows and notifications, which speed up incident response and vulnerability remediation.
This dashboard contains the following components:
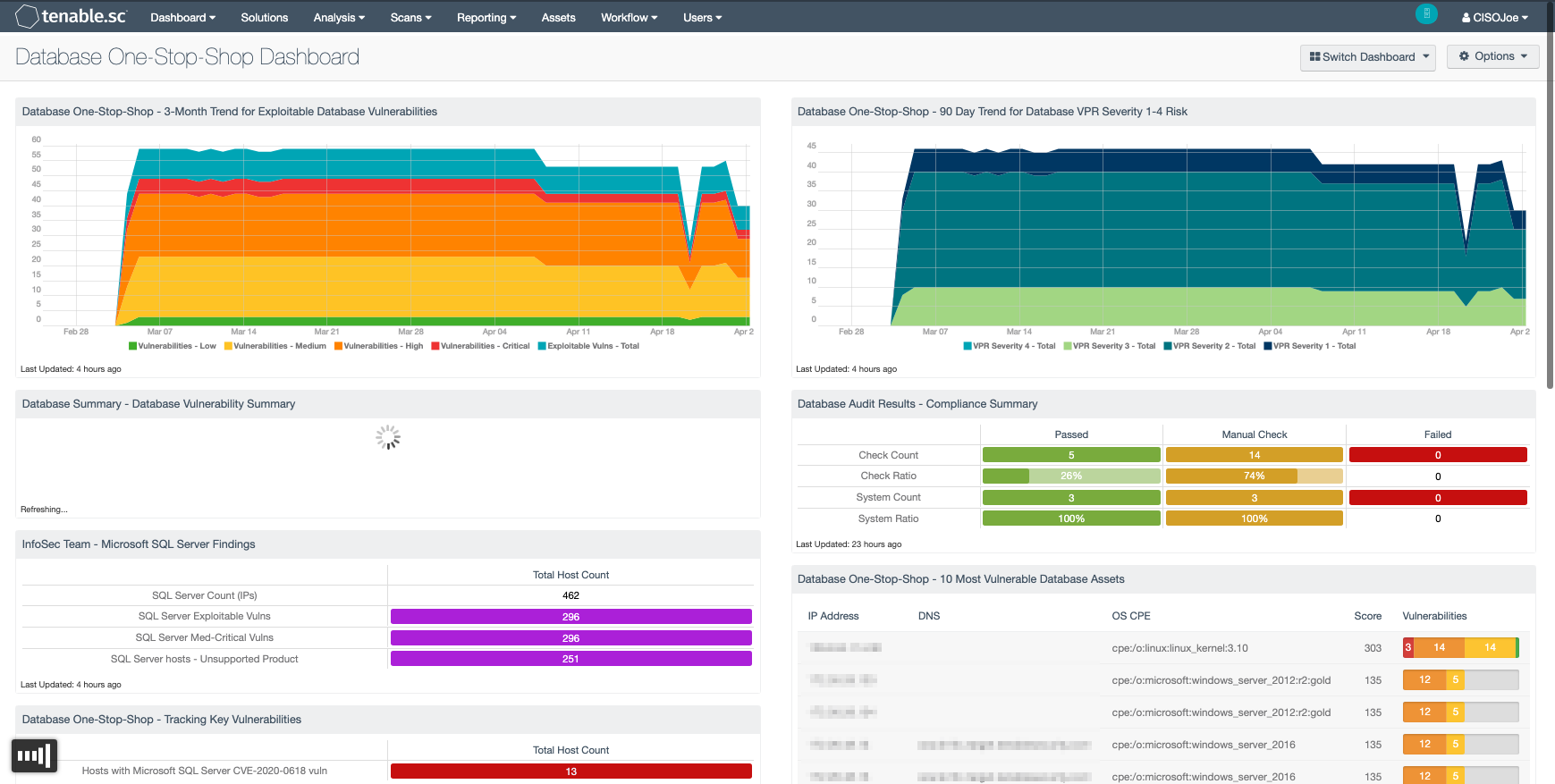
- Database One-Stop-Shop – 3 Month Trend for Exploitable Database Vulnerabilities - This component displays a 3-month graph across two separate data series.
- Database Summary – Database Vulnerability Summary - This component displays various defined technologies by row, and enumerates any found vulnerabilities across the columns.
- Infosec Team – Microsoft SQL Server Findings - This matrix displays a count of the Microsoft SQL Servers in the environment, along with vulnerability findings.
- Database One-Stop-Shop – Tracking Key Vulnerabilities - This matrix tracks the total number of vulnerable hosts by key vulnerabilities such as CVE-2020-0618 (SSRS)
- Database One-Stop-Shop – New Database Vulnerabilities Published in the Past 30 Days - This table presents the top new database vulnerabilities present in the environment that have been published in the last 30 days.
- Database One-Stop-Shop – Top CVE for Your Environment - This table uses CVE identifiers from 2000 to present to display database vulnerability findings, along with their severity rating.
- Database One-Stop-Shop – Unsupported Database Software - This table displays all unsupported database software by name, sorted by severity.
- Database One-Stop-Shop – 90 Day Trend for Database VPR Severity 1-4 - This area chart displays a 90 day trend for VPR (Vulnerability Priority Rating) Severity 1-4.
- Database Audit Results – Compliance Summary - The Database 90-Day Compliance Summary line chart provides analysts with a historic view of compliance status over the past 90 days.
- Database One-Stop-Shop – Worst of the Worst FIX THESE FIRST - This table utilizes the vulnerability summary tool to focus on the top 10 database vulnerabilities that should be remediated first.
- Database One-Stop-Shop – 10 Most Vulnerable Assets - This table provides information on the Top 10 most vulnerable database assets.
- Database One-Stop-Shop – Exploitable Vulnerabilities (Sorted by VPR Severity) - This table presents the top new exploitable database vulnerabilities present in the environment that have been published in the last 30 days.
- Database One-Stop-Shop – Top 10 Prioritized Actions to Reduce Risk - This table displays the top 10 database remediations.