Cybersecurity Snapshot: Insights on Log4Shell, the Metaverse, IoT, Pig Butchering, Active Directory

Get the latest on Log4Shell’s global remediation status; the need for metaverse security rules; a shutdown of “pig butchering” domains; tips for secure IoT products; an informal poll about AD security; and more!
Dive into six things that are top of mind for the week ending Dec. 2.
1 - Tenable: 72% of organizations still vulnerable to Log4Shell
Tenable this week provided an eye-opening reality check into the global remediation status of the Log4Shell vulnerability. To assess the scope and impact of Log4Shell – discovered almost a year ago – Tenable’s Research team conducted a telemetry study based on data collected from over 500 million tests and found that as of October 1, 2022:
- 72% of organizations remain vulnerable to Log4Shell.
- After being fully remediated, 29% of vulnerable assets saw the reintroduction of Log4Shell.
- Among North American organizations, 28% have fully remediated, followed by Europe, Middle East and Africa (27%); Asia-Pacific (25%); and Latin America (21%).

These results show how difficult it is to attain full remediation for this pervasive vulnerability in the ubiquitous Log4j component, and serves as a reminder that vulnerability remediation isn’t a “one and done” effort, Tenable Chief Security Officer Bob Huber said.
“Eradicating Log4Shell is an ongoing battle that calls for organizations to continually assess their environments for the flaw, as well as other known vulnerabilities,” Huber said.
For more information, read Tenable’s press release. You can find more coverage and analysis about the findings at TechTarget, Security Week, Inside Cybersecurity, BetaNews and ISSSource.
For more guidance on Log4j, check out:
- Tenable’s Log4j resource page
- U.S. government advisory on APT exploit of Log4Shell to breach agency
- Log4j guidance from the U.S. Cybersecurity and Infrastructure Security Agency (CISA)
- CISA’s Cyber Safety Review Board Log4j event review
2 - CISA beefs up critical infrastructure resilience plan
CISA has updated its Infrastructure Resilience Planning Framework (IRPF), which it first released in 2021 to help state, local, tribal and territorial governments draft better plans for protecting their critical infrastructure assets – both digital and physical.

“Because so much of a community’s physical infrastructure is now controlled, in whole or in part, by computers and connected through the internet, planning should consider sound policies and procedures for incorporating cybersecurity improvements into the infrastructure development lifecycle,” reads the document.
For more information about the cybersecurity of critical infrastructure, industrial control systems (ICS) and operational technology (OT):
- “The OT Security Dozen – a 12-part series on building an OT/ICS cybersecurity program” (ISA Global Security Alliance)
- “OT/ICS cybersecurity threats remain high” (Security Magazine)
- “Three U.S. Policy Recommendations to Strengthen OT Cybersecurity” (Tenable)
- “Guide to Industrial Control Systems (ICS) Security” (National Institute of Standards and Technology - NIST)
- “Control System Defense: Know the Opponent” (CISA)
3 - U.S. seizes “pig butchering” domains used to steal millions
The U.S. Attorney’s Office for the Eastern District of Virginia has taken down seven domains used by cyber criminals in so-called “pig butchering” scams where five victims lost $10 million in recent months.
In these social engineering long cons, fraudsters contact victims via digital channels, such as social media platforms, text messages and dating apps, patiently lure them into a false romantic relationship and then dupe them into handing over money.
Five people in the U.S. were victimized using these seven domains, which spoofed domains of the Singapore International Monetary Exchange as part of a ploy to convince the victims to invest in a non-existent cryptocurrency opportunity.
In October, 11 people were arrested for allegedly participating in “pig butchering” scams in which more than 200 victims were defrauded of almost $18 million.
For more information about “pig butchering” scams:
- “Cryptocurrency Investment Schemes” (U.S. Federal Bureau of Investigation)
- “Massive Losses Define Epidemic of ‘Pig Butchering’” (Krebs on Security)
- “Satnam Narang breaks down how Pig Butchering scams work” (Ticker Insight)
- “What’s a Pig Butchering Scam?” (ProPublica)
- “How One Man Lost $1M To A Crypto ‘Super Scam’ Called Pig Butchering” (Forbes)
4 - A temperature check on Active Directory security
As the primary method for user authentication and authorization for 90% of the Fortune 1000, Microsoft’s Active Directory (AD) remains a prime target for cyber attackers. At a recent Tenable webinar, we polled attendees about their approach to AD security, as well as their challenges and priorities. Check out the results below.
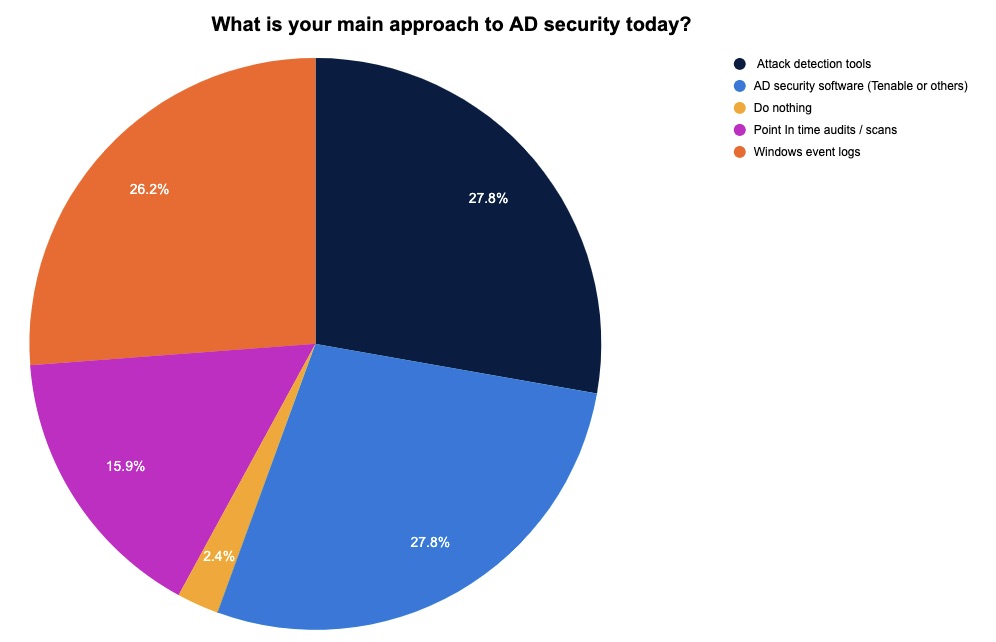
(126 webinar attendees polled by Tenable, November 2022)
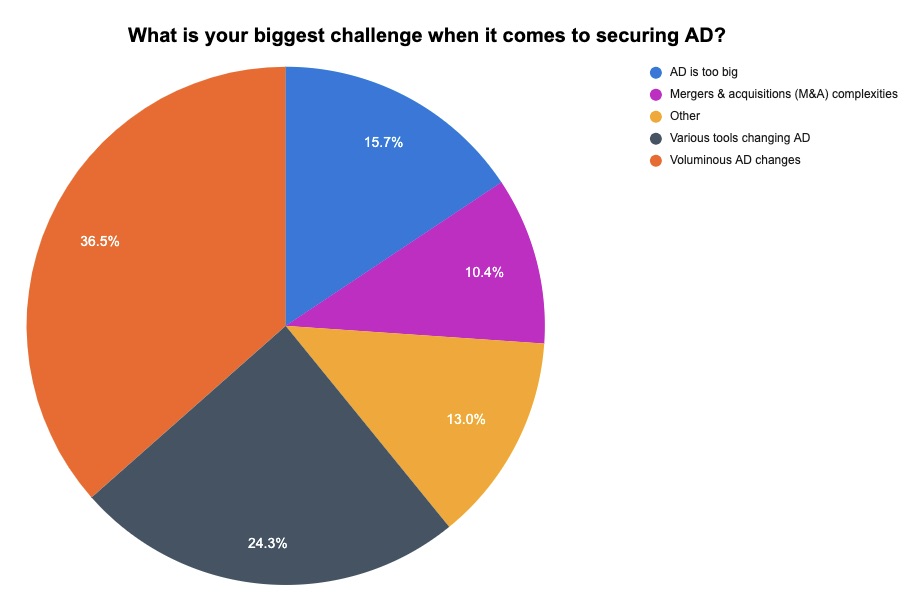
(115 webinar attendees polled by Tenable, November 2022)
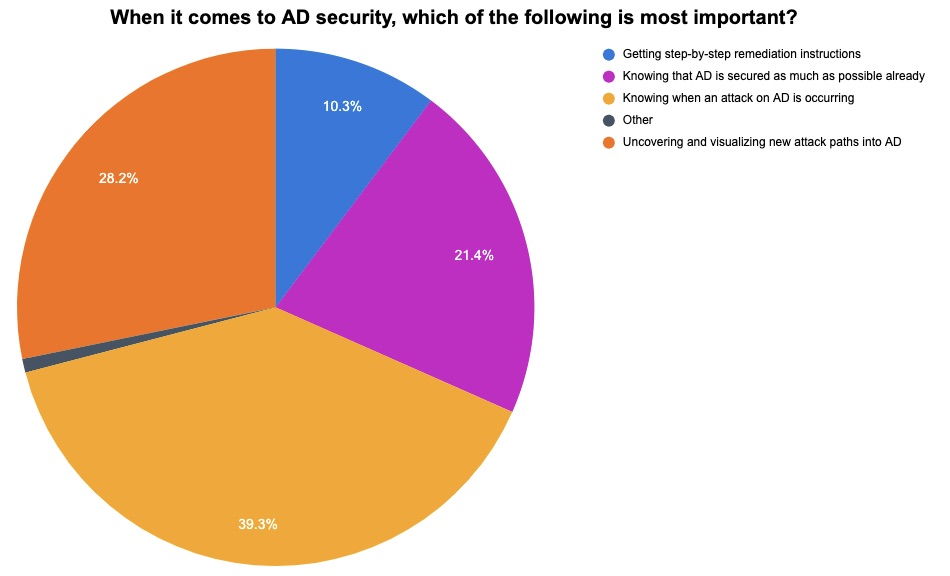
(117 webinar attendees polled by Tenable, November 2022)
For more information about AD security, check out these Tenable resources:
- “Adopt a Proactive Process for Detecting and Preventing Attack Paths in AD” (webinar)
- “Active Directory Security Needs Immediate Attention” (white paper)
- “How Sanofi Successfully Protects Its Global AD Infrastructures” (case study)
- “How Threat Actors Leverage AD Flaws in Ransomware Attacks” (blog)
5 - Study: Community guidelines urgently needed in the metaverse
Although the metaverse is still in its early stages, many people already are enthusiastically participating in the immersive experiences of social virtual reality (VR), creating an urgent need for metaverse platforms to establish clear community guidelines.
That’s according to the white paper “A Secure and Equitable Metaverse” from the University of California’s UC Berkeley Center for Long-Term Cybersecurity (CLTC,) which looks at user interactions in social VR, including instances of hate and harassment, reviews existing community guidelines and offers recommendations.

The guidelines, according to the study, should be:
- Accessible, meaning they’re clear and easy to understand
- Comprehensive, in that they should outline “broad, high-level principles” along with more specific “mid-level policies” addressing categories of online harm
- Specific, meaning they should detail what constitutes violations
- Transparent, so that they clearly explain the rationale and values behind the rules and policies
To get all the details, read a blog about the white paper and the full 74-page document.
For more information about metaverse cybersecurity:
- “Why privacy and security are the biggest hurdles facing metaverse adoption” (VentureBeat)
- “Europol: Police chiefs need to get hip to the metaverse” (Tenable)
- “The metaverse is coming, and the security threats have already arrived” (ZDNet)
- “Top metaverse cybersecurity challenges” (TechTarget)
- “The metaverse has a groping problem already” (MIT Technology Review)
6 - Tips for building more secure IoT products
Security has often been an afterthought when designing and developing internet of things (IoT) devices and systems, making many of them notoriously vulnerable to cyber attacks. Now the Cloud Security Alliance has identified key security challenges faced by makers of IoT products along with recommendations for overcoming them. Here’s a sampling of CSA’s guidance:
- Because attackers can easily reverse-engineer IoT products to discover their vulnerabilities, IoT vendors should design them so that they automatically install firmware and software updates that fix critical security flaws.
- Foster an awareness of the importance of security by training developers in IoT security, as well as create a framework for threat modeling the products.
- When choosing technologies to build IoT products, take into account not only performance criteria but also security, and take advantage of security features offered by IoT components.

For more information about IoT security:
- “What is IoT security?” (TechTarget)
- “Secure IoT Best Practices” (IoT Security Foundation)
- “A framework for securing the IoT ecosystem” (Tenable)
- “Securing the Internet of Things” (U.S. Department of Homeland Security)
- “Guidance for testing IoT security products” (Tenable)
- Active Directory
- Cybersecurity Snapshot
- Government



