Verizon’s 2016 DBIR Report

The Verizon 2016 Data Breach Investigation Report (DBIR), published earlier this week, includes key insights on real-world data breaches and the evolving threat landscape. The DBIR continues to be one of the most important reports for organizations each year because it includes data from security vendors and organizations worldwide, revealing information on the past year’s breaches and security incidents.
The 2016 DBIR uses data from 67 contributing organizations
For this year’s report, Tenable contributed data for analysis to help the Verizon DBIR team paint the clearest picture of threats, vulnerabilities, and actions that lead to security incidents.
The 2016 report helps you understand how cybersecurity breaches occur, what the most likely attack types are for your industry, and what techniques you can adopt to reduce the risk. This blog summarizes key findings from the 2016 report.
Breach trends
Similar to findings from previous years, according to the 2016 DBIR, most attacks still come from outside the organization, and the two motivators for attackers continue to be money and espionage. This year’s report also emphasizes that attackers are getting quicker all the time. Time to compromise is minutes (81.9%), while time to exfiltrate data is between days (67.8%) and minutes (21.2%).
Even more disturbing, external breach notifications are up, while internal breach detection is down. This means organizations rarely discover on their own that they have been breached; the first time they know they’ve been compromised is when law enforcement, a fraud detection service, or a third party notifies them.
Attackers are getting quicker all the time. External breach notifications are up, while internal breach detection is down.
Even with security tools and experienced staff in place, it’s still difficult to detect threats. If you don’t have the right solution in place to continuously monitor your network and proactively identify suspicious or malicious activity, detecting whether or not your data has already been stolen can be a nearly impossible task.
Phishing
The DBIR combined the results of over eight million phishing tests in 2015 from multiple security awareness vendors and found that the mean time from the start of a phishing campaign to first click is 3 minutes and 45 seconds. In less than 4 minutes, an attacker can gain a foothold on your network.
Social threats like phishing are hard to defend against, even when you have a comprehensive training and awareness program in place related to social engineering threats that employees may face; a unified, robust monitoring solution can identify early signs of a compromise. Often, core pieces of security exist – anti-virus deployments, intrusion detection sensors, and NetFlow capture are available. But they don’t do any good if they are not used. For example, anti-virus can be installed on all corporate assets, but if it is a mishmash of products installed by IT over the years, gaps can occur.
To help protect against phishing attacks, use a unified security assurance solution to make sure anti-virus solutions are enabled and updates are regularly rolled out across the company. Also, make sure you are using a security assurance solution that can correlate intrusion detection alerts and NetFlow capture. By using these tools together, you can quickly identify emergent threat actors from phishing attacks before significant damage occurs.
Stolen credentials
The Verizon 2016 DBIR reveals that 63% of breaches used weak, default or stolen credentials. To protect against stolen credentials and outsmart attackers, the best approach is still going back to the basics:
- Perform configuration auditing for password strength controls
- Segment and continuously monitor your network
- Enable two-factor authentication
- Keep track of which credentials are used where, when and by whom, and rotate passwords frequently
- Flag and investigate any anomalies
Make sure you monitor how users behave once they log into systems, to understand what bad behavior looks like. Also consider evaluating new technologies that will help you move away from passwords altogether, replacing passwords with newer technology, such as Universal Two Factor (U2F), which gives users the ability to authenticate their identities with biometrics like fingerprints or iris scanners.
Exploited vulnerabilities
According to the 2015 DBIR, 99.9% of the exploited vulnerabilities were compromised more than a year after the CVE was published, and we continue to see this trend in the 2016 DBIR. Older and well-known vulnerabilities continue to be the source of most attacks, with the top 10 known vulnerabilities accounting for 85% of successful exploits. However, the other 15% is made up of over 900 vulnerabilities.
The 2016 DBIR report also highlights how time from vulnerability publication to exploitation varies. For example, the following figure from the Verizon 2016 DBIR illustrates that Adobe and Microsoft vulnerabilities are exploited quickly, while other vulnerabilities, such as Mozilla vulnerabilities, take longer to exploit after disclosure. This data gives you the context you need to focus and prioritize your remediation efforts more effectively.
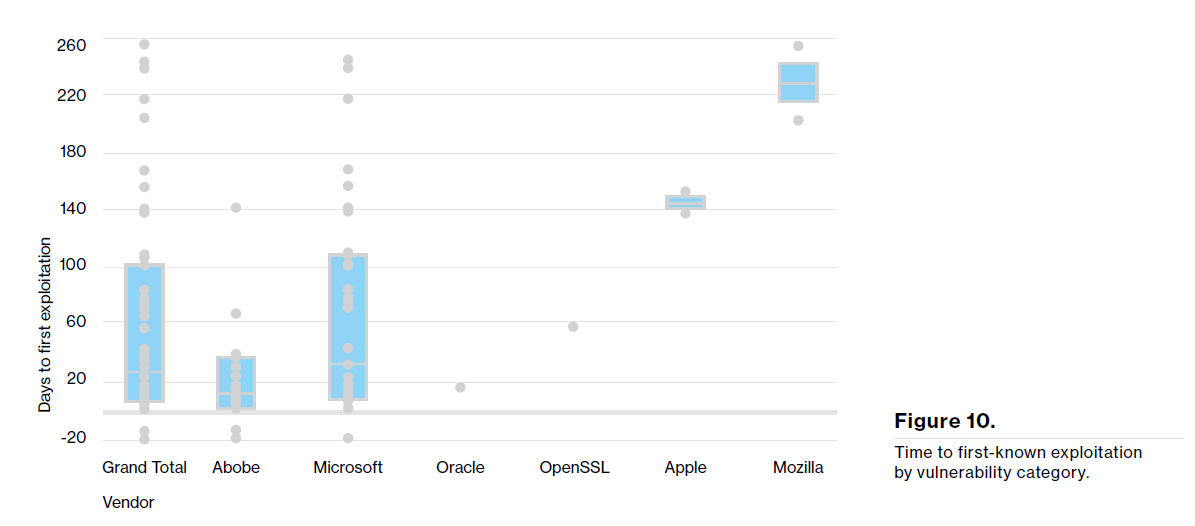
Once again the 2016 DBIR recommends vulnerability scanning as a way to help identify new devices, services, and changed configurations. The key to any scanning program is to reduce or eliminate your between-scan blindness. Simply running a quarterly, monthly, or weekly scan is not sufficient. Active scanning must be combined with passive network traffic monitoring to enable continuous discovery of new devices, services, and vulnerabilities in near real time. A comprehensive security assurance program, which includes vulnerability management and continuous monitoring, will always be more effective at preventing data breaches than “fire drills” focused on the “threat of the day.”
Mobile and Internet of Things
Just as in last year’s report, the 2016 DBIR still shows no significant data on breaches involving mobile or IoT. This could be sample bias, or it could be that these areas just aren’t as big of a threat as many corporate marketing departments would lead you to believe.
However, that does not mean that mobile and IoT should not be included in an organization’s risk assessment strategy and security program. The threat environment continues to evolve, so it’s a good practice to monitor and secure all devices—be they desktops or mobile—to make it more difficult for attackers to gain entry.
Make the Verizon 2016 DBIR actionable for your organization
The Verizon 2016 DBIR is loaded with statistics and analysis about the threats, vulnerabilities, and actions that lead to security incidents. However, the process of gathering and analyzing the data needed to act on Verizon’s recommendations is an iterative, challenging, and time-consuming process. Most organizations simply don’t have the time to manually extract data from different parts of the business and iteratively filter and convert the information into security monitoring and an actionable program.
Use Tenable dashboards to gain visibility, context, and actionable intelligence from the DBIR findings
To help your organization get the most out of the findings in the Verizon DBIR, in 2015 Tenable created easy-to-use Verizon DBIR dashboards that collect contextual information about attack patterns based on several sections of the 2015 DBIR to give you the visibility, context, and actionable intelligence you need to apply DBIR information to your own networks:
- Verizon 2015 DBIR - Browser Vulnerabilities
- Verizon 2015 DBIR - Vulnerabilities & Malware Collection
- Verizon 2015 DBIR - Account Weakness
- Verizon 2015 DBIR - Incident Pattern Monitoring
- Verizon 2015 DBIR - Indicators of Compromise
These dashboards, available in SecurityCenter Continuous View™, leverage a unique combination of active scanning, agent scanning, continuous listening, and host data activity monitoring technologies to help you quickly identify whether the top vulnerabilities identified in the Verizon DBIR are in your environment, and if your organization is a victim of malware or advanced threats.
Coming soon: new and updated Verizon 2016 DBIR ARCs and dashboards
The Verizon 2015 DBIR dashboards from Tenable are still highly relevant to the findings in the Verizon 2016 DBIR. However, we also plan to update and release new Verizon 2016 DBIR Assurance Report Cards (ARCs) and dashboards for SecurityCenter Continuous View based on Verizon’s 2016 findings.
The Tenable researchers have completed their initial analysis of the 2016 Verizon DBIR, and development of new ARCs and dashboards is underway. We will post information about these new ARCs and dashboards to our blog and in the SecurityCenter feed as they become available, so stay tuned for more information!
Take the time to dive deeper
Overall, the 2016 DBIR provides a level of information about breaches that few other reports can match, as well as a high level of transparency about the data and methodologies used to generate the report. As a result, the DBIR continues to be one of the most important reports for organizations each year.
Understanding the data breach scenarios that are relevant to you, your industry, and your asset landscape is key to smart security. This summary just scratches the surface of Verizon’s findings. Make sure you read the entire DBIR report to learn about other key findings relevant to your organization.
- Announcements
- Dashboards
- Research Reports
- SecurityCenter

