Produkte von Tenable
Isolieren und beseitigen Sie wichtige Cyberrisiken, die Ihr Unternehmen gefährden.
Nehmen Sie vorrangige Cyber-Schwachstellen ins Visier – von der IT-Infrastruktur über Ihre Cloud-Umgebung bis hin zu Ihrer kritischen Infrastruktur und allen dazwischen liegenden Bereichen. Entscheiden Sie sich für eine einzelne Exposure-Lösung oder schützen Sie Ihre gesamte Angriffsfläche mit Tenable One, der branchenweit einzigen End-to-End-Plattform für Exposure-Management.
Exposure-Lösungen von Tenable
Schließen Sie Ihre Cyber Exposure-Lücken.
Optimieren Sie die Risikoreduzierung mit KI-gestützten Exposure-Lösungen, die kontinuierlich voneinander lernen, um die Risikoreduzierung durch ganzheitliche Erkenntnisse zu ergänzen, die Ihre gesamte Cybersecurity-Situation verbessern.
Beheben von Sicherheitslücken in der Cloud
mit der handlungsfähigen Plattform für Cloud-Sicherheit.
Reduzieren Sie Risiken, indem Sie schnell die wichtigsten Sicherheitslücken aufdecken und schließen, die durch Fehlkonfigurationen, risikoreiche Berechtigungen und Schwachstellen entstehen.
Beheben von Schwachstellen
mit der weltweiten Nr. 1 in Sachen Schwachstellen-Management
Reduzieren Sie Risiken, indem Sie alle folgenschweren IT-Schwachstellen identifizieren, die wirklich wichtigen ermitteln und kritische Sicherheitslücken in kürzester Zeit schließen.
Beheben von
OT-Cyberrisiken
mit der einheitlichen Industrial-Security-Lösung für konvergente OT/IT-Umgebungen.
Verringern Sie Risiken, indem Sie sich mit einer einzigen Lösung einheitliche Transparenz, Erkenntnisse und Kontrolle über OT-, IoT- und IT- Assets verschaffen.
Beheben von Identity-Risiken
mit der unerlässlichen Lösung für das identitätsorientierte Unternehmen.
Reduzieren Sie Risiken, indem Sie Sicherheitslücken in Ihrer gesamten Identity-Umgebung aufspüren und beheben, um identitätsbasierte Angriffe zu verhindern.
Sicherheitslücken in der Cloud
Schwachstellen
OT-Cyberrisiken
Identity Exposure
Kostenfreie Produkte von Tenable
Tenable One
Die weltweit einzige Plattform für lückenloses Exposure-Management
Gewährleisten Sie umfassende Sichtbarkeit und handlungsrelevante Erkenntnisse entlang der gesamten Angriffsfläche
Fragmente zusammenfügen
Holen Sie sich den weltweit einzigen allumfassenden Überblick über die Cyberrisiken in Ihrer gesamten Angriffsfläche und bringen Sie die gefährlichsten Sicherheitslücken ans Licht–– über alle Arten von Assets und Angriffspfaden hinweg.
Datenzusammenhänge herstellen
Profitieren Sie von einer einzigen, zentralen Quelle für verlässliche und aufschlussreiche Informationen zur Angriffsfläche und stellen Sie Zusammenhänge aus gänzlich verschiedenen Datenpunkten her, um die vorrangigen Probleme und toxischen Risikobeziehungen zu identifizieren, die die Exposure Ihres Unternehmens in die Höhe treiben.
Silos überwinden
Mobilisieren Sie Ihre Business- und Sicherheitsteams, um Ihre größten Cyberrisiken zu beseitigen, und reduzieren Sie so das Unternehmensrisiko– vom Netzwerk über die Cloud bis hin zu operativen Technologien und allen dazwischen liegenden Bereichen.


Umfassende Inventarisierung
Dynamisches Angriffspfad-Mapping
Predictive Prioritization
Mobilisierung und Problembehebung
rweiterte Analysen und Berichterstattung

Beschleunigen Sie Suchvorgänge, Erkenntnisse und Maßnahmen mit generativer KI, die versteckte Risiken aufdeckt und das Sicherheits-Know-how in Ihrer gesamten Umgebung erweitert.
Gewinnen Sie einen einheitlichen Überblick über sämtliche Assets und Risiken auf der gesamten Angriffsfläche: verborgene Assets, IT-, OT-, IoT- und Cloud-Assets sowie Identitäten und Anwendungen.
Machen Sie sich ein Bild von der Zugänglichkeit für Angreifer durch die Visualisierungen von bereichsübergreifenden Beziehungen, sodass Sie die gefährlichsten Angriffspfade blockieren können.
Fokussieren Sie Ihre Maßnahmen auf das, was wirklich wichtig ist: die kritischen Sicherheitslücken, bei denen die Wahrscheinlichkeit eines Angriffs am größten ist.
Beschleunigen Sie die Reaktion mit automatisierten Workflows und konkreten Handlungsempfehlungen, die Behebungsmaßnahmen vereinfachen.
Optimieren Sie die Messung und Kommunikation der Cyber Exposure– mit business-orientierten Ansichten, die Ihnen zu besseren Entscheidungen und Investitionen verhelfen.
Machen Sie sich die umfassendste Wissensdatenbank für Bedrohungen und Schwachstellen zunutze, die Erkenntnisse von Tenable Research, der National Vulnerability Database (NVD) und vertrauenswürdigen Drittquellen umfasst.
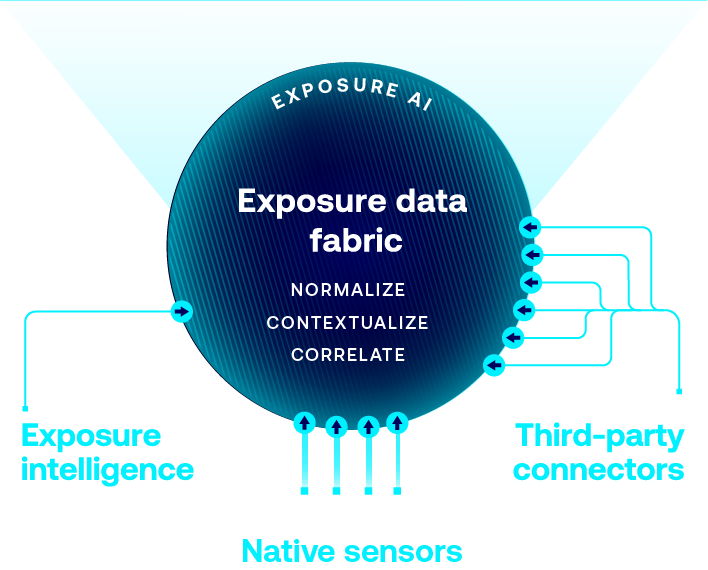
Native Erkennung von Angriffsflächen für Cloud, Identitäten, IT, IoT, OT, Anwendungen, Container, Kubernetes usw., die von Tenable-Produktsensoren unterstützt wird.
Verknüpfen Sie nahtlos Asset- und Exposure-Daten aus Ihren bestehenden Tools, um Tenable Intelligence zu ergänzen und umfassenden Exposure-Kontext zu liefern.
Nutzen Sie das weltweit größte Repository für Asset-, Exposure- und Bedrohungskontext, aus dem ExposureAI unübertroffene Erkenntnisse gewinnt.
Organisieren Sie Daten, um Redundanz zu reduzieren und Integrität, Konsistenz und Effizienz zu verbessern.
Reichern Sie die Daten mit zusätzlichen Informationen an, damit sie aussagekräftiger und handlungsrelevanter werden.
Identifizieren Sie wichtigen Beziehungskontext zu grundlegenden Unternehmensservices und -funktionen und zeigen Sie ihn auf.
Erste Schritte mit Tenable One
Tenable One hat unseren Engineers geholfen, den Zeitaufwand für manuelle Aufgaben um 75 % zu reduzieren, sodass sie sich auf die eigentliche Engineering-Arbeit konzentrieren können.
- Tenable Attack Surface Management
- Tenable Cloud Security
- Tenable Enclave Security
- Tenable Identity Exposure
- Tenable Nessus
- Tenable One
- Tenable OT Security
- Tenable Patch Management
- Tenable Security Center
- Tenable Vulnerability Management
- Tenable Web App Scanning







