In LockerGoga’s Aftermath: 3 Guiding Principles for Your OT Security Defense Strategy
Automatically finding relevant assets can empower you to apply patches so you can remediate vulnerabilities within your attack surface before attackers can exploit them.
In 2019, LockerGoga took a major aluminum producer’s operations offline — that much we know. But many people don’t know that LockerGoga has a common thread with Triton, Shamoon, Petya and other attacks that inflict damage to critical infrastructure and industrial operations around the globe.
When these attacks happen — whether to your organization or others — it’s always a good idea to conduct a post-mortem analysis to learn from the attack and help secure your operation from future attacks.
Here are three key takeaways to help strengthen your defense strategy:
1. Security today makes a more secure tomorrow
The commonality between LockerGoga and other attacks? There were multiple occurrences of each in the wild.
For example, LockerGoga was first detected in January 2019, yet in March it made a second appearance when it shut down an aluminum producer, which had to move to manual operations. LockerGoga made an additional appearance in April 2019.
Shamoon appeared as early as 2012 and reappeared again in 2016 and 2017.
Similarly, Triton made its debut in 2017. We saw it again in 2018 and then again in early 2019.
Attackers are recycling these exploit tools, so there’s a good probability that whatever resource you use to secure your organization the first time will help avoid revisiting them over and over.
2. Basic maintenance is generally not happening in your OT environment
Industrial organizations have experienced quantum paradigm shifts in the last five years, which makes them more attractive and easier to successfully attack.
Whereas industrial processes and operational technology (OT) networks were once isolated, today they are not. Thanks to the digital convergence of IT and OT environments and the implementation of industrial internet of things (IIoT) technology, OT is no longer an unreachable island. In fact, OT is a relatively easy target compared to traditional IT environments, which have a 20-year security head start.
To keep attacks from repeating, your organization must keep an up-to-date inventory of assets on your OT network. Some refer to this as “basic maintenance,” yet it is anything but basic.
To truly stop the return of named attacks we thought were in our rear-view mirror, it is not enough to just keep a spreadsheet or other offline asset list. These static lists are generally outdated the minute you create them.
In today’s dynamic OT environments, you need an automatically updated, live list with a detailed inventory of what is in your network.
Without this live and detailed information, your organization can easily miss critical elements in your network you need to patch. The result is that vulnerabilities remain overlooked because your security administrator does not know they are there.
With enough reconnaissance, hackers can quickly find these holes and take advantage of them by recycling old attacks that still have the capacity to devastate industrial operations.
3. Automate and alleviate mundane tasks to focus on what matters
In the past, we relied on human intelligence to find security incidents within mountains of data. This is frequently a laborious, time-consuming set of tasks.
In addition, this process is also subject to human error, which adds another barrier to breach resolution. Automatically finding relevant assets will empower you to apply patches to secure vulnerabilities before attackers exploit them and thereby help you eliminate encore attack performances that take down OT networks.
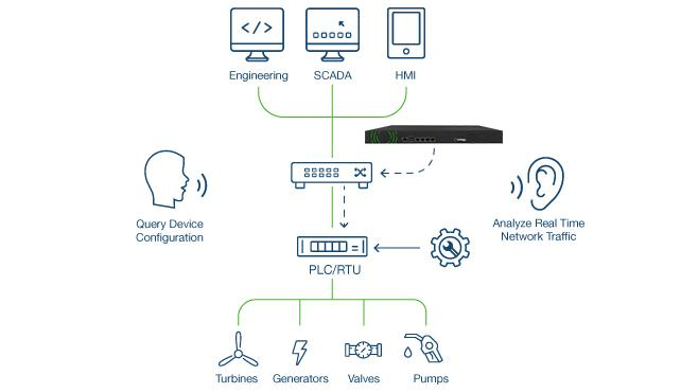
Deploying a robust patch management program also automates tedious tasks, which eliminates human error.
With a real-time and detailed asset inventory program, you can prioritize your top threats and take more efficient actions to defend your network.
Learn more
Tenable.ot can help you automate assets discovery, prioritize threats and defend your OT network. Visit https://www.tenable.com/products/tenable-ot
- SCADA


