The Buy Vs. Build Dilemma: Pitfalls of the DIY Approach to Exposure Management

Some security teams are taking a do-it-yourself approach to exposure management, according to a recent study conducted by Enterprise Strategy Group, now part of Omdia, in partnership with Tenable. But are they really ready for the hidden costs and challenges that come with a homegrown system?
Key takeaways
- Organizations are managing as many as 25 different security tools and struggling to make sense of all the alerts and data.
- Some teams are turning to homegrown data security lakes and data fabrics to stitch together the output from all these tools.
- DIY solutions introduce hidden costs and risks and place burdens on security teams, distracting them from their main mission: reducing cyber risk.
How do you manage the cacophony of alerts and floods of data coming at you from your various siloed security tools? If you’re like most security leaders, you probably figure the best option is to just handle it yourself. After all, who else knows your infrastructure like you do? You’ve invested time and resources in deploying the security tools that best serve your needs and choosing the right teams to manage them.
And, let’s face it, do-it-yourself (DIY) projects can be fun…until they’re not.
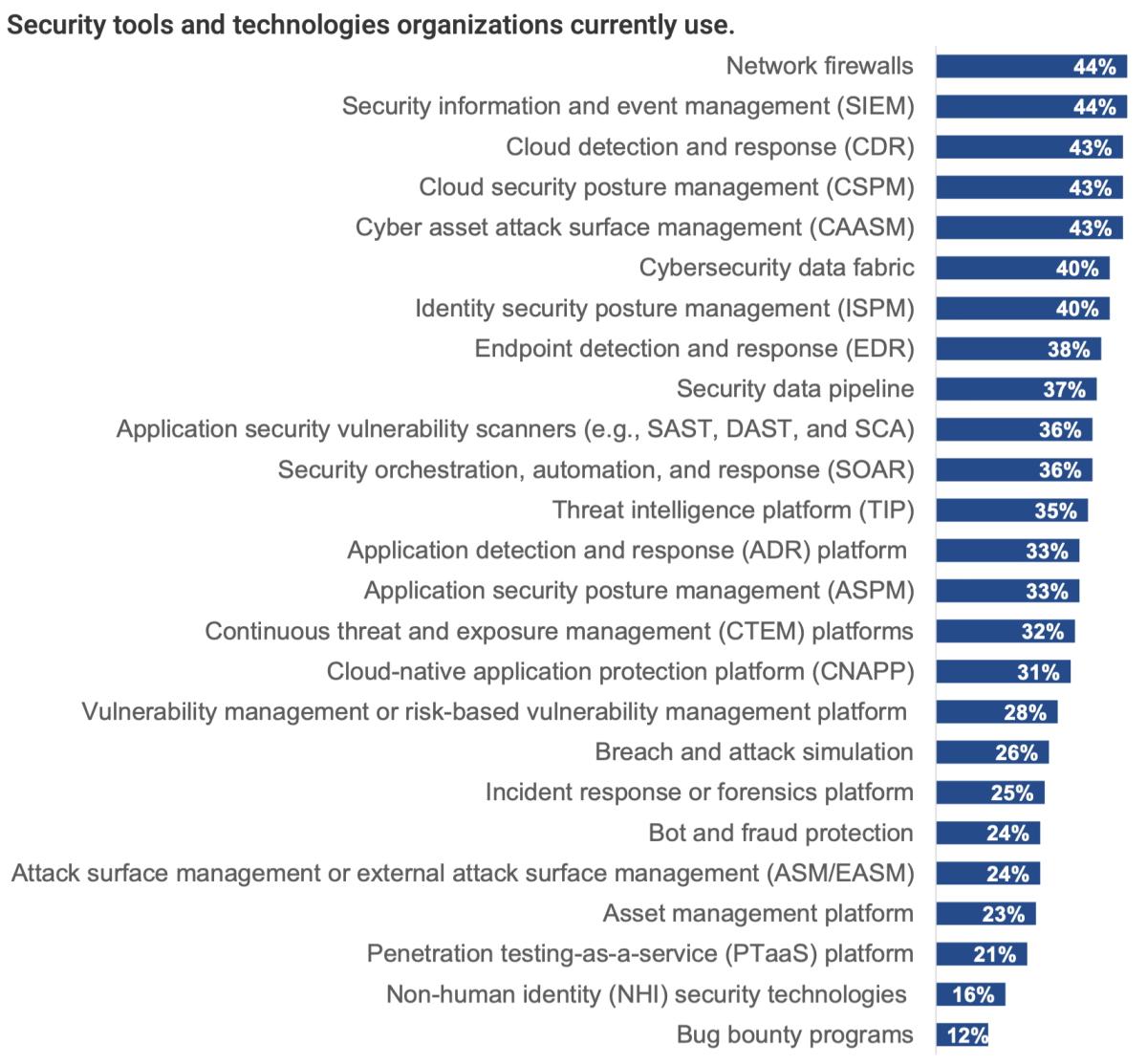
A study conducted by Enterprise Strategy Group, now part of Omdia, in partnership with Tenable, reveals that organizations are managing as many as 25 different security tools, each with its own unique way of presenting findings. Among these tools are:
- Cloud security posture management (CSPM)
- Cyber asset attack surface management (CAASM)
- Identity security posture management (ISPM)
- Endpoint detection and response (EDR)
- Application security vulnerability scanners (e.g., SAST, DAST, and SCA)
Nearly two-thirds of organizations (63%) are currently using or in the process of implementing their own security data lakes or security fabric to make sense of the output from all these siloed security tools. Another third (34%) are in the process of evaluating or planning an implementation in the next 12 months.
While it may be tempting to build rather than buy, there are numerous pitfalls in this approach. “Building these custom data lakes is a significant undertaking,” wrote Tenable CSO Robert Huber in the blog How Tenable Moved from Siloed Security to Exposure Management. “It often starts with seemingly ‘free’ solutions, only to quickly escalate into substantial investments in infrastructure, expertise, and countless integrations and workflows.”
Pulling all your data together is just the first step. You have to normalize, deduplicate, enrich and continuously analyze that data in order to have an accurate assessment of your risk. These are just some of the challenges we see in homegrown solutions:
- Lack of consistency
- Data quality problems
- A lack of data deduplication and normalization
- High storage and computing costs
- Skills and knowledge gaps in your teams
- Infrequent exposure assessments, leading to increased risk
- Inability to gather meaningful and actionable intelligence
- Inefficient workflows and prioritization
Building a DIY data lake requires you to employ dedicated cyber data analysts, an inefficient use of scarce cyber resources. “These individuals should be solving cyber problems, not spending their time on data analytics that should be provided by vendors,” wrote Huber.
Analysis isn’t happening often enough
Despite all the effort, many DIY approaches still rely on point-in-time assessments. Pulling together reports, stitching dashboards from multiple sources, and trying to normalize and enrich all that data is time-consuming and complex. As a result, organizations often end up relying on infrequent snapshots that quickly become outdated, leaving critical blind spots. Meanwhile, attackers have a continuous, real-time view of your environment — the less frequent your analysis, the greater the advantage you’re giving them.
Continuous assessment is the only way to truly reduce risk, prioritize remediation effectively and stay ahead of evolving threats.
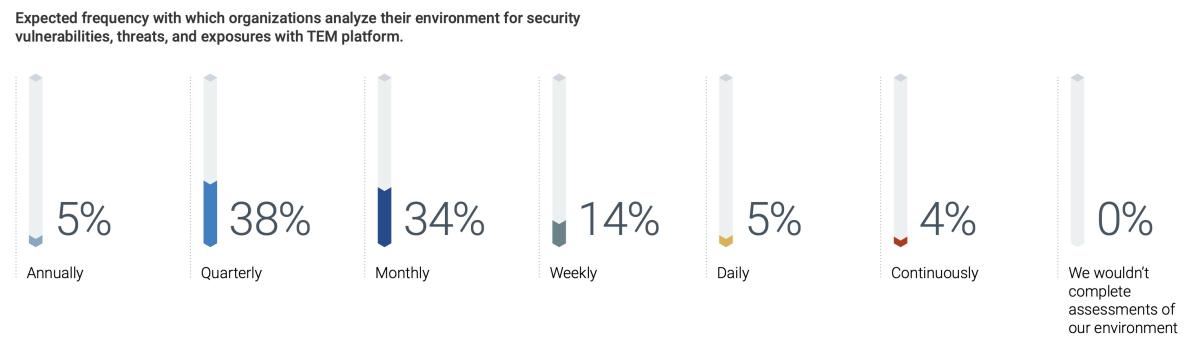
The problem lies in the misconceptions organizations still have about the benefits they will gain from using a modern platform. Many teams assume that even with a threat and exposure management (TEM) platform, updates will still be infrequent — monthly or quarterly at best. In fact, our study finds that only 14% of organizations expect to conduct weekly exposure assessments and even fewer expect to achieve continuous monitoring with a platform.
The reality is very different. Modern TEM platforms, like Tenable One, deliver continuous, real-time analysis across all assets, risks and data sources. Only a TEM platform can close the visibility gap, turning reactive security into proactive defense and giving teams the insight they need to stay ahead of evolving threats.
How an exposure management platform outperforms the DIY approach
Managing risk with DIY tools is complex, time-consuming and often leaves dangerous blind spots in your protection. The Tenable One Exposure Management Platform provides a unified, continuous and contextual approach to exposure management, helping organizations stay ahead of threats and make informed, actionable decisions.
- Unified visibility: Ingest data from all your existing security tools — including cloud security, vulnerability management, application scanners, identity management, endpoint detection and more — into a single view to eliminate blind spots.
- Contextual prioritization: Gain context-rich, actionable insights that highlight the risks that matter most to your specific business, enabling your teams to focus on what truly reduces exposure.
- Continuous assessment: Monitor your environment in real time to stay ahead of attackers and address vulnerabilities before they can be exploited.
- Executive-ready reporting: Access unified dashboards and reports that track business risk, analyze trends and share progress with leadership and the board.
- Lower operational costs: Avoid the high storage and computing expenses of running your own data lake or fabric and eliminate the need to dedicate resources to managing infrastructure, integrations and workflows.
Tenable One empowers organizations to move beyond fragmented, point-in-time assessments and achieve continuous, proactive exposure management that drives real risk reduction.
Learn more
- Read the Enterprise Strategy Group report, “The Evolution of Risk Reduction: Contextual Analysis and Automated Remediation in Threat and Exposure Management”
- Check out the Exposure Management Resource Center
- Visit the Exposure Management Academy
- Learn more about Tenable One
- Exposure Management
- Research Reports



