Exposure Management: Cyberrisiken stets einen Schritt voraus sein
Die Bedeutung von Exposure Management beim Aufbau von Cybersecurity-Programmen
Exposure Management bietet einen umfassenden Überblick über Ihre moderne Angriffsfläche, sodass Sie das Cyberrisiko Ihres Unternehmens besser nachvollziehen und fundiertere Geschäftsentscheidungen treffen können. Wenn Ihre IT- und Sicherheitsteams wissen, wie Ihre Angriffsfläche aussieht und wo die größten Risiken bestehen, können sie Schwachstellen und andere Sicherheitslücken aus technischer wie auch geschäftlicher Perspektive effektiver entschärfen.
In dieser Informationssammlung betrachten wir genauer, was unter Exposure Management zu verstehen ist, welche Rolle risikobasiertes Schwachstellenmanagement spielt und wie Exposure Management Ihr Unternehmen vor Cyberangriffen schützt.
Erfahren Sie mehr über diese Themen:
7 Vorteile einer Exposure Management-Plattform
Eine umfassende Exposure Management-Plattform kann Ihnen die notwendige Sichtbarkeit zur Reduzierung von Cyberrisiken bieten – ohne gänzlich verschiedene Tools, die kritische Sicherheitsdaten in Silos speichern.
Mehr erfahrenSichtbarkeit erzielen, Angriffe verhindern, Risiken kommunizieren
Wie prädiktiver Bedrohungskontext und objektive Metriken zur Verhinderung von Cyberangriffen beitragen.
Mehr erfahrenExposure Management – FAQ
Sie haben Fragen zum Thema Exposure Management? Sehen Sie sich unsere FAQs an.
Mehr erfahrenAufbau eines Exposure Management-Programms
In fünf Schritten sind Sie auf dem besten Weg, ein Exposure Management-Programm aufzubauen.
Mehr erfahrenSchließen Sie sich der Exposure Management-Community an
Tauschen Sie sich mit anderen Experten aus, die mehr über Exposure Management erfahren möchten.
Mehr erfahrenVorteile von Exposure Management
Machen Sie sich mit einigen der vielen Vorteile einer Exposure Management-Strategie vertraut.
Mehr erfahrenAuswahl einer Exposure Management-Lösung
Hier finden Sie einige Aspekte, auf die Sie bei der Auswahl einer Exposure Management-Lösung achten sollten.
Mehr erfahrenAntizipieren Sie Angriffe. Reduzieren Sie Risiken proaktiv.
Tenable One ist die einzige Exposure Management-Plattform, die Sie für einen einheitlichen Blick auf Ihre moderne Angriffsfläche benötigen. Mit Tenable One sind Sie in der Lage, die Folgen von Cyberangriffen vorherzusehen und Cyberrisiken für all Ihre Assets in sämtlichen Bereichen auf proaktive Weise anzugehen und zu managen.
Exposure Management: Aktuelle Erkenntnisse
Cyber Exposure-Studie von Tenable: Abwehr von Ransomware
Bedrohungsakteure setzen auf die Wahrscheinlichkeit, dass Ihr Unternehmen gängige und bekannte Software-Schwachstellen nicht behoben hat. Diese Sicherheitslücken möchten sie ausnutzen, um Ihre Systeme zu infiltrieren – häufig mit der böswilligen Absicht, Ihre Assets mit Ransomware zu infizieren.
Viele Ransomware-Infektionen sind auf diese Schwachstellen und auf einen Bereich zurückzuführen, den Sicherheitsteams häufig übersehen – Ihr Active Directory (AD).
Wenn es Angreifern gelingt, nur eine einzige Sicherheitslücke in Active Directory erfolgreich auszunutzen, können sie ihre Rechte mühelos ausweiten. Und sollte es in Ihrem Unternehmen an Cyberhygiene mangeln, stehen die Chancen gut, dass Angreifer auf Ihrer Angriffsfläche ohne Weiteres Fuß fassen und Ransomware verteilen werden.
Was können Sie also tun?In dieser Studie von Tenable erfahren Sie mehr über folgende Themen:
- Am häufigsten genutzte Angriffsvektoren und Exploits
- Wie sich Behebungsmaßnahmen priorisieren lassen, um sich auf Schwachstellen zu konzentrieren, von denen die größte Bedrohung für Ihr Unternehmen ausgeht
- Wie Tenable One Ihnen helfen kann, Schwachstellen in Active Directory (AD) und andere Sicherheitslücken zu identifizieren
Gartner Report: „How to Grow Vulnerability Management into Exposure Management”
Wenn eine endlose Liste mit Schwachstellen priorisiert wird, die allesamt einen „kritischen“ oder „hohen“ Schweregrad aufweisen, bleibt eine handlungsorientierte Lösung für Ihr Cyber Exposure-Problem für immer unerreichbar – insbesondere dann, wenn Sie weiterhin klassische Tools für die Bewertung von Schwachstellen und herkömmliche Verfahren für das Schwachstellenmanagement einsetzen.
Fakt ist, dass die aktuellen Ansätze für Attack Surface Management (ASM) mit den gewaltigen und komplexen Umgebungen der heutigen Zeit einfach nicht Schritt halten können. Hierzu ist eine Umstellung auf risikobasiertes Schwachstellenmanagement notwendig.
Dieser CTEM-Ansatz (Continuous Threat Exposure Management) geht über eine reine Bewertung von Cyberrisiken hinaus. Ausgereifte Schwachstellenmanagement-Programme sollten Ihnen außerdem ein Verständnis von Cyberbedrohungen im jeweiligen Geschäftskontext vermitteln, was für Exposure Management und Ihre Priorisierungs- und Behebungsstrategien von entscheidender Bedeutung ist.
Aus diesem Gartner-Bericht zum Thema Vulnerability Management geht im Detail hervor, wie Sie Ihr Schwachstellenmanagement-Programm zu einem Exposure Management-Programm weiterentwickeln können. Lesen Sie weiter und erfahren Sie, wie Sie:
- Den Umfang und die Frequenz von Schwachstellenbewertungen festlegen
- Die Asset-Erfassung ausweiten, um die Cloud und digitale Assets einzubeziehen
- Den Fokus mithilfe von Priorisierungs- und Validierungsstrategien auf Sicherheitslücken richten, die Bedrohungsakteure aktiv ausnutzen
- Risikomanagementprozesse in bestehende Workflows einbinden und teamübergreifende Zusammenarbeit verbessern
Wie Menschen, Prozesse und Technologien Cybersecurity-Teams Probleme bereiten
Tenable hat Forrester mit der Durchführung einer Studie beauftragt, in deren Rahmen über 800 IT- und Cybersecurity-Experten dazu befragt wurden, wie Herausforderungen im Zusammenhang mit Mitarbeitern, Prozessen und Technologien ihre Risikominderungsstrategien beeinträchtigen.
Der Bericht unterstreicht, warum es für Unternehmen unerlässlich ist, von reaktiver Sicherheit auf präventive Sicherheit umzustellen.
Einige der wichtigsten Ergebnisse:
- Ein durchschnittliches Unternehmen hat in den vergangenen zwei Jahren weniger als 60 % der Cyberangriffe präventiv abgewehrt.
- Mehr als die Hälfte der IT- und Sicherheitsverantwortlichen geben an, dass Cloud-Infrastruktur das größte Cyberrisiko in ihrem Unternehmen darstellt.
- Sechs von zehn Cybersecurity- und IT-Profis geben an, dass Sicherheitsteams zu sehr mit der Bekämpfung kritischer Vorfälle beschäftigt sind, um einen präventiven Ansatz zur Verringerung der Exposure zu verfolgen.
Im Bericht erfahren Sie mehr zu folgenden Themen:
- Die am häufigsten genutzten Cybersecurity-Tools
- Der Bedarf an mehr Cybersecurity-Ressourcen
- Die Komplexitäten von Public Cloud-, Private Cloud-, Multi-Cloud- und Hybrid Cloud-Sicherheit
Fünf Schritte zur Priorisierung der tatsächlichen geschäftlichen Exposure
Für Angreifer spielen betriebliche Silos keine Rolle. Vielmehr hoffen sie darauf, dass zwischen Ihren IT- und Sicherheitsteams eine Kluft besteht. Isolierte Sicherheit ist eine natürliche Konsequenz der rapide zunehmenden Nutzung von Technologie – insbesondere wenn Ihre Teams immer mehr OT-, IoT- und Cloud-Assets in Ihre Workflows einbinden.
Parallel zu diesem Wachstum wird die Branche mit einer Flut an gänzlich verschiedenen Schwachstellenmanagement-Tools überschwemmt, die jeweils nur für einen spezifischen Teilbereich Ihrer gesamten Angriffsfläche ausgelegt sind. Nur wenige davon werden als umfassende All-in-One-Sicherheitslösung betrieben. Dies führt zu verschiedenartigen Daten, unvollständiger Sichtbarkeit und blinden Flecken, die Angreifer nur allzu gern noch vor Ihnen finden würden.
Bedrohungsakteure werden Ihre Sicherheitsschwächen ausfindig machen und dann ausnutzen, um sich seitwärts (und häufig unbemerkt) durch Ihr Netzwerk fortzubewegen.
In diesem E-Book erfahren Sie mehr darüber, wie Sicherheit auf Ihrer gesamten Angriffsfläche vereinheitlicht werden kann. Folgende Themen werden unter anderem behandelt:
- Lehren aus früheren Sicherheitsverletzungen
- Häufig auftretende Exposure Management-Hindernisse
- Fünf Methoden, mit denen Sie Ihre Strategien zur Schwachstellenpriorisierung optimieren können, um Sicherheitsverletzungen zu verhindern
Tenable Connect-Community: Ihre zentrale Anlaufstelle für Exposure Management
Treten Sie der Tenable Connect-Community bei und tauschen Sie sich mit anderen aus, die ähnliche Interessen haben und mehr darüber erfahren möchten, wie Exposure Management funktioniert oder wie vorhandene risikobasierte Schwachstellenmanagement-Programme optimiert werden können, um zu einer effektiveren Exposure Management-Strategie überzugehen.
Willkommen beim Tenable One Deployment Guide
Tenable One ist eine Exposure Management-Plattform, mit deren Hilfe Unternehmen Sichtbarkeit auf ihrer gesamten modernen Angriffsfläche erzielen, Maßnahmen zur Verhinderung von wahrscheinlichen Angriffen fokussieren und Cyberrisiken präzise kommunizieren können, um eine optimale Unternehmensleistung zu unterstützen.
WeiterlesenSchnelle Tipps für effektive Exposure Response
In der schnelllebigen digitalen Landschaft von heute ist Schwachstellenmanagement von entscheidender Bedeutung, doch mit der Identifizierung von Schwachstellen ist es nicht getan: Für ein effektives Schwachstellenmanagement müssen Risiken mithilfe von Maßnahmen priorisiert und beseitigt werden, die Verbesserungen der Sicherheit vorantreiben und schwerwiegenden Sicherheitslücken vorbeugen.
WeiterlesenHybrid Cloud Security mit Tenable One
Tenable Cloud Security steht nicht einfach nur für Cloud-Sicherheit. Die Lösung ist Teil des größeren Tenable-Ökosystems für Exposure Management – und das kann einen gewaltigen Unterschied ausmachen. Risiken treten nicht in Isolation auf und Angreifer agieren systemübergreifend. In der Lage zu sein, Lösungen eines Anbieters für Infrastrukturen verschiedenster Art (On-Prem, Cloud, OT usw.) einzusetzen, um potenzielle Angriffswege zu erkennen, ist daher von entscheidender Bedeutung.
Jetzt ansehenHäufig gestellte Fragen zu Exposure Management
Exposure Management ist für Sie ein neues Konzept? Sie haben Fragen, wissen aber nicht, wo Sie anfangen sollen? Diese FAQs zum Thema Cyber Exposure Management sind ein guter Ausgangspunkt.
Was ist Exposure Management?
Was wird mit Exposure Management erreicht?
Wie kann Exposure Management den Reifegrad meines Cybersecurity-Programms erhöhen?
Warum benötige ich Exposure Management?
Wie lauten die zentralen Rollen in einem Exposure Management-Programm?
Wie kann ich mit Exposure Management beginnen?
- Machen Sie sich ein Bild von der Sicherheit all Ihrer Assets und identifizieren Sie Sicherheitslücken.
- Betrachten Sie Ihre gesamte Angriffsfläche aus der Perspektive eines Angreifers.
- Priorisieren Sie Behebungsmaßnahmen anhand des tatsächlichen Unternehmensrisikos (nicht anhand willkürlicher CVSS-Bewertungen).
- Messen Sie Ihre Behebungsprozesse anhand kontinuierlicher Verbesserungen.
- Kommunizieren Sie Risiken effektiv und ergreifen Sie Maßnahmen zur Absicherung Ihrer Angriffsfläche.
Welche Vorteile bietet Exposure Management?
- Umfassender Einblick in Ihre moderne Angriffsfläche
- Übergang von reaktiver Sicherheit zu einer Antizipation der Folgen von Cyberangriffen
- Kontextualisierte Sicherheitsdaten zur Priorisierung von Behebungsmaßnahmen
- Effektivere Kommunikation im gesamten Unternehmen – bis hinauf zur Geschäftsleitungs- und Vorstandsebene
Welche Schritte kann ich ergreifen, um Cyberrisiken einen Schritt voraus zu sein?
Wie trägt Exposure Management dazu bei, bessere Geschäftsentscheidungen zu treffen?
Wie kann ich Cyber Exposure proaktiv reduzieren?
Worauf sollte ich bei einer Exposure Management-Plattform achten?
- es einfach macht, alle Assets in sämtlichen Bereichen auf einer einzigen Plattform einzusehen
- Ihnen hilft, Sicherheitsdaten zu verstehen, und Threat-Intelligence bietet – unterstützt durch KI und ML, sodass Sie Bedrohungen antizipieren und Behebungsmaßnahmen priorisieren können
- Sie dabei unterstützt, Cyberrisiken effektiv zu kommunizieren, um bessere Sicherheits- und Geschäftsentscheidungen zu treffen
Was kann ich durch Exposure Management lernen?
- Wie sicher sind wir?
- Wo sollen wir unsere Prioritäten setzen?
- Wie reduzieren wir unsere Gefährdung im Laufe der Zeit?
- Wo stehen wir im Vergleich?
Lassen sich Angriffspfade durch Exposure Management versperren?
Warum ist Asset-Inventarisierung für Exposure Management wichtig?
Aufbau eines Exposure Management-Programms
Die Umstellung auf einen risikobasierten Ansatz kann Ihrem Unternehmen helfen, den Reifegrad Ihres Schwachstellenmanagement-Programms zu erhöhen. Doch heutzutage stellt sich die Frage: Reicht das aus?
Die Antwort lautet: wahrscheinlich nicht.
Ein Exposure Management-Programm hingegen kann Ihnen helfen, Ihr Cybersecurity-Programm von einem reaktiven, auf Incident Response ausgerichteten Ansatz zu einem proaktiven Ansatz weiterzuentwickeln, der Ihrem Team umfassende Einblicke in Ihre gesamte Angriffsfläche verschafft. So können Sie mit der sich ständig verändernden Bedrohungslage Schritt halten und deren Auswirkungen auf die spezifischen Anforderungen Ihres Unternehmens besser einschätzen.
Setzen Sie diese fünf Empfehlungen um, um sich ein besseres Verständnis aller vorhandenen Sicherheitslücken zu verschaffen, sodass Sie Cyberrisiken proaktiv reduzieren können:
-
Bewerten Sie Ihre derzeitigen Assets – On-Prem und in der Cloud (IT, OT, IoT, Web-Apps usw.).
Fragen Sie sich: Greifen unsere Technologien ineinander, sodass sie uns einen umfassenden Einblick in alle unsere Sicherheitsschwächen bieten? Oder arbeiten sie immer noch isoliert voneinander?
-
Gehen Sie der Sichtbarkeit Ihrer Angriffsfläche auf den Grund.
Fragen Sie sich: Was können wir sehen? Was müssen wir sehen?
-
Priorisieren Sie Maßnahmen.
Fragen Sie sich: Was ist als Erstes zu tun? Wie können wir unsere Behebungsstrategien prädiktiver gestalten? Nutzen wir Threat-Intelligence? Können wir alle Angriffspfade analysieren, die zu unseren kritischsten Assets führen?
-
Messen Sie Ihre Behebungsprozesse.
Fragen Sie sich: Wie effektiv schließen wir aktuell die identifizierten Sicherheitslücken? Was können wir tun, um hier effektiver vorzugehen? Wie schneiden unsere Maßnahmen im Vergleich mit anderen Unternehmen der Branche ab?
-
Kommunizieren Sie und ergreifen Sie Maßnahmen.
Fragen Sie sich: Wie sicher sind wir? Können wir unseren Sicherheitsstatus gegenüber Führungskräften, wichtigen Stakeholdern und anderen Beteiligten effektiv kommunizieren? Wie nutzen wir Daten, um effektivere Geschäftsentscheidungen zu treffen?
Welche Exposure Management-Plattform ist für Ihr Unternehmen die richtige?
Die Suche nach einer zuverlässigen und effektiven Cybersecurity-Lösung ist seit jeher frustrierend und zeitaufwändig. Und nach der sorgfältigen Evaluierung und Implementierung einer Lösung kann es sich häufig als noch schwieriger erweisen, alle Beteiligten zur Nutzung der Lösung zu bewegen und von all ihren Vorteilen zu profitieren.
Der Grund dafür? Diese Lösungen sind traditionell wenig benutzerfreundlich oder sie liefern derart viele Daten, dass die zuständigen Teams nicht wissen, was sie mit all diesen Daten anfangen sollen.
Doch eine Exposure Management-Lösung auszuwählen und Ihre Teams von Ihrer Auswahl zu überzeugen, muss kein Kopfzerbrechen bereiten. Hier drei wichtige Lösungsmerkmale, auf die Sie achten sollten, um diesen Prozess zu vereinfachen:
-
Die Lösung macht es einfach, alle Assets in sämtlichen Bereichen auf einer einzigen Plattform einzusehen.
Und das sowohl On-Prem wie auch in der Cloud. Die Lösung sollte mehr können, als einfach nur Ihre Assets zu inventarisieren. Eine effektive Exposure Management-Lösung sollte auch Schwachstellen, Fehlkonfigurationen und sonstige Sicherheitsprobleme in Bezug auf Assets identifizieren können und kontinuierliches Monitoring ermöglichen, damit Sie jederzeit wissen, was vorhanden ist und wo Sicherheitslücken vorliegen könnten.
Suchen Sie nach einer Lösung, die Ihnen eine einheitliche Ansicht Ihrer gesamten modernen Angriffsfläche bietet, sodass Sie blinde Flecken beseitigen können und wissen, wie Sie vorgehen müssen, um Cyberrisiken effektiv zu managen.
-
Die Lösung hilft Ihnen, Daten zu verstehen, Bedrohungen zu antizipieren und Behebungsmaßnahmen zu priorisieren.
Suchen Sie nach einem Exposure Management-System, das Ihnen hilft, Threat-Intelligence und andere relevante Daten zu nutzen, um die Folgen eines Cyberangriffs zu antizipieren – ganz konkret für Ihr Unternehmen.
Suchen Sie nach einer Lösung, die Beziehungen zwischen Assets, Sicherheitslücken, Berechtigungen und Bedrohungen auf der gesamten Angriffsfläche aufzeigt und Ihnen helfen kann, Risikomanagement- und Behebungsmaßnahmen zu priorisieren. Die Lösung sollte außerdem in der Lage sein, kontinuierlich die Angriffspfade zu identifizieren, die mit dem größten Ausnutzungsrisiko verbunden sind – selbst bei rasanter Veränderung und Erweiterung Ihrer Angriffsfläche. Diese Funktionen erleichtern es Ihren Teams, Risiken proaktiv und mit geringstmöglichem Aufwand zu reduzieren und dadurch Angriffe zu verhindern.
-
Die Lösung sollte Ihnen helfen, Cyberrisiken effektiv zu kommunizieren, sodass Sie fundiertere Sicherheits- und Geschäftsentscheidungen treffen können.
Suchen Sie nach einer Exposure Management-Lösung, die eine zentralisierte und geschäftsbezogene Ansicht Ihrer Sicherheitslücken bietet – zusammen mit Fortschrittsmessungen im Zeitverlauf anhand klarer KPIs.
Die Lösung sollte zudem Einblicke bieten, die über einen allgemeinen Überblick hinausgehen, sodass Sie Detailinformationen auf Ebene von Assets, Abteilungen oder Betriebseinheiten aufschlüsseln können. Darüber hinaus sollte die Lösung Benchmarking-Funktionen beinhalten, sodass Sie nachvollziehen können, wie gut Ihr Programm im Vergleich mit anderen Unternehmen der Branche abschneidet.
Vorteile von Exposure Management
Im Kern geht es bei Exposure Management darum, ausgehend von reaktiven Sicherheitsmaßnahmen zu einer proaktiveren Strategie überzugehen, die vorhandene Sicherheitslücken reduziert. Durch die Einführung einer Exposure Management-Plattform ist Ihr Unternehmen besser darauf vorbereitet, wahrscheinliche Angriffe zu antizipieren und parallel dazu Risiken proaktiv zu reduzieren.
Hier einige Vorteile einer Exposure Management-Strategie:
Umfassende Sichtbarkeit erzielen
Mit einer einheitlichen Ansicht Ihrer Angriffsfläche können Sie im Handumdrehen all Ihre Assets in sämtlichen Bereichen identifizieren, damit verbundene Sicherheitsprobleme aufdecken und den zur Reduzierung von Risiken notwendigen Zeit- und Arbeitsaufwand reduzieren.
Folgen von Cyberangriffen antizipieren
Eine Exposure Management-Plattform kann Ihnen ein besseres Verständnis der Beziehungen zwischen Assets, Sicherheitslücken, Berechtigungen und Bedrohungen auf der gesamten Angriffsfläche vermitteln – On-Prem wie auch in der Cloud.
Maßnahmen priorisieren
Wenn Sie ausnutzbare Schwachstellen sowie Pfade für Angriffe und Sicherheitsverletzungen kontinuierlich identifizieren und im Blick behalten, können Sie Ihre Fähigkeiten zur Risikopriorisierung verbessern und profitieren von besseren Erkenntnissen für Behebungsmaßnahmen. Dadurch gelingt es Ihnen effektiver, Cyberbedrohungen zu reduzieren und Angriffe zu verhindern.
Effektivere Kommunikation
Ein Exposure Management-Programm bietet Ihnen eine geschäftsbezogene Ansicht der vorhandenen Sicherheitslücken. Dadurch können Sie effektiver mit wichtigen Stakeholdern kommunizieren – abgestimmt auf die jeweiligen geschäftlichen Ziele und Vorgaben.
Erleben Sie Tenable One in Aktion
Tenable One vereint risikobasiertes Schwachstellenmanagement, Web-App-Scanning, Cloud-Sicherheit und Identitätssicherheit in einer einzigen Exposure Management-Plattform. Auf diese Weise gewinnen Sie einen einheitlichen Einblick in Ihre gesamten Angriffsfläche, sodass Sie Risiken für all Ihre Assets proaktiv angehen und managen können.
Blog-Artikel zum Thema Exposure Management
Exposure Management: Risikoreduzierung auf der modernen Angriffsfläche
Viele Sicherheitsteams verharren im Reaktionsmodus – oftmals weil ihre Programme isoliert sind und sie Unmengen von Tools einsetzen, die derart viele Daten generieren, dass Teams nicht wissen, was sie damit anfangen sollen oder worauf Sie sich zuerst konzentrieren müssen.
Dieser Blog befasst sich damit, wie Exposure Management Ihnen die nötige Transparenz verschaffen kann, um Bedrohungen besser vorhersehen, Maßnahmen priorisieren und Risiken reduzieren zu können. Lesen Sie weiter und informieren Sie sich, wie Sie mit einer Exposure Management-Plattform Daten aus Ihren verschiedenen Assessment-Tools und Kontrollmechanismen zusammenführen können, um Abhängigkeiten klar zu erkennen. Auf diese Weise können Sie effektiver nachvollziehen, wo Sie tatsächlich Angriffen ausgesetzt sind und welche potenziellen Auswirkungen diese haben können.

Exposure Management: 7 Vorzüge eines Plattform-Ansatzes
Bisher haben die meisten Sicherheitsfachkräfte eine Vielzahl gänzlicher verschiedener Tools eingesetzt, die jeweils nur für einen spezifischen Teilaspekt der Angriffsfläche konzipiert wurden – beispielsweise ein Tool für Informationstechnologie (IT), ein weiteres für operative Technologie (OT) und ein drittes für die Cloud. Doch ist dies der effektivste Ansatz? Da diese Tools Daten häufig in Silos auf proprietären Plattformen speichern, ist es unmöglich, sich einen umfassenden Überblick über sämtliche Assets und Schwachstellen innerhalb Ihrer weitläufigen Umgebung zu verschaffen.
In diesem Blog-Artikel geht es um die Frage, was effektiver ist – diese Tools oder eine konsolidierte Lösung? Informieren Sie sich im Detail über die jeweiligen Vor- und Nachteile und finden Sie heraus, aus welchen sieben Gründen Sie erwägen sollten, diese Einzellösungen durch eine umfassende Exposure Management-Plattform zu ersetzen.

Effektivere Penetrationstests mithilfe von Exposure Management
Wie können Sie den Nutzen von Penetrationstests maximieren und sie effektiver gestalten? Dieser Blog-Beitrag beleuchtet, wie eine Exposure Management-Strategie Ihre Penetrationstests optimieren kann, um so eine Verbesserung Ihrer Cybersecurity-Lage zu bewirken. Mit einer Exposure Management-Plattform ist es beispielsweise möglich, regelmäßige Schwachstellen-Scans durchzuführen, anstatt die Ergebnisse von Penetrationstests abzuwarten.
In diesem Blog-Artikel erfahren Sie mehr über die Vorteile von Exposure Management und finden heraus, wie Sie alle Ihre Assets sowie damit verbundene Schwachstellen erfassen und Penetrationstests gezielt auf die Identifizierung von blinden Flecken fokussieren können. Auf diese Weise können Sie Ihre Abwehrmaßnahmen verstärken, bevor Bedrohungsakteure vorhandene Sicherheitslücken ausnutzen.

So schützen Sie Ihre IT-, OT- und IoT-Assets mit einer Exposure Management-Plattform
In konvergenten IT/OT-Umgebungen sind Sichtbarkeitslücken keine Seltenheit. Der Grund dafür ist, dass herkömmliche IT-Sicherheitstools Schwachstellen in OT-Umgebungen übersehen können. OT-Sicherheitstools hingegen lassen unter Umständen abhängige IT-Assets außer Acht.
Dieser Blog-Artikel behandelt die mit Sichtbarkeitslücken in OT-Umgebungen verbundenen Konsequenzen, z. B. bezogen auf Identitäten, wodurch sich erhöhte Geschäfts- und Cyberrisiken ergeben. Dies birgt ein besonders hohes Risiko für potenzielle Ausfallzeiten und Störungen, was Umsatzeinbußen oder unsichere Arbeitsbedingung zur Folge haben und im schlimmsten Fall sogar Menschenleben kosten könnte. Informieren Sie sich in diesem Blogbeitrag über den ganzheitlichen Mehrwert, den Ihnen eine Exposure Management-Plattform innerhalb Ihrer konvergenten IT/OT-Angriffsfläche bietet.

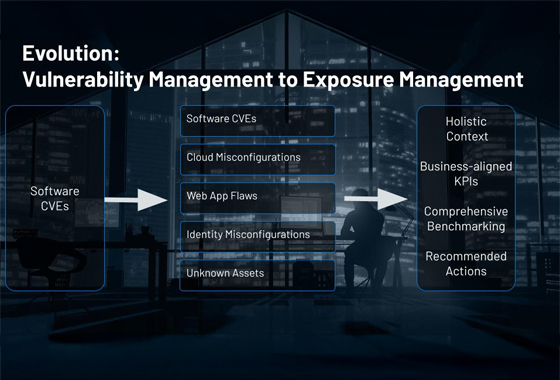
Kontext ist das A und O: Von Vulnerability Management zu Exposure Management
Ein Vulnerability Management-Programm ist für proaktive Cybersecurity-Strategien von entscheidender Bedeutung. Doch die meisten Unternehmen werden mit Unmengen von Schwachstellendaten überhäuft, die nur wenig Kontext zu den tatsächlichen Geschäftsrisiken beinhalten. Ohne diese Kontextinformationen sind Sie nicht in der Lage, hochriskante Sicherheitslücken auf der gesamten Angriffsfläche effektiv zu priorisieren.
Dieser Blog-Artikel behandelt den übergeordneten Nutzen, den eine Exposure Management-Strategie im Hinblick auf die Bewältigung gängiger Herausforderungen bietet, wie beispielsweise eine Überlastung durch Schwachstellen und langsame Reaktionszeiten bei der Behebung. In diesem Blog erfahren Sie, wie Sie vom klassischen Schwachstellenmanagement zu einem ganzheitlichen Exposure-Management-Ansatz übergehen können – mit Fokus auf Asset-Kontext, Identitäten und Bedrohungslage.

Mögliche Angriffspfade abbilden und versperren, bevor es zu Angriffen kommt
Hybride Angriffspfade können ohne Weiteres durch mehrere Sicherheitsbereiche verlaufen. Wenn Sie hier Einzellösungen verwenden, kann dies zur Folge haben, dass diese Angriffspfade übersehen werden. Bedrohungsakteure hoffen darauf, dass es dazu kommt. Sie sind darauf aus, Ihre Versäumnisse auszunutzen, um sich dann seitwärts und unerkannt durch Ihre Netzwerke fortzubewegen.
In diesem Blog-Artikel gehen wir näher auf die Lehren aus realen Angriffen ein und befassen uns mit der Frage, wie Einzeltools die Sichtbarkeit einschränken, die zur Bewertung und Behebung von Sicherheitslücken auf Ihrer gesamten Angriffsfläche notwendig ist. Informieren Sie sich in diesem Blogbeitrag über jüngste aufsehenerregende Angriffe und finden heraus, wie eine Exposure Management-Strategie Ihren Sicherheitsteams helfen kann, bessere Sicherheitsergebnisse zu erzielen.
Exposure Management – On-Demand-Webinare
Ihre Angriffsfläche aus der Angreiferperspektive
Wenn Ihre Sicherheitsteams wie Angreifer denken, sind sie besser in der Lage, die Angriffsfläche Ihres Unternehmens proaktiv abzusichern.
Dieses On-Demand-Webinar geht der Frage nach, warum eine umfassende Erfassung der Angriffsfläche für die meisten Sicherheitsteams eine Herausforderung darstellt. Sehen Sie sich das Webinar jetzt an, um sich ausführlicher über Folgendes zu informieren (auf Englisch):
- Wie Ihr Unternehmen aus der Angreiferperspektive aussieht
- Lehren aus drei Cyberangriffen, einschließlich Taktiken und Angriffsvektoren
- Wie Sie Ihre Priorisierungs- und Behebungsstrategien durch verstärkte teamübergreifende Zusammenarbeit verbessern können
Wie Menschen, Prozesse und Technologien Cybersecurity-Teams Probleme bereiten
Sicherheitsrelevante Branchenbestimmungen und behördliche Auflagen nehmen zu und werden immer komplexer. Dadurch wird es für Cybersecurity-Fachkräfte immer schwieriger, mit den sich verändernden Compliance-Anforderungen Schritt zu halten.
Dieses On-Demand-Webinar zeigt Möglichkeiten auf, wie Sicherheitsteams ihre Exposure Management-Verfahren optimieren können. Sehen Sie sich das Webinar jetzt an, um sich ausführlicher über Folgendes zu informieren (auf Englisch):
- Zentrale Silos in den Bereichen Betrieb und Technologie, die proaktiver Sicherheit im Wege stehen
- Maßnahmen, die Unternehmen mit hohem Reifegrad ergreifen, um ihre präventive Sicherheitsstrategie und Sicherheitskultur zu optimieren
- Empfehlungen, die Sie unabhängig vom derzeitigen Reifegrad Ihres Programms schnell umsetzen können
Die Cybersecurity-Bedrohungslandschaft: Wo stehen Sie derzeit?
Die moderne Angriffsfläche verändert sich ständig. Dadurch ist es schwierig, Komplexitäten zu reduzieren, um Ihr Unternehmen vor potenziellen Cyberangriffen zu schützen.
Dieses On-Demand-Webinar zeigt auf, wie es Ihnen durch ein Verständnis Ihrer aktuellen Sicherheitslage gelingen kann, Angreifern stets einen Schritt voraus zu sein. Sehen Sie sich dieses Webinar an, um sich ausführlicher über Folgendes zu informieren (auf Englisch):
- Herausforderungen bei der Sichtbarkeit der Angriffsfläche
- Wie Sie Ihr Unternehmen vor Cyberbedrohungen schützen
- Vorteile von Exposure Management
- Wie Sie Fallstricke bei der Navigation durch sich weiterentwickelnde Sicherheitsstrategien umgehen
Nicht jede „kritische“ Schwachstelle ist wirklich kritisch
Je größer die Zahl der Assets auf Ihrer Angriffsfläche, desto größer die Gefahr, dass Schwachstellen übersehen werden. Ohne Kenntnis all Ihrer Assets und der damit verbundenen Schwachstellen sinkt die Effektivität Ihrer Patch-Management-Prozesse rapide.
Dieses On-Demand-Webinar geht der Frage nach, wie Sie Reibungspunkte zwischen Ihren InfoSec- und IT-Teams verringern, um Ihre Cybersecurity-Lage zu verbessern. Sehen Sie sich dieses Webinar an, um sich ausführlicher über Folgendes zu informieren (auf Englisch):
- In welchen Fällen sind als „kritisch“ eingestufte Schwachstellen wirklich kritisch?
- Wie gängige Systeme zur Bewertung von Schwachstellen ein effektives Patching ausbremsen können
- Warum Sie die Kommunikationslücke zwischen Ihren Sicherheits-, IT- und Compliance-Teams schließen sollten
- Wie Behebungsmaßnahmen durch gestraffte Patching-Verfahren optimiert werden können
Proaktive Identifizierung und Behebung von Cyberrisiken
Viele Cybersecurity-Teams tun sich schwer damit, Cyberangriffe zu verhindern. Der Grund dafür ist, dass sie häufig mit Schwachstellendaten ohne jeden Kontext überschwemmt werden und ihnen der dringend benötigte Einblick in die Angriffsfläche fehlt.
Deshalb wissen sie oft nicht, worum sie sich zuerst kümmern müssen oder wie sie die Sicherheitsprobleme beheben können, die potenziell mit den größten Auswirkungen für das Unternehmen verbunden sind.
Auch die effektivsten modernen Sicherheitsteams müssen sich weiterentwickeln und von diesem reaktiven Schwachstellenmanagement-Ansatz zu einer proaktiven Exposure Management-Strategie übergehen. Dies beginnt mit dem Abbau von Silos, die Sicherheitsteams daran hindern, den umfassenden Einblick in die Angriffsfläche zu gewinnen, der notwendig ist, um Cyberangriffen stets einen Schritt voraus zu sein.
Ihre Angriffsfläche stets im Blick
Effektive, proactive Cybersecurity setzt Sichtbarkeit der Angriffsfläche voraus. Mit einer Exposure Management-Plattform erhalten Sie eine einheitliche Ansicht all Ihrer Assets auf der gesamten Angriffsfläche, sodass Sie damit verbundene Schwachstellen, Fehlkonfigurationen und andere Sicherheitsprobleme identifizieren können. Diese Informationen sind entscheidend, um nachzuvollziehen, wo Sicherheitsrisiken vorliegen, damit sie Prioritäten setzen und entsprechende Maßnahmen planen können.
Die eigene Exposure nachvollziehen
Es ist wichtig, sich über die eigene Exposure im Klaren zu sein, damit umsetzbare Entscheidungen zu deren Behebung getroffen werden können. Exposure Management kann zur Messung Ihrer aktuellen Sicherheitslage beitragen und Ihnen helfen zu bewerten, wie gut Ihre Teams kritische Sicherheitslücken aufspüren und wie schnell sie die Probleme beseitigen, die eine maximale Risikoreduzierung für Ihr Unternehmen bewirken. Durch Quantifizierung Ihrer Exposure sollten Sie in der Lage sein, Fragen wie die folgenden zu beantworten: „Wie sicher sind wir?“ und „Wo stehen wir bei unseren Maßnahmen zur Prävention und Risikominderung?“.
Angriffspfade visualisieren
Eine risikobasierte Bewertung unter Berücksichtigung von Asset-Kritikalität und Schweregrad der Bedrohung reduziert Fehlalarme um den Faktor 23:1 und priorisiert Remediation-Maßnahmen auf Basis der tatsächlichen Gefährdung für Ihr Unternehmen.
Risiken vergleichen
Durch Exposure Management erhalten Sie eine geschäftsorientierte Ansicht Ihrer Cyberrisiken. Beispielsweise können Sie KPIs einrichten, die im Zeitverlauf messen, wie gut Ihr Programm intern funktioniert, und Benchmark-Vergleiche der Programmreife mit ähnlichen Unternehmen der Branche anstellen. Dies unterstützt Sie dabei, das Sicherheitsprogramm und die Geschäftsziele Ihres Unternehmens aufeinander abzustimmen und die Kommunikation mit Führungskräften und wichtigen Stakeholdern zu verbessern.
Erleben Sie Tenable One in Aktion
Erzielen Sie umfassende Sichtbarkeit auf Ihrer modernen Angriffsfläche. Fokussieren Sie Maßnahmen auf die Verhinderung von wahrscheinlichen Angriffen. Treffen Sie datengestützte Sicherheits- und Geschäftsentscheidungen.
- Tenable One








